SAP Security Notes April ‘19: SAP Expands XXE Critical Patch to JAVA and HANA
SAP has released Security Notes for April and below is the Onapsis Research Labs’ analysis. This month SAP completed a patch release for a bug that Onapsis reported around an XML External Entity (XXE) vulnerability in SLD Registration that was previously patched for ABAP and XSA. SAP has included a new security note for SLD Registration in SAP HANA and updated the already released note to include JAVA. With the newly released note, the component can be updated and fixed in NetWeaver ABAP, JAVA and SAP HANA (as well as one entry point in SAP HANA XSA). Additionally, in April’s Security Notes, there is:
- An update for a well-known HotNews note with security updates for the browser control Google Chromium
- Two High Priority notes affecting SAP NetWeaver Process Integration and SAP Crystal Reports
- An SAP Security Note that patches a Missing Authorization Check for NetWeaver ABAP and S4/HANA.
XML External Entity Vulnerability now patched in SAP HANA
Last month’s blog post included details about SAP Security Note #2764283 for an XML External Entity Vulnerability in SAP HANA Extended Application Services, Advanced. Special attention should be paid to this critical vulnerability for its likelihood to be used in a targeted attack, based on its ease of exploitability and the potential negative impact to business continuity. If not patched, the vulnerability would allow an attacker to remotely access critical files from the server and steal any web app custom code (confidentiality). The attacker could also generate a Denial-of-Service (DoS) attack by stopping a Web App running on top of XSA, resulting in taking systems offline and making them unavailable (availability). This bug has a CVSS v3.0 of 8.7 and was found when researching SAP HANA XSA; however, the affected component is also present in other platforms. Based on this, SAP has released patches for other platforms, such as SAP Security Note #2729710 (originally released in February) and the recently released SAP Security Note #2772376.
Security Note #2729710 (CVSS v3.0 of 6.0) was originally released for SAP NetWeaver ABAP, but was updated this month with new ‘Symptom’ and ‘Solution’ information to include Java Server. Security Note #2772376 (CVSS v3.0 of 5.1) is a new SAP Security Note that includes the update for a secured and fixed SLDREG component for SAP HANA, including updates for both SAP HANA 1.00 and 2.00 (SAP HANA 2.0 SPS04 is not affected, so no need to patch).
A missing authorization check is more critical for XSA, since there is evidence that it could be remotely executed, but it should be properly patched in other platforms as well. Currently, we know that the attack can be executed locally, but further research may find other remote entry points that have not yet been discovered.
Missing Authorization Checks affecting SAP NetWeaver and S/4HANA
Missing authorization checks is one of the most common vulnerabilities in SAP software, representing about 15% of all SAP Security Notes. Today, a new patch has been released fixing three vulnerabilities reported by our lead researcher Matias Sena. SAP Security Note #2753629 (CVSS v3.0 of 5.5) “Missing Authorization Check for ABAP INST Function Module” was published as a Medium Priority and includes a fixed version of the affected module for both SAP NetWeaver and SAP S/4HANA, both on-prem and in the cloud.
As the title implies, some Missing or Improper Authorization checks were found on different ABAP functions that allow the management of RFC connections (enumerate, create, modify, activate or delete). Based on this, an attacker can potentially gather information about connections between SAP systems, disrupt communication between those systems (by deleting some of those RFC connections) or even perform a Man-in-the-Middle (MitM) attack (among others, see the Onapsis SAP Security Notes December ‘18 blog post for more details).
It is important to mention that even though the patch was published as Medium Priority, the bugs are similar to the one already patched in December (also reported by the same researcher), which was published as a High Priority note and maintained a CVSS v3.0 of 8.3.
Other HotNews and High Priority Notes
The only HotNews released this month is another update to the well-known note #2622660, “Security Updates for the Browser Control Chromium Delivered with SAP Business Client.” This is the third time this year that there is an update for this note (it has been updated eight times since it was first released in April 2018). This note addresses multiple vulnerabilities in the third-party web browser control Chromium, which is used in SAP Business Client and is periodically updated based on web browser updates. Since exploits for third-party tools are more common than exploits that are SAP-specific, which tend to be more targeted and selective, it is important to keep this note installed with every update to stay secure.
As for High Priority notes, SAP released #2687663 fixing a database information disclosure in Crystal Reports .NET SDK Webform Viewer. This is a developer tool used for report creation and business intelligence platform analysis. If you’re using this tool, we recommend that you patch it given that sensitive information, including credentials, can be included inside the disclosure.
Another digital signature spoofing vulnerability was found in SAP NetWeaver Process Integration (note #2747683). When this vulnerability is exploited, it could allow an attacker to get or modify critical information by sending arbitrary requests and XML documents that bypass server signature validation.
Summary and Conclusions
SAP published a total of 11 Security Notes in April and an additional three in late March. We recommend that you apply these critical SAP Security Notes (including two High Priority notes that affect many SAP customers) because of their important security implications.
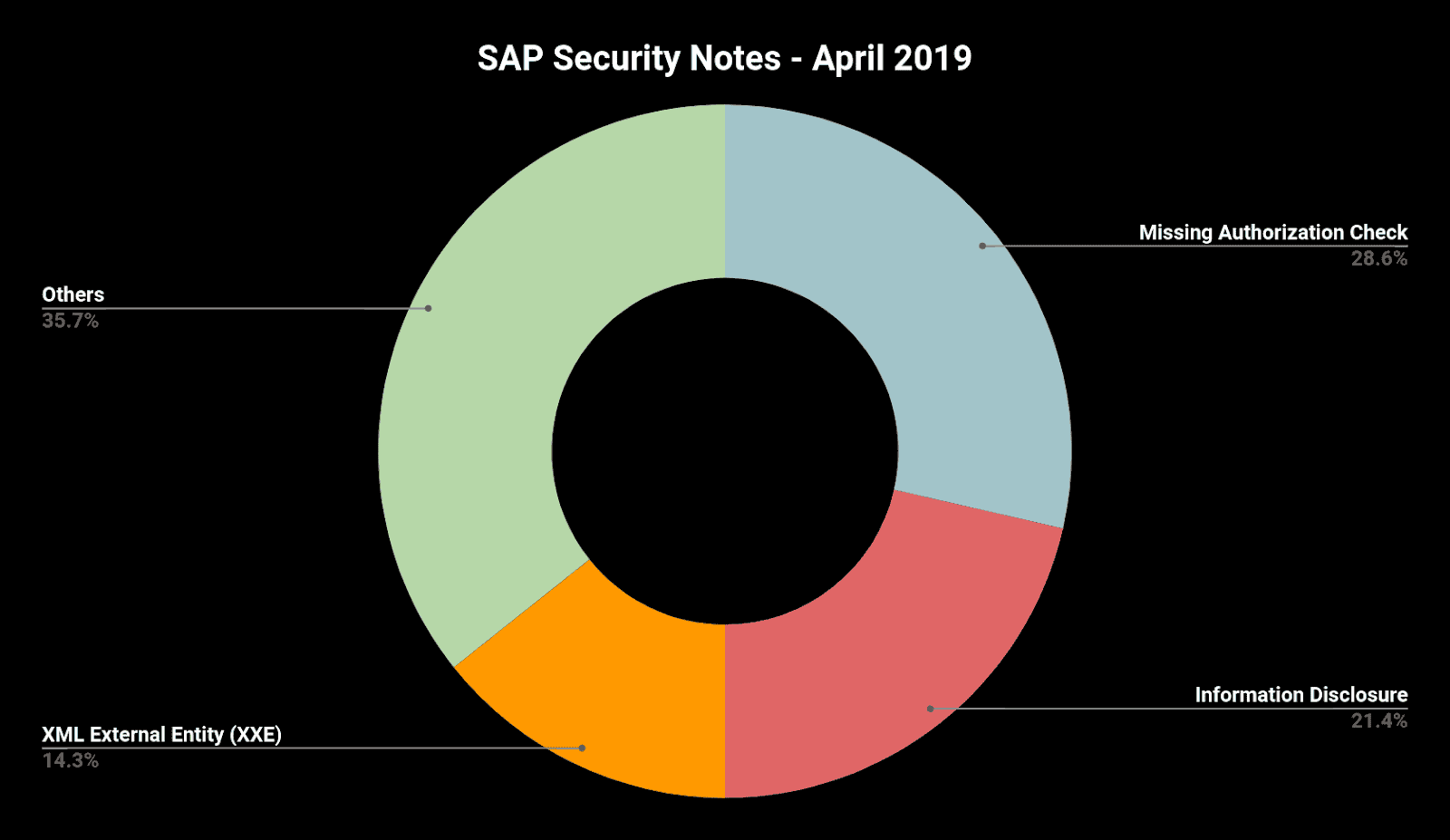
Below is a summary of the type of bugs SAP patched this month through its security notes:
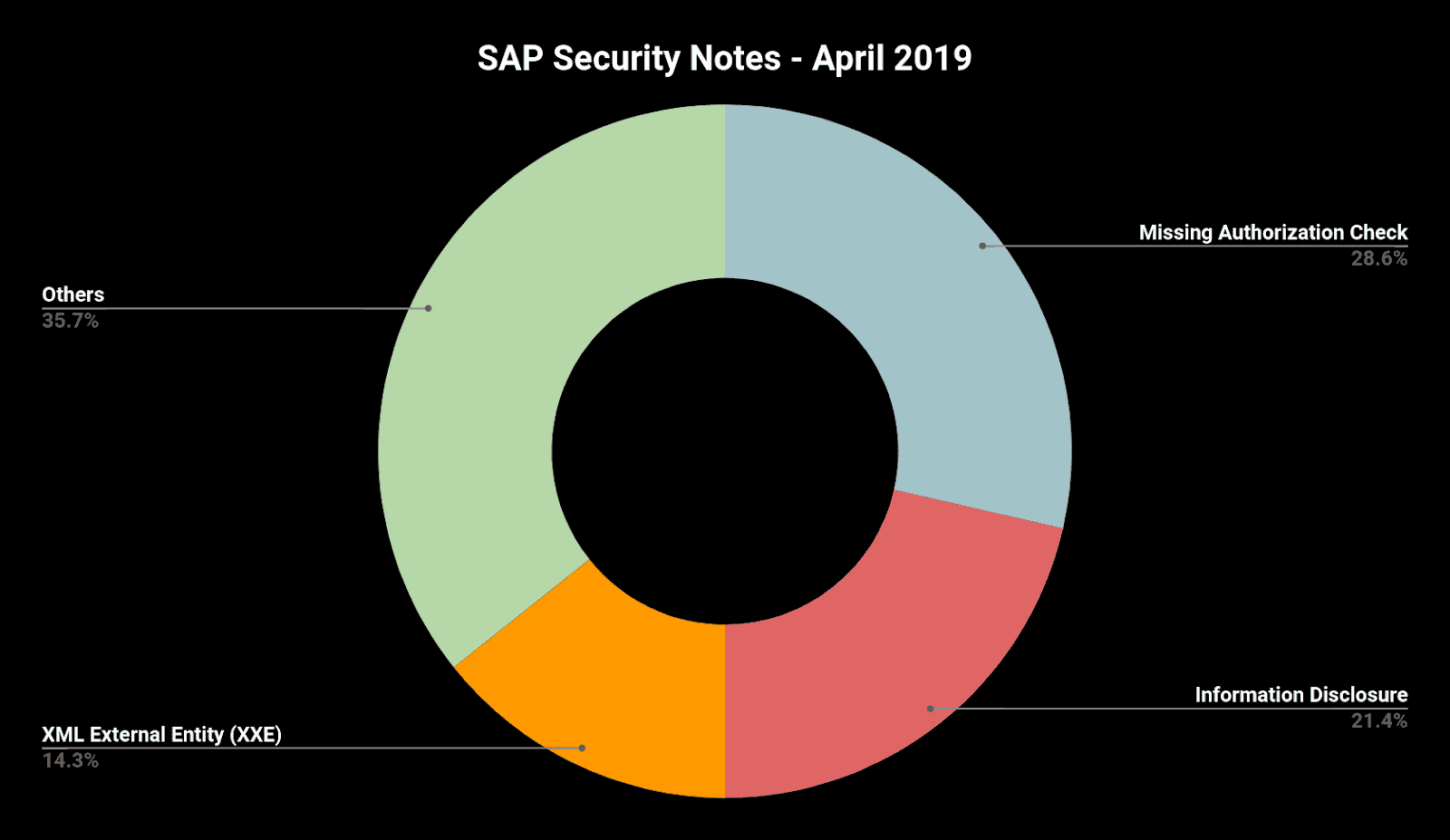
This month SAP recognized Onapsis researchers who have helped SAP improve the security and integrity of their customers’ systems. As we regularly do at Onapsis, we are working to update the Onapsis Security Platform to incorporate these newly published vulnerabilities. This will allow our customers to check whether their systems are up to date with the latest SAP Security Notes and will ensure that systems are configured with the appropriate level of security to meet their audit and compliance requirements.
Please follow our ERP security blog or follow us on Twitter for more information about the latest SAP security issues.
