SAP Security Patches April 2020: 5 HotNews and 29 Total Fixes for SAP Products

Highlights of April SAP Security Notes analysis include:
- April summary—29 new and updated SAP security patches released including 5 HotNews Notes and 5 High Priority Notes
- Onapsis helped with priority notes—The Onapsis Research Labs reported and helped SAP patch 6 of 10 Security Notes tagged as High Priority or HotNews
- Patches for several platforms—The most critical patches include fixes for platforms such as SAP Portal, SAP Commerce, Solution Manager (SolMan) and SAP Host Agent, among others
This month, SAP released 29 new and updated SAP Security Notes, the highest amount this year, after releasing 12 new ones in January and February and 22 last March. One-third of the released notes have been tagged as important ones, including five High Priority and five HotNews (which represents the first time since December 2014 this amount of HotNews notes were released in the same month). Six of these 10 SAP Security Notes were patched due to Onapsis reporting and helping, including fixes in platforms such as SAP Portal, SAP Commerce, SolMan and SAP Host Agent, among others. The Onapsis Research Labs is sharing its analysis of this month’s SAP Security Notes to help SAP customers properly prioritize, patch and therefore keep their systems secure.
HotNews fixes in several products, reported by Onapsis
SAP Security Note #2904480 titled, “Missing XML Validation Vulnerability in SAP Commerce”, has the highest CVSS of the ones released this month, 9.3 for CVE-2020-6238. SAP Hybris is an eCommerce Java-based platform that provides solutions for B2B and B2C commerce, among others. This vulnerability is present in SAP Hybris with a default configuration and exploitable by a remote unauthenticated attacker. It could potentially allow a malicious agent to read sensitive files and data from the system and even affect availability (in some limited scenarios). SAP has provided patches for both SAP Hybris on-prem implementations as well as SAP Commerce Cloud.
SAP Security Note #2896682 titled, “Directory Traversal Vulnerability in SAP NetWeaver (Knowledge Management)”, is one of the four notes with a CVSS of 9.1 released this month and tagged as HotNews. It is also the second new patch developed by SAP with Onapsis reporting and helping. Identified as CVE-2020-6225, this vulnerability is a Path Traversal present in SAP NetWeaver Knowledge Management, which is a centralized access point for distributed repositories of files along the systems. It lets users navigate through folders, create, delete files, etc. In all these functionalities, a user can upload files. If unpatched, the system does not sufficiently validate input and therefore may allow a potential attacker to overwrite, delete or corrupt arbitrary files on the remote server.
SAP also released Security Note #2839864, which replaces the corrections already published in Security Notes #2808158 and #2823733. All of these notes provide improved fixes to vulnerabilities reported by Onapsis for Operating System (OS) Command Injection in SAP Diagnostics Agent. In this latest update, SAP updated the ‘Attachments’ section adding a correction in one of the files attached to the note. If you want to better understand the scope and severity of this vulnerability, you can read our July 2019 blog post where we first explained this vulnerability after it was patched, or our September 2019 blog post when SAP improved the fix to cover other scenarios. We can confirm that this latest update is a minor one, that improves attachments for customization of the protection after the patch. Customers who have applied the March fix are protected against critical exploitation of this vulnerability.
High Priority Note fixes in SolMan and SAP Host Agent reported by Onapsis
Onapsis also collaborated with SAP and reported three of five High Priority notes patched today, which includes another authentication bypass in SolMan and several escalations of privileges vulnerabilities.
SAP Security Note #2906994 patches a vulnerability identified as CVE-2020-6235 with a CVSS of 8.6. It fixes a missing authentication check in SAP SolMan, which may allow an attacker to read sensitive information or even access administrative or other privileged functionalities abusing the lack of an authentication check-in a component. This vulnerability, despite being a little bit less critical (CVSS vector-only affects confidentiality), has some similarities with the one patched in SAP Security Note #2890213, HotNews that was previously explained in our March 2019 blog post. Both vulnerabilities allow an unauthenticated attacker to get privileged access to SolMan and, combined with other vulnerabilities, post-exploitation alternatives include critical scenarios for affected customers if attacked.
Finally, SAP also released this month two Security Notes which fix Privilege Escalation vulnerabilities in SAP Landscape Management (#2902456) and SAP Host Agent (#2902645), both tagged as High Priority with CVSS scores of 7.2. Both patches protect SAP customers to avoid potential attackers with admin privileges in the system escalating to root privileges in the operating system layer.
Other Critical SAP Security Notes in April
One SAP solution that is affected above average by April’s Patch Day is SAP BusinessObjects. There are eight SAP Security Notes for this solution, covering various types of vulnerabilities, and three of them are rated as critical:
HotNews Note #2863731 describes the possibility of a remote command execution caused by a deserialization attack in SAP BusinessObjects Business Intelligence Platform. Parameters of a specific component can be manipulated in order to inject deserialized content. The provided fix enables data encryption for the traffic between client and server so that it can no longer be read. SAP has rated this vulnerability with a CVSS of 9.1.
Another part of the above mentioned specific component is also involved in the vulnerability described and fixed with the updated High Priority Note #2861301. While this vulnerability also allows the remote execution of code with an even higher impact on the application’s confidentiality and integrity, unlike #2863731, this vulnerability requires user interaction. The latter fact leads to a CVSS of 8.1, and thus, to High Priority.
SAP Security Note #2898077 is the second High Priority Note for SAP BusinessObjects on today’s Patch Day and fixes an Information Disclosure vulnerability. A non-authenticated user could exploit this vulnerability with CVSS of 7.5 in a certain web application of SAP BusinessObjects in order to gain information that can be then used for further exploits and/or attacks.
HotNews Note #2900118 completes the set of critical notes that were released in April. It fixes a Code Injection vulnerability in SAP OrientDB 3.0. SAP OrientDB is a multi-model, graph-based, no-SQL database that SAP acquired from Callidus Software Inc. in 2018. Because an attacker requires authentication and script execution privileges, the vulnerability is rated with a CVSS of 9.1.
Summary & Conclusions
Taking into account SAP Security Note #2863396 titled, “Remote unauthenticated log injection in SAP BusinessObjects Business Intelligence Platform”, and tagged as Medium Priority, the Onapsis Research Labs has once more significantly contributed to SAP’s April Patch Day by contributing to six total fixes. Hence, SAP acknowledged five Onapsis researchers on its webpage, which values constant collaboration with researchers all over the world.
Given the impressive number of fixes (29) for multiple SAP products—including five HotNews and five High Priority Notes—this month’s notes should be carefully addressed and properly prioritized for the most critical ones.
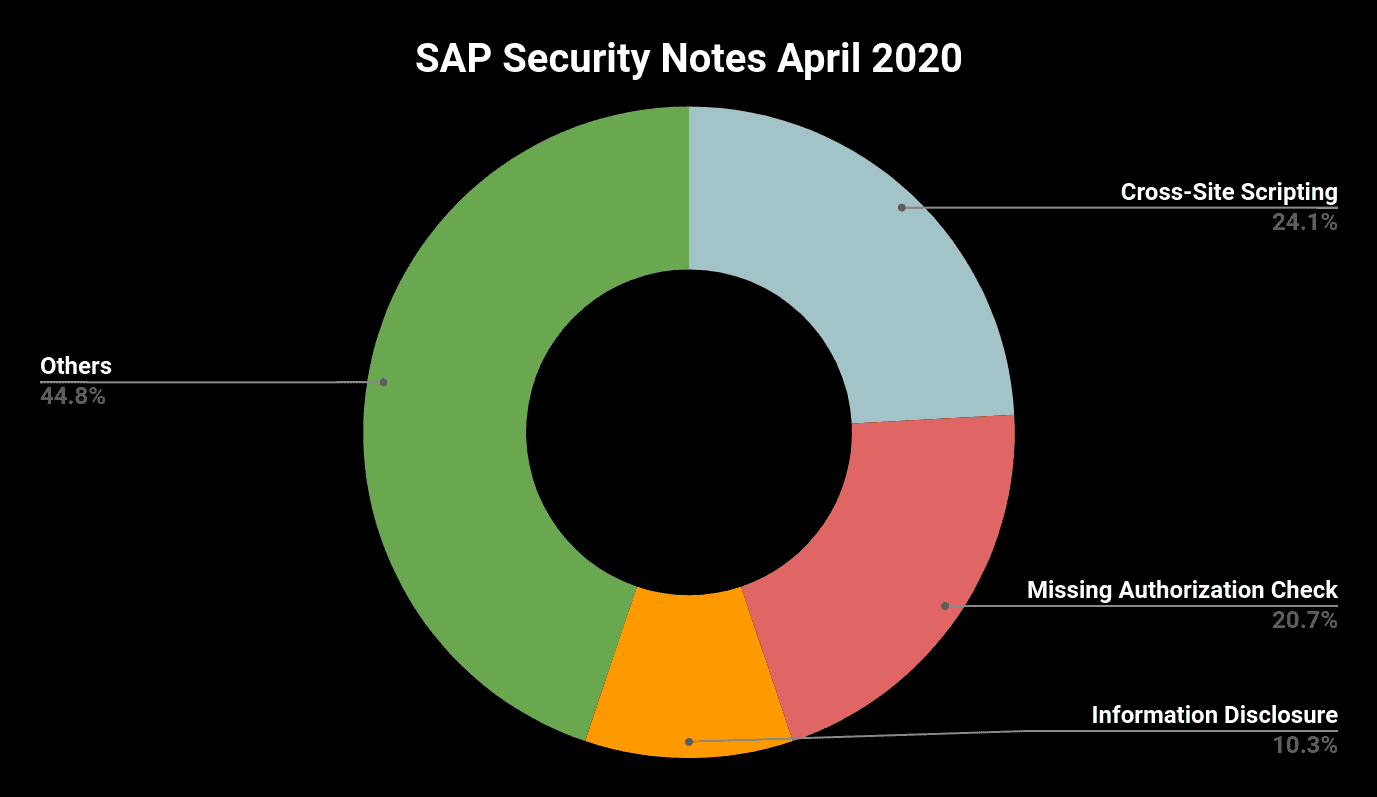
Finally, with seven reported Cross-Site Scripting and six Missing Authorization vulnerabilities in various SAP software products, these two categories represent once more the majority of the published issues:
As always, the Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.