SAP Security Notes March ‘19: Critical Bug Affecting SAP HANA XSA
Every second Tuesday of the month SAP releases its monthly security patches, better known as SAP Security Notes, now available to customers through Launchpad or SNOTE transaction. Today, SAP published 15 new security notes, including five that were discovered by our researchers. No HotNews notes were released today, but two High Priority were highlighted as a result of Onapsis Research Labs reports. SAP Security Note #2764283, the higher CVSS of the day, patches a critical vulnerability (XML External Entity) in SAP HANA extended application services advanced (XSA), a bug that can lead to critical compromise of data confidentiality. The other High Priority note, #2689925, patches a classic cross-site scripting (XSS) vulnerability in SAML 1.1 SSO Demo Application in SAP NetWeaver Java Application Server.
Before getting into details, it’s important to mention that in the latter-half of February, after the Patch Day that month, SAP re-released the well-known HotNews note #2622660, titled, Security Updates for the Browser Control Chromium Delivered with SAP Business Client. SAP has regularly updated this since it was first launched in April 2018 or any time there’s a new third-party bug for these used components. Remember, we can’t forget about these notes, since the exploit of these third-party tools could have a bigger impact than even specific exploits to SAP, which tend to be more targeted and selective.
XML External Entity Vulnerability in SAP HANA XSA
As mentioned before, the patch with the highest CVSS score this month is the one published in SAP Security Note #2764283, titled, XML External Entity Vulnerability in SAP HANA Extended Application Services, Advanced, with a CVSS score v3 of 8.7 / 10.
This security bug was found during researching SAP HANA XSA. Even though the vulnerability affects a kernel component present in every SAP system (patched in February in SAP Note #2729710), Onapsis researchers found a way to exploit it in SAP HANA XSA and, therefore, reported it. This month, SAP properly patches and solves its exploitation entry point in this platform.
Onapsis researchers’ original report explains that through an administrator interface of the XSA controller, which allows a user to send an XML file, this bug could be exploited, leading to critical scenarios affecting confidentiality (arbitrary files retrieval from the server) and availability (denial-of-service [DoS] conditions in successful exploits). This specific entry point, present in XSA and found by our researchers as a way to exploit the vulnerability, is normally used to send technical specifications from the registered SAP system to the SOLMAN inventory, such as CPU consumption, installed software components, etc. By abusing this vulnerability, an attacker would be able to send a specially crafted XML payload. Although this endpoint needs the credentials of the lm_service user, a user with access to them will be able to use this service.
Availability is affected since the XML External Entity (XXE) vulnerability, in general, contains something called an XML Entity Bomb. This attack is a piece of XML code, syntactically valid and correct, that could store entries to references which refer to other references (generating a loop) and nested data entities start growing exponentially and can result in a DoS.
This bug, found by Onapsis researchers Pablo Artuso & Nahuel D. Sanchez, is part of their presentation next week, in Germany, at the upcoming Troopers Conference. They will provide a talk titled, “Dark Clouds Ahead: Attacking a Cloud Foundry Implementation,” showing how through combining several vulnerabilities in SAP HANA, even ones that are not tagged as HotNews, attackers can get critical access to the system.
Onapsis Reported Vulnerabilities Fixed in Netweaver Kernel, SAP Java Server Netweaver, SAP BusinessObjects and SAP Work Manager & SAP Inventory
There is a second patch tagged as High Priority this month, also reported by one of our researchers. SAP Security Note #2689925 corrects a bug in SAML 1.1 SSO Demo Application in SAP NetWeaver Java Application Server – not properly encoding user-controlled input to result in a cross-site scripting (XSS) vulnerability. If successfully exploited, temporary defacing or authentication information stealing are some of the potential impacts of this vulnerability.
On the other hand, SAP Security Note #2729710, the one we discussed in last month’s blog post, was re-released, with a lower CVSS than originally published. The note, titled XML External Entity (XXE) Vulnerability in SLD Registration of ABAP Platform, was originally published as a High Priority note with a CVSS score v3 of 8.6 / 10 and is reduced to a Medium Priority Note with CVSS score v3 of 6.0 / 10. This is because the attack vector was reduced to local because the remote attack presented as a proof of concept by our team was affecting only SAP HANA XSA (see previous section). Even though it might be possible to exploit it, there is no evidence and SAP properly reduced this value. Based of our findings in SAP HANA XSA, it may still be critical and we recommend to patch it as soon as possible. SAP also explained in its new release that, “There is no action required from customer side if the note is already implemented.”
As you may already know, the Onapsis Research Labs has been putting special focus on the SAP BusinessObjects platform for many months. As a result of our continuous efforts on this platform, we reported another security bug that leads to this month’s Medium Priority publication that fixes a vulnerability in the XML parser of SAP BusinessObjects. SAP Security Note #2689259, titled SAP BusinessObjects: Improper Restriction of XML External Entity Reference, fixes a vulnerability in Central Management Console (CMC), which is included over the Business Intelligence (BI) platform. This vulnerability exists when an XML parser resolves External Entities during XML analysis, without restrictions on accessed resources. By abusing this vulnerability, an attacker would be able to read system files, list directories content or perform a DoS from a remote system. Basically, everything with the privileges of the operating system user called <sid>adm.
The second Medium Priority note reported by the Onapsis Research Labs (#2753497) fixes a DoS vulnerability in two mobile apps: SAP Work Manager and SAP Inventory Manager, which were discussed deeply in our previous blog post. These apps contain a vulnerable method that does not properly check the input and could make them crash. In order to patch this bug, customers are required to upgrade to SAP Mobile Platform SDK 3.1 or later. Lastly, but no less important, iOS and Windows desktops are not affected.
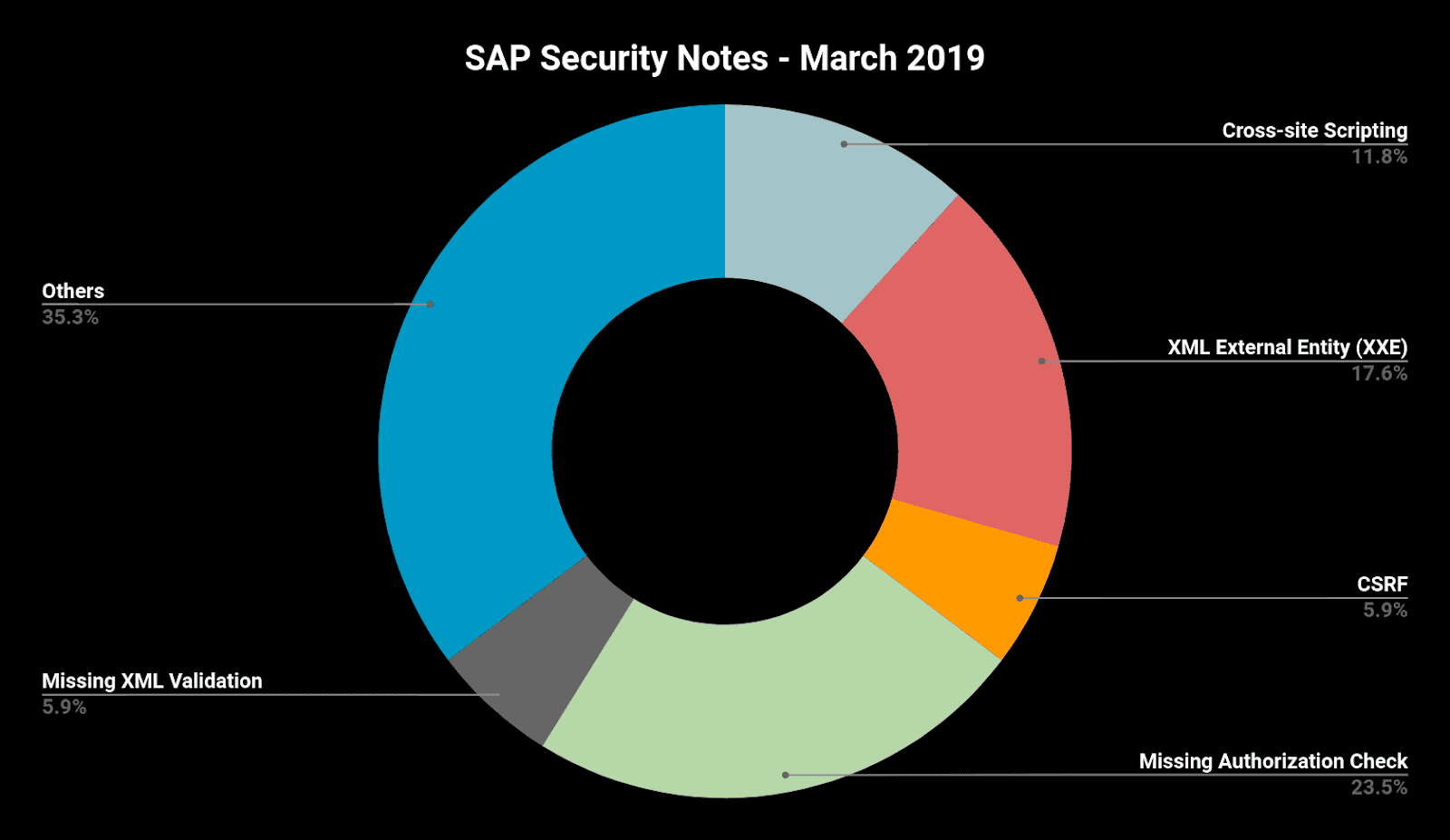
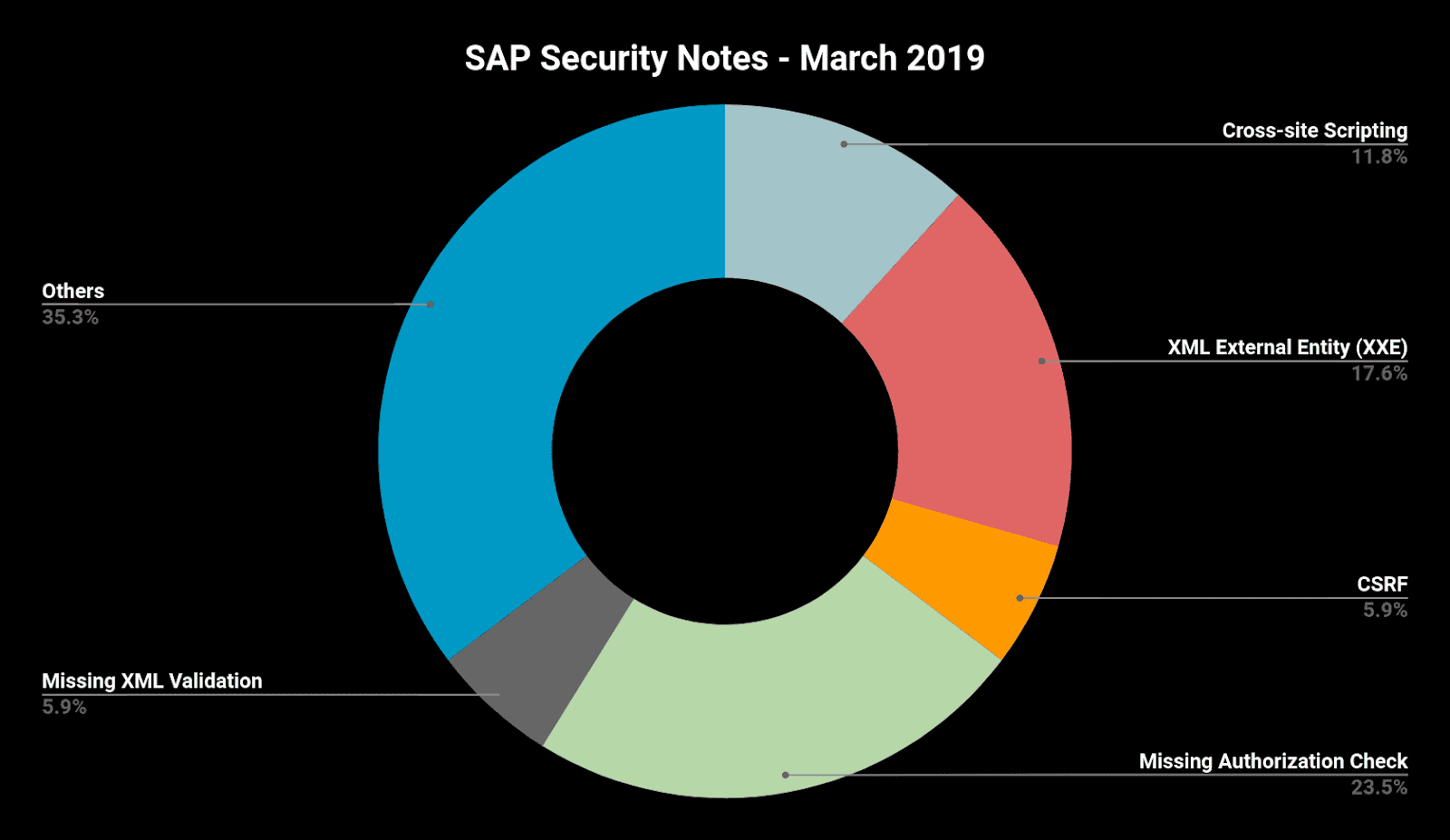
Below is a summary of the type of vulnerabilities that were fixed this month, including not only 15 SAP Security Notes, but the other two that were published later in February after the Patch Day.
As you may see in the SAP acknowledgment to Security Researchers, Onapsis is the only company with several researchers on this page. Four of our team members have been recognized this month based on their findings and reports. As always, we are working to update the Onapsis Security Platform to incorporate these newly published vulnerabilities to allow our customers to check whether their systems are up to date with the latest SAP Security Notes. Follow us on Twitter to keep tracking ERP Security News and continue to read our ERP security blog.
