SAP Security Notes July ‘19: Critical Vulnerability Affecting Solution Manager
Highlights of July’s SAP Security Notes analysis include:
- Hot News SAP Note in Solution Manager Diagnostic Agent—the only Hot News released during July’s Patch Day fixes a critical vulnerability that may allow an attacker to compromise the entire SAP system.
- High Priority Note in ABAP NetWeaver Process Integration—the second-highest priority SAP Security Note released this month fixes a serious vulnerability in eCATT, which can lead to a critical impact to the SAP system.
- Security notes reported by Onapsis Research Labs—In addition to the released Hot News note, SAP fixed other vulnerabilities reported by the Onapsis Research Labs affecting Diagnostic Agent, BusinessObjects platform and Hybris Commerce.
Hot News SAP Note in Solution Manager Diagnostic Agent
As part of our commitment to SAP security research, we have been providing information about Solution Manager (SolMan) for several months now. This month SAP released the fifth Hot News note of 2019, fixing a vulnerability in the SolMan Diagnostic Agent (SMDAgent), which manages the monitoring and diagnostics events communications between every SAP system and Solution Manager.
Using its basic functionality, a SolMan admin can execute OS commands through a GAP_ADMIN transaction, in order to perform analysis into an SAP system. Once executed, those commands are validated using a whitelist file located in the SMDAgent installation directory. This vulnerability may allow an attacker to bypass this validation by sending a custom-crafted payload. Using this technique the attacker could obtain full control over an SAP system compromising the SMDAgent user, allowing access sensitive information (such as credentials and critical business information), changing application configurations or even stopping SAP services. As previously mentioned, the SDMAgent must be installed in every SAP system in order to perform diagnostic tasks, so the scope of an attack is broad, as it could affect the entire landscape.
Due to the high impact on confidentiality, integrity and availability, added to the low complexity of an attack, note #2808158 (CVE-2019-0330), reported by our researcher Yvan Genuer, was released with a CVSS score of 9.1.
To stay protected from this vulnerability, be sure to install the respective patch corresponding to the version of Solution Manager you are using. After restarting, every SMDAgent will be reconnected and upgraded.
High Priority Note in ABAP NetWeaver Process Integration
The Extended Computer Aided Test Tool (eCATT) is a commonly used tool to cover automatic testing in SAP business processes. Its main purpose is to create and execute functional testing about transactions, reports, scenarios, authorization checks, etc. As the only SAP Security Note tagged High Priority, with a CVSS score of 8.7 (CVE-2019-0328), note #2774489 fixes a code injection in eCATT. Exploitation of this vulnerability has a critical impact on the system’s integrity and availability since malicious commands that could be executed run with a high privileged user. Just as in the Hot News patching process, this could be fixed by upgrading the affected Support Package, or implementing the correction instructions attached in the mentioned note.
Security Notes Reported by Onapsis Research Labs
Three Medium Priority Security Notes reported by the Onapsis Research Labs were released by SAP today.
SAP Security Note related to BusinessObjects. Several cross-site scripting (XSS) vulnerabilities affecting the Performance Management (PM) component were fixed in Security Note #2764733. An attacker could send a malicious crafted URL to an already authenticated user in order to steal session information. Depending on which user is affected, administrative system access is at risk. This note was released with a CVSS score of 6.1 (CVE-2019-0326).
SAP Security Note related to Solution Manager. In addition to the Hot News security note released, #2738791 with a CVSS score of 5.3 (CVE-2019-0318) fixes the exposure of SMDAgent user credentials in system log files. Even though these files were encrypted, an attacker could easily obtain the key.
SAP Security Note related to SAP Hybris commerce. The third vulnerability, fixed in note #2781873, allows a malicious user to perform a denial of service (DoS) attack by stopping Hybris service through its JMX interface. Upgrading to a patched version will disable remote access to that interface for new implementations, but in order to mitigate this vulnerability in those SAP Commerce instances already set up, the user must perform an additional configuration detailed in the mentioned note.
Summary and Conclusions
A total of 20 SAP Security Notes were released during July’s Patch Day. The chart below summarizes the types of vulnerabilities, which include: OS Command injection, Missing Authorization Check, Cross-Site Scripting and Directory Traversal.
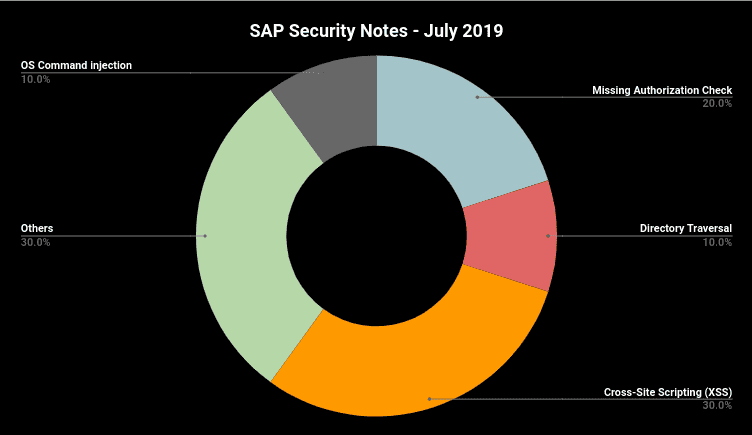
Something very important to mention is that the most critical vulnerabilities fixed this Patch Day can be mitigated maintaining system components properly patched. You can find support and assistance by running a vulnerability and compliance check with Onapsis‘s Missing Notes Module capability.
As a result of our team performing security research and sharing knowledge with the community-at-large, SAP continues to give monthly recognition to the Onapsis Research Labs. Researchers specifically mentioned include Yvan Genuer, Gaston Traberg, Nahuel Sanchez and Juan Pablo Perez-Etchegoyen.
As we regularly do at Onapsis, we will continue to publish our SAP Security Notes Patch Day analysis blog post every Patch Tuesday and work to update the Onapsis Security Platform to incorporate these newly published vulnerabilities. This will allow our customers to check whether their systems are up to date with the latest SAP Security Notes and will ensure that those systems are configured with the appropriate level of security to meet their audit and compliance requirements.
For more information about the latest SAP security issues and to stay in tune with our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.
