SAP Security Notes July 2017: Patched Denial Of Service Vulnerability affecting all SAP Platforms
Today is the the second Tuesday of July and as our readers already know that today SAP released its monthly Security Notes. Here is our monthly report on how to improve your ERP security and take care of your most critical information. Today SAP released 16 new security notes, summing up to a total of 23 taking into account the ones published after second Tuesday last month. For the third month in a row there aren’t any notes tagged as Hot News. However, a few are tagged as High Priority and should be patched as soon as possible, especially since one of them directly affects SAP availability.
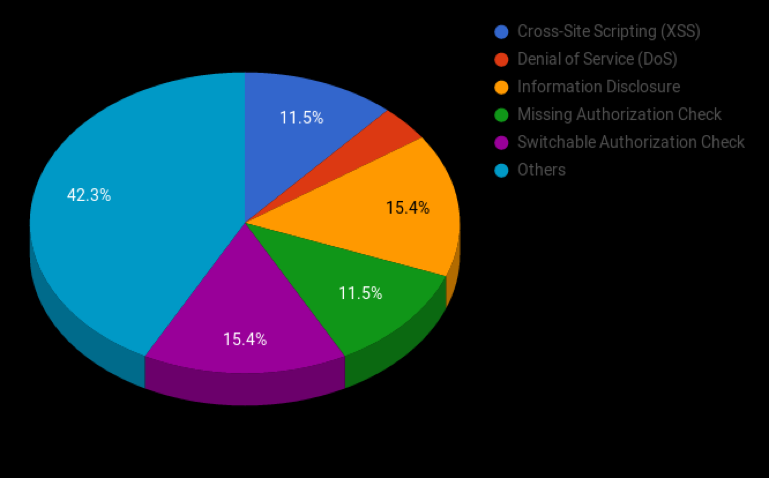
The above graph shows this month’s distribution of published vulnerabilities.
Malicious SAP Host Agent Shutdown without Authentication
SAP Host Agent is an agent that performs several management tasks, such as operating system and database monitoring, SAP instance discovery, inventory and provisioning, and several others. This patched vulnerability, could allow an attacker to remotely restart SAP Host Agent without authentication. SAP Security Note #2442993 is one of the two most high risk bugs this month, tagged as CVSS v3 Base Score: 7.5, having direct and high impact on availability.
The vulnerability, discovered by Andres Blanco and Nahuel Sanchez from Onapsis Research Labs, allows an attacker to restart SAP Host Agent without authentication, through a specific crafted SOAP request. Consequently, management functions would now be out of service. If other scheduled jobs need these web services for regular processes, those jobs will subsequently fail. Depending on your business architecture, this could lead to more critical availability or performance issues on the system.
All SAP Host Agent versions up to 7.21 PL24 are affected. This means that all Netweaver based applications and both HANA 1 and HANA 2 are affected. This not only increases the probability of being attacked, but the need for patching as quickly as possible.
After Onapsis worked closely with SAP on the details of the vulnerability, the issue is now fixed in SAP Host Agent version 7.21 PL25. To patch in SAP HANA, users can directly upgrade to the following revisions (or later versions) where SAP Host Agent is already included in its patched version:
- Revision 122.10 (for SAP HANA1.00 SPS12)
- Revision 2.02 (for SAP HANA2.0 SPS00)
- Revision 12 (for SAP HANA2.0 SPS01)
For non-HANA systems, SAP Security Note #1031096 describes the procedure to upgrade SAP Host Agent to it latest version. The upgrade basically implies downloading it from service market place and properly executing it with the -upgrade parameter.
Finally, since the vulnerability can be triggered through the SAP Host Agent web service, SAP Security Notes #1439348 and #927637detail manual steps in order to protect additional web service methods with proper authentication. To restart all sapstartsrv is needed to activate the changes. As the same notes describe, to restrict network access to the specific ports to a minimum level required for operation is another workaround to minimize the chances of being exploited.
High Priority Notes details
In addition to the aforementioned high priority note, there are three more notes that deserve attention due to their high level of impact. We will discuss them in order of descending severity, as expressed by CVSS score. Two notes, including the one with greatest severity, concern missing authorization checks. The third concerns a cosmetic update to the SAP note web page, but should nevertheless be regarded this month.
- Missing Authentication checks in SAP Point of Sale (POS) Retail Xpress Server (#2476601): The absence of a check for authentication leaves your SAP Xpress Server exposed to a possible attacker being able to reach it through the network, which could be the Internet. This note concerns a complex attack at its core. However, a smart attacker can operate silently and independently. Putting the confidentiality, availability and integrity of your data at the highest risk. The patch of the note is manual, although its web page might indicate differently.
CVSS v3 Base Score: 8.1 / 10 - Improved security for outgoing HTTPS connections in SAP NetWeaver ( #2416119):
This note was initially published in March and has received multiple cosmetic updates to its web page since. We discussed this note in our blog post last month, and this month the updates to the note are again cosmetic only. Due to the high severity of this note we recommend to use this update as a reminder to patch the note as soon as possible, if not yet performed. Manual steps are involved after patch installation, so be aware of usability issues if the certificates are not properly configured before implementation.
CVSS v3 Base Score: 7.4 / 10 - Missing authorization-check in BC-SRV-ALV (#1854252): This note also concerns an update, although not cosmetic like the previous note discussed. The patching of this note, together with automatic steps, requires a manual pre-implementation step. The note update for this month has added an additional software component release version to the list of releases requiring the pre-implementation step. Although this vulnerability has the lowest CVSS score in the list, exploiting it is easier than the others. Patching therefore is still recommended. Don’t forget to check if the updated release version applies to you.
CVSS v3 Base Score: 6.0 / 10
Another bug reported by Onapsis Research Labs was published this month in SAP Note #2459319 (Weak encryption used in SAP Netweaver Data Orchestration Engine). Onapsis researcher Pablo Artuso found this vulnerability as part of our SAP For Defense analysis at the end of 2016. This note contributes to a total of 14 SAP notes published by SAP in response to over 40 vulnerabilities found by Onapsis Research Labs as part of SAP For Defense. Our blog post from May of this year provides a review on SAP For Defense patched bugs.
Finally, this month only 43% of notes require no manual steps besides note installation. Installing these notes is easier than the other ones and patching them has direct impact on information security. This percentage is lower than the average (usually between 60% and 75%) so this means this month’s users should perform more manual steps to have better coverage of patches in their environments.
As usual, our researchers who help SAP improve their security are properly acknowledged on the SAP Webpage this month. Onapsis Research Labs is already in the process of updating our Onapsis Security Platform to incorporate these newly published vulnerabilities into our product. Stay tuned for more information about SAP Security and do not hesitate to communicate with us if you have further questions about how to protect against the attacks of this month.



