SAP Security Notes June 2017: Information Disclosure and Denial of Service
As with the second Tuesday of every month, today SAP released its monthly Security Notes to keep your SAP infrastructure secure. This month, SAP published 18 new security notes, and released 11 security notes that were published after May 9th (last patch tuesday), totaling 29 notes that will be analyzed in this post. For the second month in a row there aren’t any notes tagged as Hot News; the most critical risk category that SAP has catalogued for newly discovered vulnerabilities. This month however, there are five ‘high risk’ security notes that should be taken into account for prioritization.
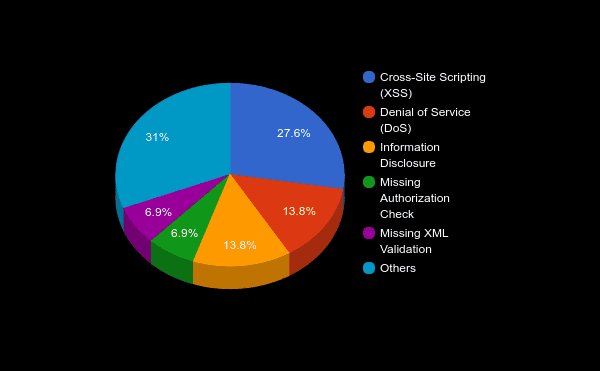
It is important to note that most of this month’s notes (more than 80%) are automatic, meaning there are no manual steps that need to be performed after installation. These notes are easier to implement than the manual ones, so one can take this into account for prioritization. Below is a detailed list breaking down the various types of vulnerabilities reported this month:
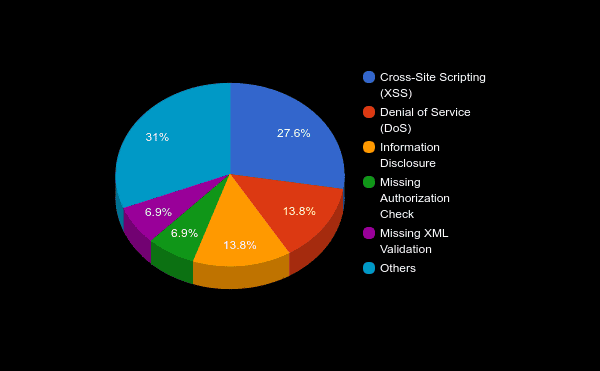
Bugs Reported by Onapsis: Confidentiality & Availability of Risk
This month, SAP patched six vulnerabilities reported by the Onapsis Research Labs, and grouped them in three SAP Security Notes. All of these vulnerabilities affect information confidentiality and availability. Our research team discovered them during a deep dive analysis of SAP Message Server, a protocol/service that is present in all SAP Systems. We initially researched the SAP Message Server due to the impact a bug would have have on this service as any SAP implementation may have this service enabled.
The first couple of bugs, solved in SAP Security Note #2445033 titled “Information Disclosure in SAP NetWeaver Message Server,” directly affect confidentiality. By sending custom packages, an attacker could retrieve information about the configuration of the SAP Message Server. Despite the fact that Information Disclosure bugs are not critical ones, they could be used as a first step towards targeted attacks; the type of attacks that big companies should be protected against. In other words, an information disclosure bug in other types of software (not business critical applications) could have less impact as part of a bigger attack than in this scenario.
In a second note, #2445071 titled “Denial of service (DOS) in SAP NetWeaver Message Server,” an attacker could directly impact availability using the same resource: by sending customized packages. In this case, as the name of the note indicates, the attack could not only lead to a Denial of Service attack in the statistic level of Message Server, but could also lead to the modification of specific parameters in the same service that is part of the monitoring and administrator tools of SAP Message Server. In this note, SAP grouped three bugs, reported by Onapsis, that allow the same type of attack with different parameters.
Finally, there’s a third note that has been reported by our team, #2425129, “Missing XML Validation vulnerability in SAP Note Assistant.” In this note, SAP included restrictions for external references for XML files in SAP Note Assistant, that can lead (without proper protection) not only to file retrieval (confidentiality) but in some cases, can also lead to Denial of Service attacks.
Our researchers Andrés Blanco, Nahuel D. Sánchez, Martin Doyhenard and Alejandro Burzyn were acknowledged on the SAP Webpagethis month. We are very proud of their hard work discovering new bugs and quickly reporting them to SAP in order to help keep ERP systems secure.
High Priority Notes Details
As previously mentioned, this month there are five ‘high priority’ security notes that should be prioritized as they have a greater impact (usually expressed through a bigger CVSS score) on overall security posture. Two of them are related to Denial Of Service attacks, another two are related to HTTPS security, and the third is a Cross Site Scripting bug. Here’s a prioritized list of these notes:
- Denial of service (DOS) in BILaunchPad and Central Management Console (#2313631): Both services can be exploited, generating a Denial Of Service Attack in the servers, tagged like this due to its high impact in availability.
CVSS v3 Base Score: 7.5 / 10 - Denial of service (DOS) in SAP NetWeaver Instance Agent Service (#2389181): Same type of bug and conditions as the previous one, but affecting another service.
CVSS v3 Base Score: 7.5 / 10 - Improved security for outgoing HTTPS connections in SAP NetWeaver (#2416119): This note is an update of a March publication that includes more information on how to properly configure HTTPS connections securely. It’s worth mentioning that this is a manual note that includes specific manual steps after patch installation. As a result, this could lead to usability issues if the certificates are not properly configured before implementation. This is the second month that SAP has published information about this note so we strongly recommend it be patched as soon as possible.
CVSS v3 Base Score: 7.4 / 10 - Cross-Site Scripting (XSS) vulnerability in SAP BusinessObjects Web Intelligence HTML interface (#2396544): As with any XSS bug, if the note is not installed it does not sufficiently control user inputs, resulting in client-side attacks. Despite XSS bugs are usually not critical, this one has high impact in confidentiality, which increases its CVSS Score.
CVSS v3 Base Score: 7.1 / 10 - Missing certificate verification in CommonCryptoLib (#2444321): Finally, there’s another note related to HTTPS certificates validation. In this case, it’s through a third-party tool. This is a manual note that can be solved through the installation of the fixed version of the software that is available in SAP Software Downloads. As with the related bug, after proper installation there could be some issues if there are no trusted certificates installed.
CVSS v3 Base Score: 7.0 / 10
As always, our team is already in the process of updating our Onapsis Security Platform to incorporate these newly published vulnerabilities. This will allow you to check whether your systems are up to date with these latest SAP Security Notes, and will ensure that those SAP systems are configured with the appropriate level of security to meet your audit and compliance requirements.
