SAP Security Notes May 2017: Military and Defense Solutions
As with the second Tuesday of every month, today SAP released its monthly Security Notes to keep your SAP infrastructure secure. This month, SAP published 14 new Security Notes with only one note tagged as High Priority. However, of these 14 notes, four of them are updates to previous publications. Based on the number of fixed vulnerabilities, and the criticality of each, it’s safe to say that this is not a critical patch day for SAP compared to previous months.
Additionally, SAP released 3 more notes in April after their April Notes release, totaling 17 patched bugs that we will be reviewing. Of these, the most common are Missing Authority Check (6) and Cross Site Scripting Attacks (5) and one additional note for each of the following attacks: Missing XML Validation, SQL Injection, Denial of Service (DoS), Memory Corruption, Clickjacking and Insufficient logging.
15 notes were tagged as ‘medium priority’, and one was tagged as ‘low priority’. The only ‘high priority note’ of the month is not a vulnerability directly in the SAP platform, but a bug that exists in a library that is being used by SAP. This note is #2380277 titled “Memory Corruption Vulnerability in IGS,” and details how an attacker can update a library component that is being used by Internet Graphics Server (IGS). This bug has been vulnerable for the last year. However, despite that the bug has been present for a while, it is pretty easy to solve and there aren’t any reports detailing that it has been widely exploited in the wild. Other software companies such as Oracle and RedHat had the same library and updated it in 2016.
Finally, all but one of the published notes are automatic ones. That means that these notes will have automatic effect after installing, there’s no need to perform manual steps or additional checks. The only SAP Note that has manual steps is note #2142551 ‘Whitelist Service for Clickjacking Framing Protection in AS ABAP.’ This note was originally released in 2016 and was analyzed in detail in our blogpost “Clickjacking SAP Security Notes: Where to start?.” Here, you can find more details on how to properly set up a clickjacking security framework over SAP.
SAP For Defense in Review
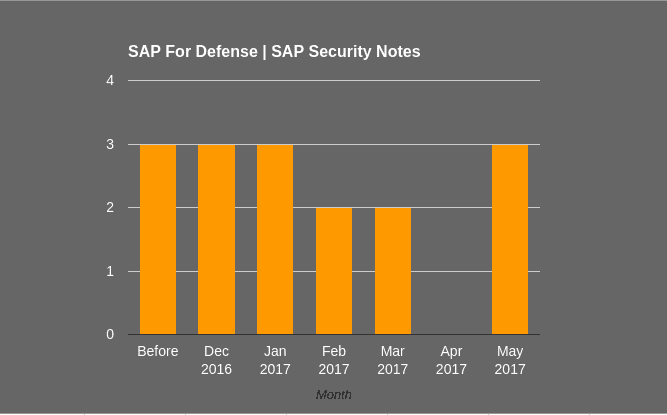
Last November, our Research Labs analyzed SAP For Defense Security and have been working with SAP to help them improve the security of this solution by fixing all reported vulnerabilities. Prior to December 2016, there were only three SAP Security Notes or this solution, and another 13 were published by SAP after December 2016. This month, SAP added another three notes relating to Missing Authority Checks in SAP for Defense Security. These notes are #2394024, #2376743 and #2442630.
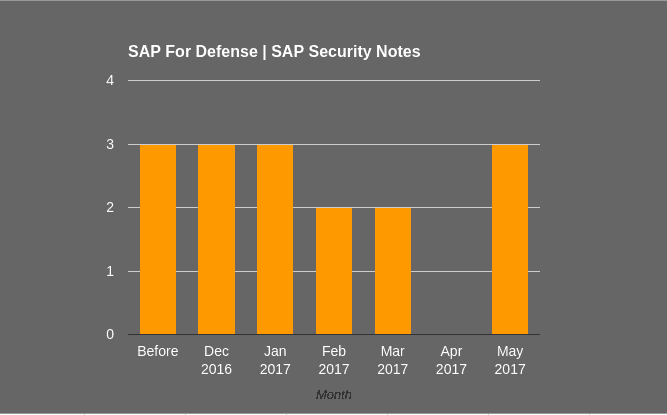
The 13 SAP security notes reported by Onapsis cover over 40 different vulnerabilities that were grouped into these notes and were previously published as shown in the graph. 11 out of 13 bugs, are related to ‘Missing Authority Check’ vulnerabilities and are one of the most relevant bugs for SAP Security. As the Common Weakness Enumeration states: “The vulnerability is given when an actor, who interacts with the system, attempts to access a resource or perform certain action in it to which access should be restricted, and the application lacks of a proper control.” Whether or not the application user is authenticated will influence the CVSS vector, thus in both the CVSS scoring and priority of the SAP security note. Regarding SAP security notes (starting from September of 2009), the vulnerability ‘Missing Authorization Check’ corresponds to approximately a 16% of total notes.
The other two reported bugs in SAP For Defense are an Argument Injection (Note #2376998) and a Denial Of Service attack (Note #2410061).
In summary, Onapsis is constantly working with SAP to protect SAP for Defense, and to date has helped fix over 80% of SAP Security Notes for this solution. The Onapsis Research Labs are already in the process of updating the Onapsis Security Platform to incorporate these newly published vulnerabilities in order to keep our customers secure. With this, it will possible to check whether your systems are up to date with these latest SAP Security Notes, and will ensure that those SAP systems are configured with the appropriate level of security to meet your audit and compliance requirements.
