AppsMas: A Look Back at the 2022 ERP Security Landscape (Video)
Over the past twelve months, we’ve seen threat actors become smarter, faster, and more sophisticated with their attacks on business-critical applications. Business-critical applications, like enterprise resource planning (ERP) applications, run the global economy. If organizations cannot ensure these applications are strictly secure, they not only place their own business at risk, but also data from their partners, customers, and employees. SAP and Onapsis recently found evidence of more than 300 successful exploitation attempts against unsecured SAP applications, pointing to cybercriminals’ clear understanding of ERP applications.
From Elephant Beetle to the ICMAD vulnerabilities, let’s take a look back at some of the ERP vulnerabilities and threat intelligence of 2022, and what we can learn from it.
Log4j Vulnerability: Threat Intelligence and Mitigation Strategies to Protect Your SAP Applications
Log4j (CVE-2021-44228) is a remote code execution (RCE) vulnerability that enables threat actors to execute arbitrary code and take full control of vulnerable devices.The Onapsis Research Labs’ network of sensors, the Onapsis Threat Intelligence Cloud, captured 3,000+ attack attempts and observed over 50 variants within 10 days of the initial Log4j attack. With more than 30 SAP applications affected by this vulnerability, it’s important to understand the implications of the Log4j vulnerability on SAP applications and build a comprehensive vulnerability management program to protect the crown jewels of the business, SAP systems.
ICMAD SAP Cybersecurity Vulnerabilities
At the beginning of the year, Onapsis Research Labs worked with SAP Product Security Response Team to discover and patch three critical memory corruption vulnerabilities affecting SAP Internet Communication Manager (ICM). These ICMAD vulnerabilities could allow attackers to execute malicious activities on SAP users, business information, and processes — and ultimately compromise unpatched SAP applications. In this threat briefing session, SAP CISO Richard Puckett and Onapsis CEO Mariano Nunez share details on the ICMAD vulnerabilities discovered and recommendations to keep your SAP systems safe.
The Elephant Beetle in the Room: An Advanced Financial Attack Leveraging SAP Vulnerabilities
Researchers from Sygnia released a report detailing the activities of a threat group they’ve named Elephant Beetle that stole millions of dollars from Latin American financial sector organizations. Two of the vulnerabilities exploited affect SAP Netweaver Java systems: SAP NetWeaver Invoker Servlet Exploit (CVE-2010-5326) and SAP NetWeaver ConfigServlet Remote Code Execution (EDB-ID-24963). But, the thing is these vulnerabilities are over six years old and there are existing patches for both. Critical vulnerabilities continue to be a prime target for threat actors and it is of the utmost importance for organizations to strengthen their SAP security processes.
The Latest ERP Threat Intelligence from Onapsis Research Labs
Did you know Onapsis is the only business application security company that automatically updates its products with the latest threat intelligence and security guidance from a dedicated security research team? This group of researchers is Onapsis Research Labs, dedicated to solving cybersecurity concerns in ERP applications and to date, has discovered 1000+ zero-day vulnerabilities in business applications and supported 6 U.S. Department of Homeland Security alerts. Watch this session for the latest threat intelligence from the team.
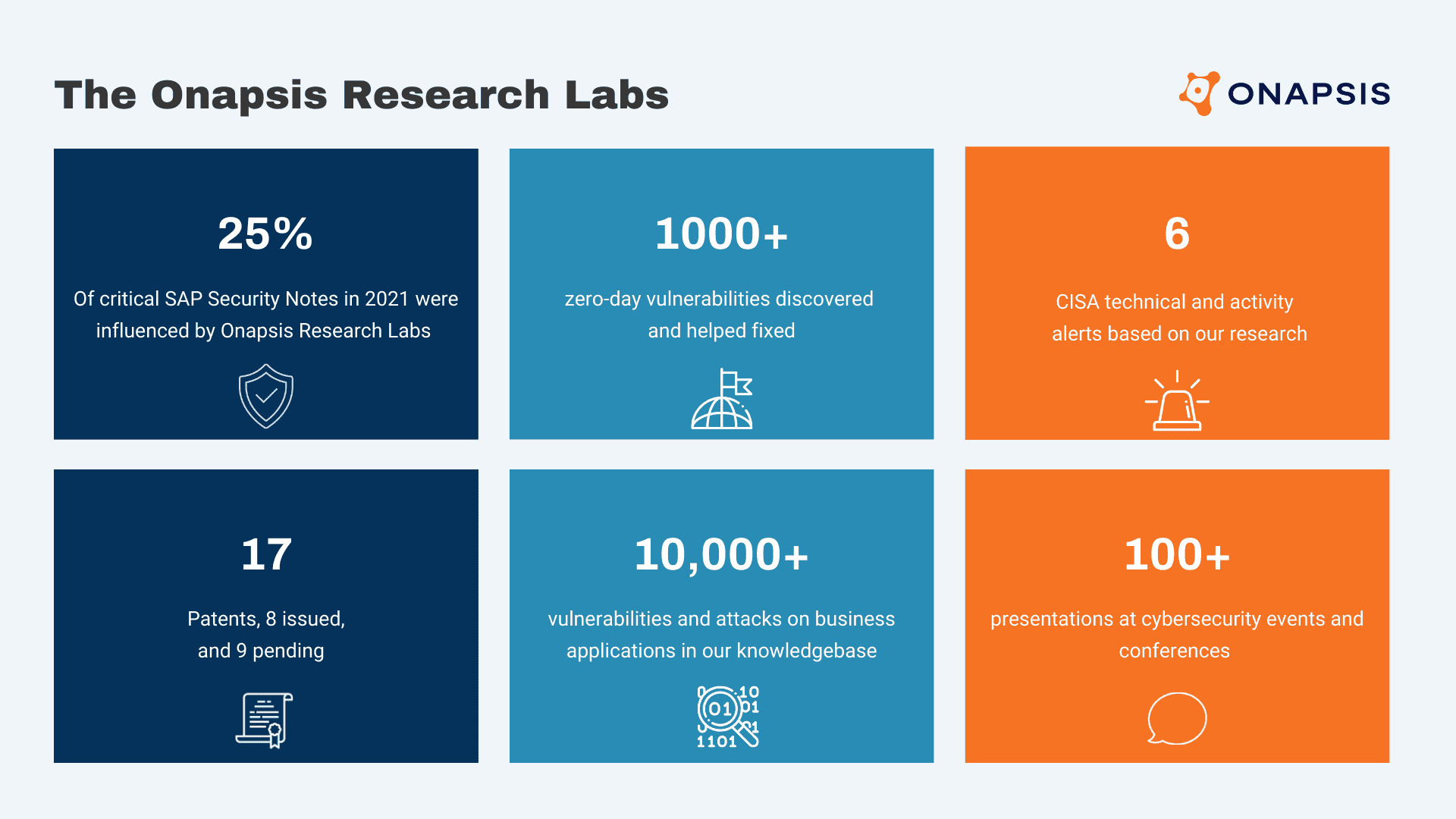
Onapsis Research Labs 2022 ERP Threat Intelligence Recap
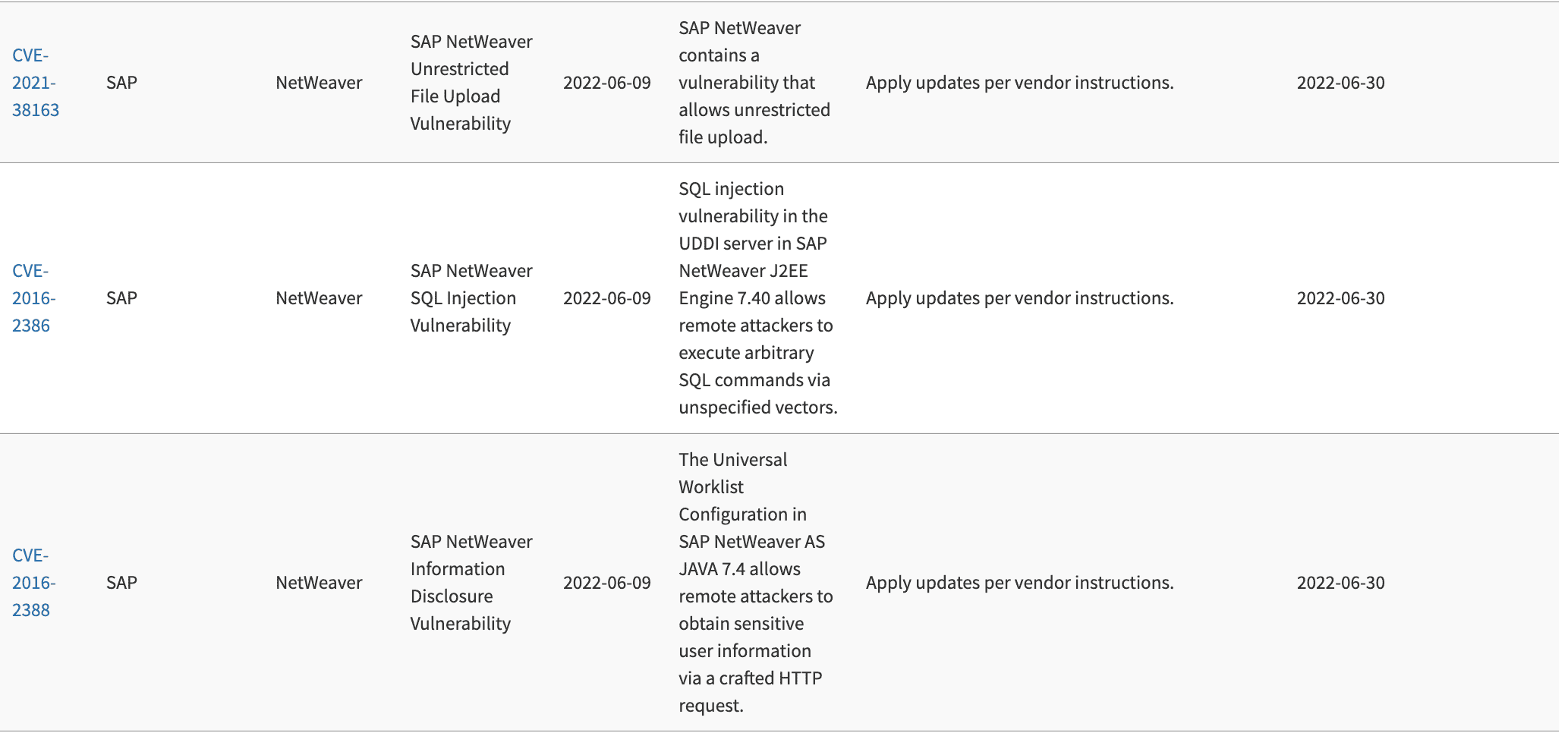
In June, Onapsis Research Labs detected exploitation activity related to three vulnerabilities that were already patched by SAP – CVE-2021-38163, CVE-2016-2386, and CVE-2016-2388. Two out of three of these CVEs have critical CVSS ratings, most of these CVEs have publicly available PoCs and exploits and most of these CVEs are remotely exploitable and through HTTP(s) protocols. CISA has updated its Catalog of Known Exploited Vulnerabilities with these three vulnerabilities. This catalog is a collection of known vulnerabilities that are currently being exploited and mitigation and/or remediation of these vulnerabilities is mandatory for all federal agencies. This session with SAP, CISA and Onapsis shares assets organizations can leverage and steps to ensure SAP systems are protected.
It is safe to assume organizations will continue seeing an increase in exploits against known vulnerabilities, especially those within web-facing applications, since those are lucrative assets for cybercriminals. As we look forward to 2023, enterprises should ramp up the deployment of business-critical application security tools as the number of attacks against these systems continues to grow exponentially. With the general application security market expected to reach $22.54 billion by 2028, it’s evident that organizations are already recognizing the increasing need to protect their enterprise crown jewels. Organizations must prepare by equipping themselves with automated vulnerability management tools that can provide them with complete visibility over their IT ecosystem and help them understand each vulnerability’s level of criticality.






