SAP Security Patch Day October 2021: Critical Patches for SAP Environmental Compliance and SAP Software Logistics Released

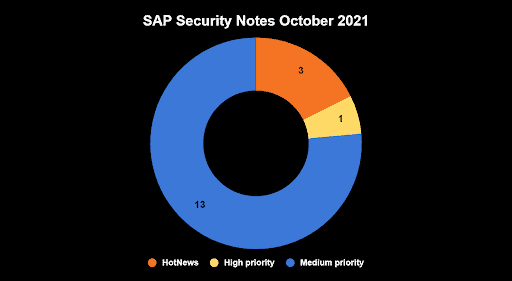
- October Summary – 17 new and updated SAP security patches released, including three HotNews notes and one High Priority note
- Two Applications in Focus – SAP Environmental Compliance and SAP Software Logistics
- An Excursion About Workarounds – The easiest solution is usually not the best solution
SAP has released 17 new and updated SAP Security Notes on its October 2021 patch release, including the notes that were released since last patch day. As part of this month’s patch release, there are three HotNews notes and one High Priority note.
After two months with nine critical SAP Security Notes (priority HotNews and High) each, the October Patch Day is a calmer one.
One of the three HotNews notes is once again the regularly recurring SAP Security Note #2622660 that provides an update for SAP Business Client including the latest supported Chromium patches. SAP Business Client now supports Chromium version 94.0.4606.54 which fixes 65 vulnerabilities in total compared to the last supported version. The maximum CVSS value of all fixed vulnerabilities is 8.8 which is a relatively low value when looking at the maximum values of the last 24 months.
Critical SAP Security Notes in October
Based on CVSS score, SAP Security Note #3101406, tagged with a CVSS score of 9.8, is the most critical of SAP’s October Patch Day. It patches an XML External Entity (XEE) Injection vulnerability in SAP Environmental Compliance (SAP EC). SAP EC is an application that is designed to support emission management and compliance relevant processes in an industrial environment. The application allows the import of master data, such as materials, facilities, hierarchies, or parameters from an Excel template. As this functionality uses a standard library with open source software components, it is directly affected by any vulnerability present in these components. The patch is shipped with newer versions of the affected software components that no longer include the vulnerabilities CVE-2020-10683, BDSA-2017-0180, and CVE-2021-23926.
SAP does not describe the possible impact in detail. Given the fact that the assigned CVSS vector indicates a high impact on confidentiality, integrity, and availability, let’s assume that there is a wide range of possible exploits. In general, an XEE Injection vulnerability is a web security vulnerability that allows an attacker to interfere with an application’s processing of XML data. It often allows an attacker to view files on the application server file system, and to interact with any back-end or external systems that the application itself can access.
The second new HotNews Note is SAP Security Note #3097887, tagged with a CVSS score of 9.1. It patches a critical vulnerability in an ABAP report of the software logistics system of SAP NetWeaver AS ABAP and ABAP Platform. Created in March 1995, the report seems to be harmless as it only provides some information on specified transport requests and/or tasks. But in actuality, it allows anyone with a minimum set of authorizations to change. External researchers have detected that these changes are not protected sufficiently by authorizations. As a result, they can be exploited to transfer ABAP code artifacts or content to quality and production systems, by-passing the established quality gates.
The detected vulnerability is a perfect example of the risks that are involved in the software logistics system in general. Connecting development, quality assurance, and production systems — it represents a central component in SAP that manages almost all changes in an SAP landscape. No surprise that it represents an attractive entry point for attackers!
The only High Priority note on SAP’s October Patch Day is SAP Security Note #3077635, tagged with a CVSS score of 7.8 and patching a Denial-of-Service vulnerability in the SAP SuccessFactors mobile application for Android devices. The note describes that this application has implemented some widely used Android methods that begin executing once the users access their profile. During execution, they can also interact with activities from other Android applications that are running in the background of the user’s device and are using the same types of methods in the application. In addition to the described Denial-of-Service vulnerability, this can also lead to phishing attacks that can be used for staging other types of attacks.
An Excursion about Workarounds
As on almost every SAP Patch Tuesday, the October Patch Day contains some Security Notes that provide a workaround as an alternative to the implementation of the attached patch. While SAP usually flags these workarounds with a standard statement saying that such a workaround should only be considered a temporary solution and that only implementing the attached patch provides a 100% protection, SAP has published three Security Notes in October (SAP Security Notes #3084937, #3080710, and #3099011) that do not include this statement. They all patch vulnerabilities in ICF services and the corresponding workarounds recommend disabling the affected services. At a first glance, this seems to be completely reasonable. But looking at this recommendation in more detail, it includes at least two risks if patching is not completed:
- If a service is currently not needed by any of the business applications, an administrator tends to prefer the “easy” mitigation and just deactivates the vulnerable service. Some weeks, months, or even years later, there might be new applications or changes in existing applications that require an activation of the service. If the reason for the former deactivation was not properly documented, there is a high risk that the (still vulnerable) service is reactivated again.
- The status of an ICF service can also be manipulated unnoticed from outside of the system through a specially crafted transport request. This allows an attacker to reactivate a vulnerable ICF service on a system even without having a user on that system.
Summary & Conclusions
After two busy months, SAP’s October Patch Day was a calmer one with only four critical notes. The lessons learned from this Patch Day: The software logistics system in SAP requires special attention. Vulnerabilities in this area, as with the one patched with HotNews note #3097887, usually have a big negative impact on SAP systems. In addition, it provides an attack surface by design. Developers can manipulate almost every table on a development system via ABAP and the software logistics system often allows the transport of tables that are not actually intended for transports (like the table that contains status information of an ICF service). Quality Assurance measures in this area focus on functionality and performance. Security plays a minor role and is usually restricted to checks for sufficient AUTHORITY-CHECKS in reports. It is nearly impossible to check the object list of a transport request manually for anything that could potentially harm a target system. More information about the dangers in SAP software logistics (aka SAP Transport Management System) can be found in our blog series “Dangers in SAP Transport Management”.
The Onapsis Research Labs is continuously updating The Onapsis Platform to incorporate newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.
Further Reading
- This joint report from Onapsis and SAP analyzes how threat actors are actively targeting unprotected SAP applications.
- Onapis and SAP address how to protect your organization’s business-critical applications from the looming threat of ransomware.
