SAP Security Patch Day November 2021: Critical Patch for ABAP Platform Kernel

Highlights of November SAP Security Notes analysis include:
- November Summary – 11 new and updated SAP security patches released, including one HotNews note and three High Priority notes
- Calm Patch Day – Only eight new security notes since October Patch Day
- In Focus: ABAP Platform Kernel – Missing Authorization Check can lead to an escalation of privileges
SAP has released 11 new and updated SAP Security Notes on its November 2021 patch release, including the notes that were released since last Patch Day. As part of this month’s patch release, there are one HotNews note and three High Priority notes.
One of the High Priority notes, SAP Security Note #2971638, is an update of a vulnerability in CA Introscope Enterprise Manager that was detected in 2020 by the Onapsis Research Labs. Hard-coded default passwords for the Admin and the Guest user allowed a remote attacker to bypass authentication, compromising the confidentiality of the service. (For more details, see our October 2020 Patch Day analysis.) The note has been updated by SAP with additional manual instructions for customers who are still using Introscope 10.5 or versions older than 10.7.0.307.
Critical SAP Security Notes in November
The only HotNews notes of SAP’s November Patch Day is SAP Security Note #3099776, tagged with a CVSS score of 9.6. The note patches a Missing Authorization Check vulnerability in ABAP Platform Kernel that can result in an escalation of privileges for an authenticated business user. The vulnerability affects trusted connections to other systems via RFC and HTTP communication, allowing the user to execute application-specific logic in other systems. SAP optimistically labeled the CVSS vector of the vulnerability as low impact on availability despite the fact that a business user “… is able to read and modify data…”. Due to the criticality and the impact on systems beyond the vulnerable system, we strongly recommend applying the corresponding kernel patch.
High Priority note #3110328 is tagged with a CVSS score of 8.3 and also patches a Missing Authorization Check vulnerability, resulting in an escalation of privileges for an authenticated user. Any SAP Commerce installation using Commerce Organization is impacted by this vulnerability that can highly compromise the system’s integrity and availability.
SAP Security Note #2827086, tagged with a CVSS score of 7.9, is the third High Priority note of the November Patch Day. It affects SAP Forecasting and Replenishment for Retail (FRP or F&R). This software component can be connected to SAP Retail but the vulnerable engine can also be used with purchasing systems of other software vendors. SAP F&R is used by retail companies to cut surplus stock and reduce stockouts in distribution centers and stores. It is also used to increase transparency in the supply chain. The note patches known vulnerabilities in Open Source libraries used by the software. SAP mentions a Memory Corruption vulnerability and a Denial of Service vulnerability, which can lead to a complete system crash in the worst case.
Information Disclosure in SAP GUI for Windows
With a CVSS score of 6.8, SAP Security Note #3080106 just missed being tagged as a High Priority note. Nevertheless, because of the high number of affected SAP customers, it is worth mentioning here. The note patches an Information Disclosure vulnerability in SAP GUI for Windows 7.60 and 7.70 that allows an attacker with “sufficient privileges on the local client-side PC to obtain an equivalent of a (connected) user’s (SAP) password”. With that information, the attacker is able to log on to the SAP system and impersonate the original SAP user. The CVSS score of 6.8 does not reflect the impact once the attacker is connected.
Information on SAP Security Note #3105728
SAP Security Note #3105728 is tagged with a CVSS score of 4.9 and describes a Leverage of Permission vulnerability in SAP NetWeaver Application Server for ABAP and ABAP Platform. It fixes a template role that contains unnecessary high privileges allowing “to transport ABAP artifacts”. The associated patch can obviously only fix this template role. It cannot correct any customer role that was copied from this template role. The note briefly explains how to identify such roles. As transports are one of the most underestimated attack vectors in SAP, I would like to explain in more detail how to identify roles that might require manual correction:
1. Log in to the SAP system with an administrative account
2. Call transaction SUIM
3. Expand the menu tree and execute the following option:
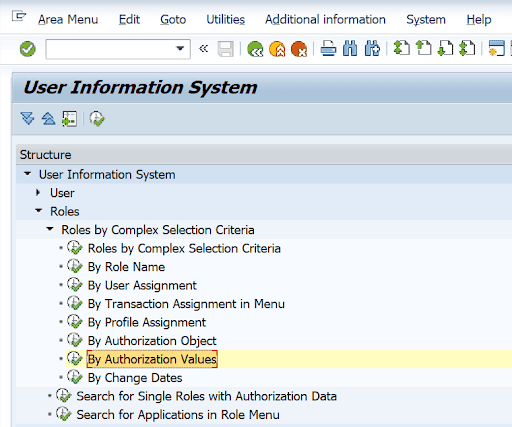
4. In the following screen, enter S_CTS_ADMI in field Object 1:
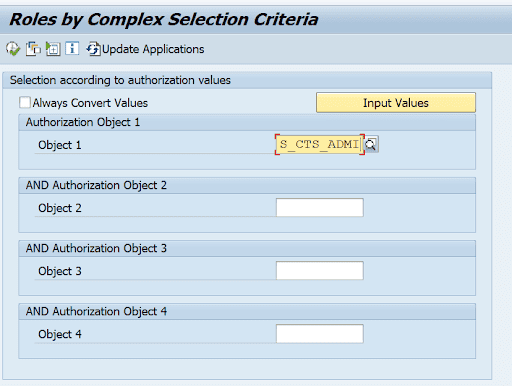
5. Press the Input Values button
6. Enter the values IMPA and IMPS as a filter for field CTS_ADMFCT:
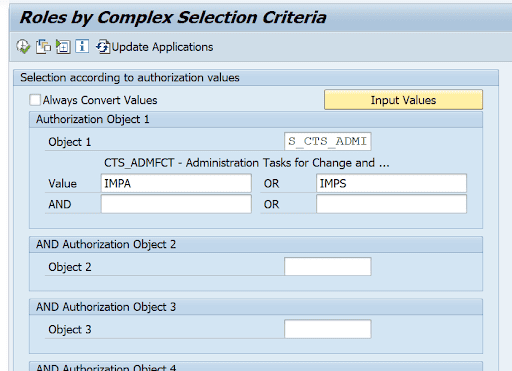
7. Press Execute (F8)
As a result, you get all single and composite roles that include the critical values. Depending on the purpose of the roles, the values should be removed using the Profile Generator (transaction PFCG).
Summary & Conclusions
SAP’s November Patch Day was a relatively calm Patch Day. Eleven notes in total with only three new notes above CVSS 7.0 is a record low number for the year. Nevertheless, the lower-rated notes should not be left unaddressed as some of these vulnerabilities can be used to launch follow-up attacks, e.g., through impersonation of users or exploiting transport permissions. Ultimately, the rating of this month’s notes are not always commensurate with the damage they could do.
The Onapsis Research Labs is continuously updating The Onapsis Platform to incorporate the newly published vulnerabilities into The Onapsis Platform so that our customers can protect their organizations.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Newsletter.
