SAP Security Patch Day August 2020: SAP Knowledge Management Affected by Two Critical Patches

Highlights of August SAP Security Notes analysis include:
- August Summary—21 new and updated SAP security patches released, including two HotNews Notes and six High Priority Notes
- Onapsis Research Labs Collaboration—Most critical vulnerability once more detected by our Research team, plus three other critical vulnerabilities
- SAP Knowledge Management in Focus—Cross-Site Scripting vulnerability can result in complete compromise of system confidentiality, integrity and availability
While the SAP community is still discussing the impact and malicious activities around the RECON vulnerability, SAP has published 21 new and updated Security Notes on its August patch day. This number includes two HotNews Notes and six High Priority Notes. Fortunately, one of the two HotNews Notes is just a minor text update on the RECON note #2934135 originally published at the end of July. Remember that Onapsis has a free online service and downloadable open source scanning tool to quickly help organizations assess if their SAP applications are vulnerable and detect indicators of compromise related to exploitation of the RECON vulnerability (CVE-2020-6287). If you haven’t ensured you are not vulnerable to RECON yet, we highly recommend you start there, based on its unique criticality. If you have already patched it, or at least applied some of the workarounds described in the Threat Report and SAP Security Note, you can now focus on the newly released patches.
The second HotNews Note of August, as well as one of the High Priority Notes, provide patches for two critical vulnerabilities in SAP Knowledge Management – the most affected SAP component on August patch day.
Onapsis Research Labs Contributed in Solving Two Critical Vulnerabilities in Sap Knowledge Management
As a result of the Onapsis mission of aiding SAP in protecting its customers, the Onapsis Research Labs already contributed to the patching of 29 vulnerabilities in 2020, 19 of them rated as critical (High Priority + HotNews Notes).
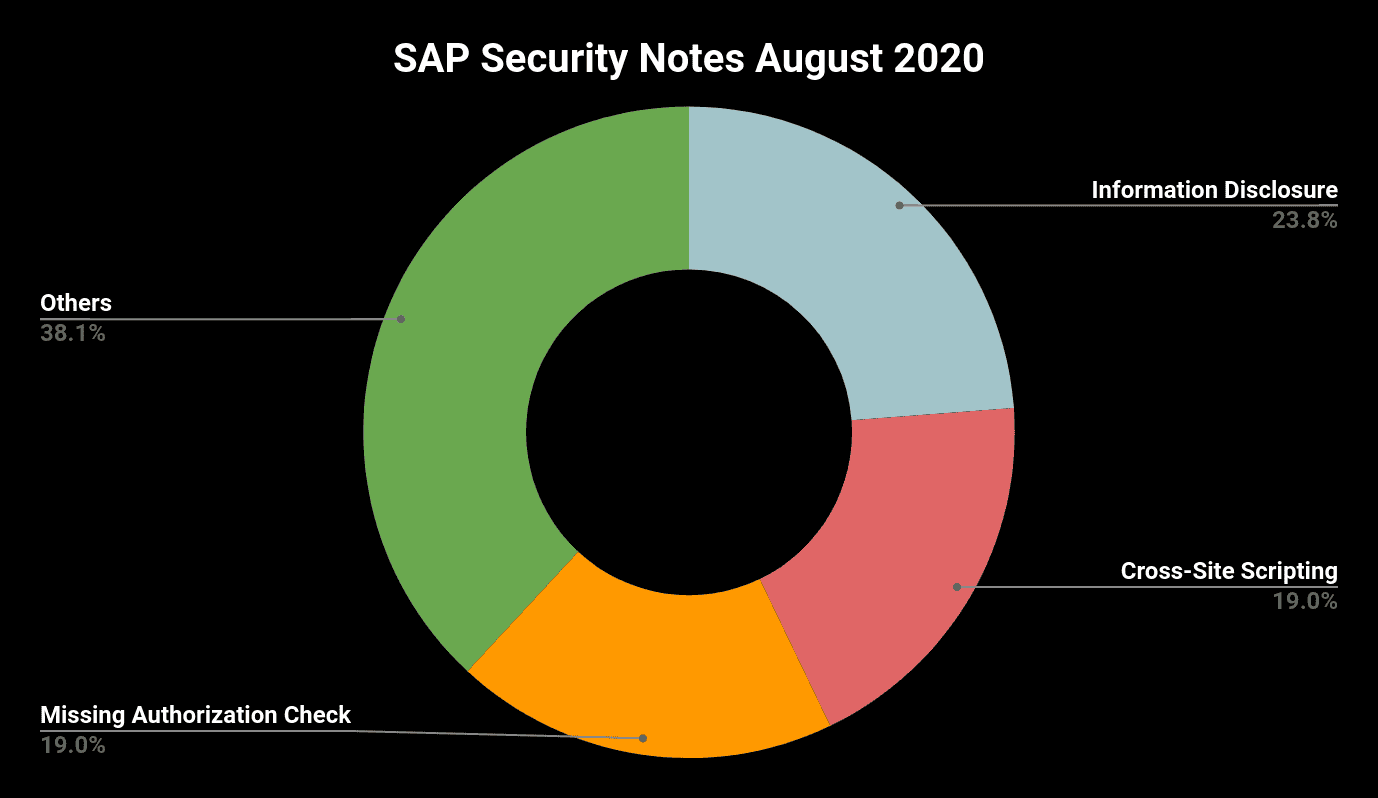
The most critical vulnerability of August patch day affects SAP Knowledge Management. SAP Security Note #2928635 patches a Cross-Site Scripting vulnerability that can result in complete compromise of system confidentiality, integrity and availability.
Knowledge Management (KM) is a component of SAP NetWeaver, specifically of SAP Enterprise Portal. It is intended as a unified entry point to manage different data sources in various formats and comes by default with every installation of SAP Enterprise Portal.
Users can create new content, folders, modify existing ones and upload files to the system. They can upload, by default, files of any type, including html files, which, when read by any other user will be rendered by their browsers. The Onapsis Research Labs detected that this upload process can be exploited to upload malicious html files with javascript code in it, performing a Stored Cross-Site Scripting (XSS) attack. The exploit is possible as the filtering mechanism that was implemented by SAP in order to prevent uploaded files from being injected with executable scripts did not work properly.
The vulnerability has a CVSS score of 9.0, and only the fact that it needs additional user interaction (a user with administrative privileges who accesses the malicious file), prevents it from being scored a 9.9.
The Onapsis Research Labs also detected the possibility to create files or modify/delete existing ones in SAP KM with an unauthenticated user. This vulnerability is described and patched with SAP Security Note #2938162, titled “Unrestricted File Upload in SAP NetWeaver (Knowledge Management)”. SAP strictly separates this vulnerability from the previous one. As a result, the CVSS score of this threat is 7.3. The combination of both exploits not only represents a very serious danger, but also if the HotNews isn’t applied, this last vulnerability can then be exploited without authentication, making it more critical (which would represent a potential CVSS Score of 9.6). In other words, SAP Security Note #2938162 is not critical only because the other patch is already available, so it is highly important to apply both of them.
Further Contribution From the Onapsis Research Labs
The Onapsis team has also found a Code Injection vulnerability in SAP NetWeaver AS ABAP and ABAP Platform, allowing any authenticated user to replace an arbitrary SAP standard report by code that the user recorded during a batch input session. As described in the corresponding High Priority Note #2941667, tagged with CVSS score 8.3, this can lead to a Denial of Service e.g., by overwriting essential logon programs. The patch includes the implementation of several authorization checks. The report creation for the recorded code is now implemented via the respective API functions that automatically provide various repository checks including the check for already existing reports.
High Priority Note #2941315, tagged with CVSS score 7.5, describes a Missing Authentication Check vulnerability that was found by the Onapsis Research Labs in SAP NetWeaver AS JAVA. The vulnerability is exposed by a web service and an exploit can result in a complete denial of service.
Other Important SAP Security Notes in August
The three remaining High Priority Notes affect SAP Business Object, SAP Banking Services and SAP Adaptive Server Enterprise.
SAP Security Note #2927956, tagged with CVSS score 8.5, patches a vulnerability that allows an attacker with access to the internal network(LAN) to gain unauthenticated access to X server. As a result, the attacker can comprehend keyboard and mouse activities of a user who is connected remotely and can even grab screenshots of the remote host. From this, it is possible to gain access to the user name and password of the connected user.
SAP Security Note #2939685 describes a Missing Authorization Check vulnerability in SAP Banking Services. This High Priority Note, tagged with CVSS score 8.3 is strongly recommended for all SAP customers, especially those regulated by GDPR as the vulnerability allows an attacker to read protected Business Partner Generic Market Data (GMD) or to modify the related GMD data key figure values in SAP Banking Services.
SAP Security Note #2941332, tagged with CVSS score 7.0, patches an Information Disclosure vulnerability in the installer of the SAP Adaptive Enterprise cockpit. It allows an attacker to read information of the installation log files that can be used afterwards to start further attacks.
Summary & Conclusions
Time to take a deep breath. While the last few SAP patch days were marked by a high number of critical HotNews Notes with CVSS scores far above 9.0 and ending up with the 10.0 RECON vulnerability in July, SAP only published one new HotNews Note in August, tagged with a CVSS score of 9.0. Nevertheless, the total number of released patches in August matches exactly the 2020 monthly average, which is significantly higher than it was in 2019. RECON has shown the importance of giving attention to SAP’s patch days. However, dismissing or underestimating lower rated Security Notes would be a grave mistake. The CVSS score of a note can only take into account standard criteria. It can neither represent the individual impact in a specific SAP installation nor does it reflect the impact when combining multiple exploits.
As always, the Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.