SAP Security Notes October ‘18: First Critical BusinessObjects Note in Five Years
Today is a new second Tuesday of the month and SAP has released a batch of 12 new security notes for this October’s Security Patch Day. These total 20 security notes after adding to the other eight security notes released throughout the last month. Among the most critical, one tagged as Hot News is about a security bug in SAP BusinessObjects BI Suite allowing access to information without the required authorizations. This note has a high CVSS v3 Base Score of 9.8/10, being the first note for this platform tagged as Hot News in over five years.
On the other hand, one of the High Priority notes for this month is the re-released security note #2681207 that fixes a security bug in the SAP HANA XS Engine, reported by the Onapsis Research Labs. The reason for the re-release is not the patch itself, which has no changes, but involves a technical description of the note. In the solution section, SAP re-named the previously called ‘workarounds’ to ‘measures to reduce the attack surface’ which mostly consists of a further explanation of possible protection measures that could be present on OData software packages running in HANA’s Extended Application Services classic model.
This vulnerability, described in September’s blog post, consists of a failure for parsing XML data strings that take place in the applications running in the xsengine. Two approaches for exploiting this security bug may produce either a Denial of Service (DoS) of the HANA xsengine threads making the system unresponsive or a crash to the xsengine threads, a condition with the potential for an attacker to execute a remote code execution.
A subtle but noticeable change in the title for security note #2681207, from ‘DOS Vulnerability in SAP HANA, Extended Application Services Classic Model‘ to ‘Missing XML Validation Vulnerability in SAP HANA, Extended Application Services Classic Model‘ puts the focus on the XML parsing failure. It seems a more appropriate title because it reflects the nature of that failure and does not limit the potential exploitation to a DoS attack, as we originally discussed in last month’s blog post about the two approaches for exploiting this vulnerability. Remember that due to this fact, we reported this bug with a higher CVSS, considering not only the impact to availability, but also to integrity and confidentiality. In reality the criticality could be higher than the current one in the note and it is recommended to patch as soon as possible.
If you have already patched for this note, or have the same or higher Support Package / Patch Level, you do not need to re-apply the patch. When patching vulnerabilities in HANA keep in mind that SAP advises installing the latest Support Packages version or Patch Level revision available. So, it is not a surprise to find, like in this case, that the patches specified and linked in the SAP Security Note may lead to a higher Patch Level or even do not exist since a newer Support Package replaced the one prescribed in the security note. If that is the case, please install the newest one available.
One of the two critical security notes for this month is #2654905 and is the first SAP BusinessObjects Hot News since 2012. Again it is related to SAP BusinessObjects and an Information Disclosure vulnerability due to a failure in some Central Management Server (CMS) scripts that can be executed without properly checked authorizations. The CMS is a central component for SAP BusinessObjects BI Suite. It manages the user’s database and authorizations, performs authentication and authorization, holds the information about all servers, folders, permissions and overall configurations.
The Onapsis Research Labs has been focusing on the SAP BusinessObjects BI platform both by adding support for the Onapsis Security Platform and by reinforcing the research for security bugs that led to some relevant findings like the vulnerabilities #2644154 we reported as fixed in our blog post for August.
Hot News and High Priority Notes
This month SAP issued a total of two Hot News and five High Priority security notes. Besides the two security notes we explained above, you can find the fifth re-release of the recurring Hot News security note for SAP Business Client #2622660. This note comes with the fix for a group of 40 Chromium vulnerabilities, eight of them classified as High, that are part of the Business Client. It is advised to update to the latest version of the SAP Business Client to avoid users being a victim of an exploitation of any of these security bugs.
Among the other four High Priority notes, one is a re-release. No action is required if this note, #2392860 Leveraging Privileges by Customer Transaction Code, was already installed after its initial release in February 2017. It fixes the possible use of a reserved transaction code included in a standard SAP role. Exploitation requires a malicious user to use that code in a development system and let that change be transported to the production system.
In the case of the security note #2699726, [CVE-2018-2475] Missing Network Isolation in Gardener, one cannot see immediately the connection to an SAP product unless one is familiar with the Kubernetes containers used in the infrastructure used by the SAP Cloud Platform. As a user of that platform-as-a-service, SAP advises updating to Gardener release 0.12.2.
An important security note regarding environments that integrate SAP systems to manufacturing or industrial systems using the open platform communication (OPC) standards is #2674215 Denial of Service (DOS) in OPC UA Applications of SAP Plant Connectivity. The vulnerability has been addressed by the OPC Foundation and fixed. The note details the required patch level for each Plant Connectivity Version and Support Package. The last High Priority security note #2696962 Denial of Service (DoS) Vulnerability in SAP Foundation / Database affects users or developers of the SAP Cloud Platform SDK for iOS due to a vulnerability in the widely used SQLite database which is prone to local Denial of Service. It can be solved both by installing the appropriate patch and following some simple rules for coding the mobile software detailed in the security note.
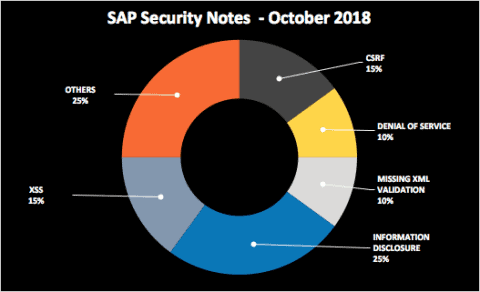
Finally, here’s a summary of the type of bugs SAP patched this month through its Security Notes:

SAP recognized Onapsis, in the last two months, through three researchers from our Research Labs, Martin Doyhenard, Gaston Traberg and Pablo Artuso, who have helped SAP to improve the security and integrity of their customers’ IT systems.
As we regularly do at Onapsis, we will continue to publish our SAP Security Notes Patch Day analysis blogs every Patch Tuesday and work to update the Onapsis Security Platform to incorporate these newly published vulnerabilities. This will allow our customers to check whether their systems are up to date with the latest SAP Security Notes and will ensure that those systems are configured with the appropriate level of security to meet their audit and compliance requirements.
Please follow our ERP security blog or follow us on Twitter for more information about the latest SAP security issues.

