SAP Security Patch Day March 2021: Critical Patch Released for SAP MII and SAP NetWeaver AS Java

Highlights of March SAP Security Notes analysis include:
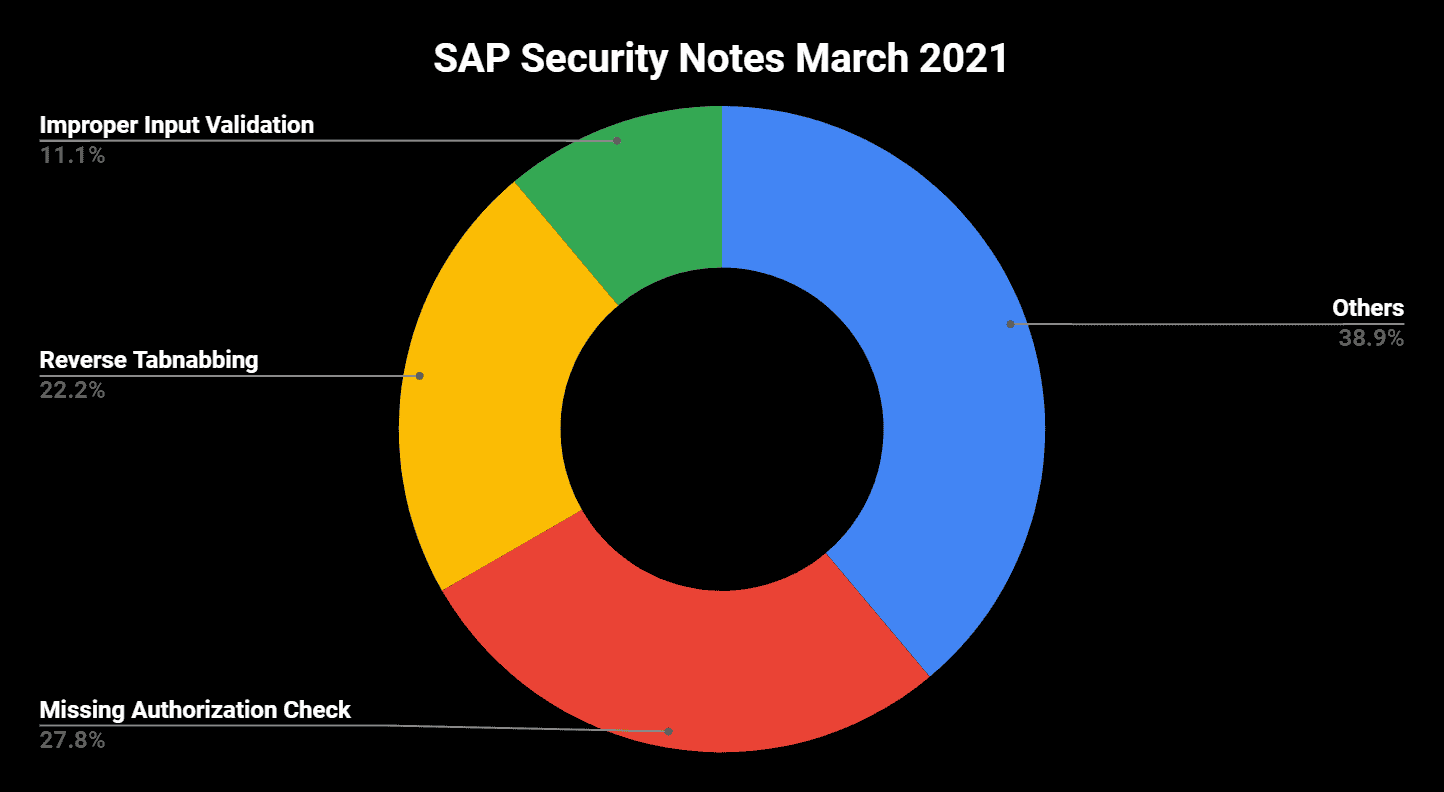
- March Summary—18 new and updated SAP security patches released, including four HotNews notes and one High Priority notes
- Serious Vulnerability in SAP MII—the Onapsis Research Labs contributed in fixing the most critical vulnerability, based on CVSS score
- SAP Continues to Fix Reverse Tabnabbing Vulnerabilities—introduction of new properties ensures protection by default
SAP has released 18 new and updated SAP Security Notes in its March 2021 patch release, including the notes that were released since last patch day. As part of this month’s patch release, there are four HotNews notes and one High Priority note.
Fortunately, the two HotNews notes that are tagged with a CVSS score of 10.0 are not as critical as they may seem to be:
HotNews note #2890213 titled, “Missing Authentication Check in SAP Solution Manager” only contains a minor textual update to the possible symptoms of the vulnerability. The note was originally released in March 2020. The last important update of this note was published in November 2020 providing support for an additional support package level of the affected application.
As already suspected in our February blog post, SAP has responded quickly to the Chromium CVE-2021-21148 zero-day vulnerability that, following Google, was exploited in attacks in the wild. Thus, the new SAP Business Client patch that is released with SAP Security Note #2622660 now includes Chromium version 88.0.4324.150. Compared to the last supported Chromium version (87.0.4280.66), this new version fixes 67 security issues in total, two of them rated by Google as critical (CVE-2021-21117 and CVE-2021-21142). The highest CVSS score of all newly fixed vulnerabilities is 9.6.
In Focus: SAP Manufacturing Intelligence and Integrations (SAP MII)
The Onapsis Research Labs contributed in fixing this patch day’s most critical vulnerability (based on CVSS score and taking into account the information of the previous section). SAP Security Note #3022622, tagged with a CVSS score of 9.9, patches a very critical code injection vulnerability in SAP Manufacturing Intelligence and Integrations (SAP MII). SAP MII or xMII (its previous name) is an SAP NetWeaver AS Java based platform that enables real-time production monitoring and provides extensive data analysis tools. It functions as a data hub between SAP ERP and operational applications such as manufacturing execution systems (MES). The software collects data from production machinery, delivering real-time insights into its performance and efficiency.
An integral part of SAP MII is the Self-Service Composition Environment (SSCE) that can be used to design dashboards by simple drag and drop. The SSCE allows users to save a dashboard as a JSP file. An attacker can intercept a request to the server, inject malicious JSP code in the request and forward it to the server. When such an infected dashboard is opened in production by a user having a minimum of authorizations, the malicious content gets executed, leading to remote code execution in the server. Some possible actions are:
- Access to the SAP databases and read/modify/erase any record in any table
- Use these servers to pivot to other servers
- Place malware to later infect end users
- Modify network configurations and potentially affect internal networks
Facing the large variety of possible impacts, Onapsis strongly recommends applying the corresponding patch as soon as possible. The patch will prevent dashboards from being saved as JSP files. Unfortunately, there is no more flexible solution available. If JSP files are required, customers should restrict access to the SSCE as much as possible and validate any JSP content manually before moving it to production.
For Onapsis customers using the Defend product of The Onapsis Platform (version 2.2021.22), a detection capability is already in place to continuously monitor for malicious activity and trigger alarms to help prevent potential attacks abusing the SAP MII vulnerability.
Other Critical SAP Security Notes in March
SAP HotNews Security Note #3022422, tagged with a CVSS score of 9.6, patches a missing authorization check in the Migration Service of SAP NetWeaver AS Java. This service is used internally by the migration framework for migrating applications between major releases of the J2EE Engine. The missing authorization check might allow an unauthorized attacker to gain administrative privileges. This could result in complete compromise of the system’s confidentiality, integrity and availability.
As applying the patch that is attached to the note requires a system restart, SAP also provides a temporary workaround that can be deployed online. SAP refers to the workaround as “a notable improvement,” but recommends applying the final patch in parallel as soon as possible. While the workaround just blocks the accessibility to the Migration Service, the final patch adds the missing authorization check to it.
SAP Security Note #3017378, tagged with a CVSS score of 7.7, is the only High Priority note of the SAP March patch releases and fixes the possibility of an authentication bypass in SAP HANA LDAP scenarios. The authentication bypass is possible if the following conditions apply:
- The LDAP directory server is configured to enable unauthenticated bind
- The SAP HANA database is configured to allow access based on LDAP authentication
- SAP HANA is configured to automatically create users based on LDAP authentication
Following the assigned CVSS vector, the vulnerability has a high impact on the system’s confidentiality and integrity.
More Reverse Tabnabbing Vulnerabilities Fixed
SAP has fixed reverse tabnabbing vulnerabilities for another two UI technologies/frameworks. While SAP Security Note #2976947 fixes this vulnerability for Web Dynpro Java, SAP Security Note #2977001 does the same for HTMLB for Java. In difference to the patches for other UI technologies, these two patches require an additional fix for SAP NetWeaver AS Java, provided with SAP Security Note #2978151. The set of security notes that are related to reverse tabnabbing vulnerabilities is completed by an update on SAP Security Note #2972275, patching the vulnerability for SAP Business Server Pages applications on SAP NetWeaver ABAP. This note comes with an update on the correction instruction section.
A good overview and summary about all reverse tabnabbing patches can be found in this SAP Knowledge Base article #3014875.
Summary & Conclusions
With 18 new and updated SAP Security Notes, SAP’s March Patch Day is slightly below the average amount of patches released in the first two months in 2021.
With SAP MII, SAP NetWeaver AS Java and SAP HANA, three different applications are affected this time by critical vulnerabilities (HotNews and High Priority). Especially the vulnerability in the Migration Service of SAP NetWeaver AS Java demonstrates once more, that even components that are not that visible to an SAP customer can represent a high risk if they are not fixed. The same applies to SAP components that are “not used” by a customer.
The fact that they are not used by the customer does not prevent them from being used by attackers as an entry point into the system as long as they include exploitable vulnerabilities!
As always, the Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.