SAP Security Patch Day February 2021: Critical Patch released for SAP Commerce

Highlights of February SAP Security Notes analysis include:
- February Summary—20 new and updated SAP security patches released, including three HotNews Notes and two High Priority notes
- Serious Vulnerability in SAP Commerce—Misconfiguration in default user permissions can lead to a complete compromise of the system
- Multiple Reverse Tabnabbing Vulnerabilities Fixed—Several applications affected by this often underestimated issue
SAP has released 20 new and updated SAP Security Notes on February’s Patch Day, including the notes that were released since last Patch Day.
As part of this month’s patch release, there are three HotNews notes and two High Priority notes.
But once again, it’s worth taking a closer look at these numbers.
One of the three HotNews notes, SAP Security Note #2986980, tagged with a CVSS score of 9.9, was initially released on January Patch Day. The note comes with a patch for a critical SQL Injection and Missing Authorization vulnerability in the database interface of SAP Business Warehouse. It was updated twice since its first release and there are now patches available for more support package levels and also for BW releases from BW 7.0 to 7.02.
Another HotNews note is SAP Security Note #2622660, the constant patch day companion that provides a new update of the SAP Business Client. These updates are mostly initiated by newly available Chromium patches. The newest SAP Business Client patch includes Chromium version 87.0.4280.66, which fixes 11 High Priority security issues, of which there are 33 in total. Here we can expect more updates very soon, as there is currently a lot of noise on the internet regarding the Chromium CVE-2021-21148 zero-day vulnerability. Following Google, the corresponding “heap overflow” memory corruption bug in the V8 JavaScript engine was already exploited in attacks in the wild. So, one can expect another SAP Business Client Patch containing Chromium version 88.0.4324.150 soon. The only purpose of this Chromium version that was released by Google on February, 4th, was to patch CVE-2021-21148.
The two updated High Priority notes, SAP Security Notes #3000306 and #2993132, tagged with a CVSS score of 7.5 and 7.6 and affecting SAP NetWeaver AS ABAP, ABAP Platform and SAP S4 HANA, were released at the end of January. While note #3000306 includes some restrictions regarding its validity, note #2993132 contains updates to the correction instructions.
In Focus: SAP Commerce
The most critical patch of SAP’s February Patch Day is the only new HotNews note #3014121, tagged with a CVSS score of 9.9. This patch fixes a serious Code Injection vulnerability in SAP Commerce. Only SAP Commerce installations that have the rule engine extension installed are affected. But as this extension is a common part of SAP Commerce installations, the patch addresses the majority of these installations.
The rule engine is based on an engine called Drools. It is used to define and execute a set of rules that can manage even extremely complex decision-making scenarios. Drools rules contain a ruleContent attribute that provides scripting facilities. Changing of ruleContent should normally be limited to highly privileged users, like admin and other members of admingroup. Due to a misconfiguration of the default user permissions that are shipped with SAP Commerce, several lower-privileged users and user groups gain permissions to change DroolsRule ruleContents and thus gain unintended access to these scripting facilities. This enables unauthorized users to inject malicious code into these scripts resulting in a strong negative impact on the application’s confidentiality, integrity and availability.
The provided patches only fix the default permissions when initializing a new installation of SAP Commerce. For existing installations of SAP Commerce, additional manual remediation steps are required. The good news is that for existing installations, these manual remediation steps can be used as a full workaround for SAP Commerce installations that cannot install the latest patch releases in a timely manner.
Top Scorer Vulnerability in February: Reverse Tabnabbing
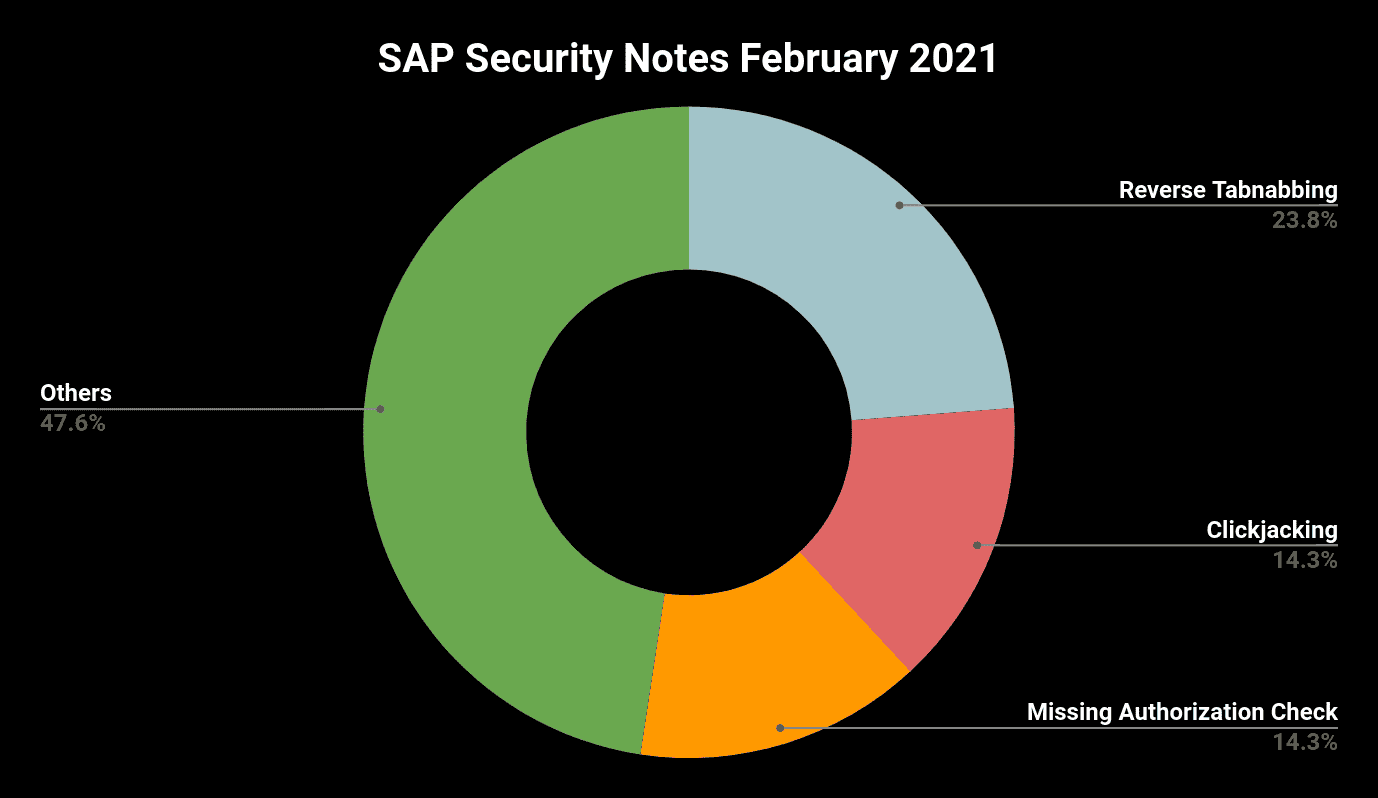
When looking at the 13 SAP Security Notes that were released for the first time on February Patch Day, it is noticeable that five of these notes fix a Reverse Tabnabbing vulnerability (each of them patching one Web UI technology/framework; details can be found in SAP Knowledge Base article #3014875). So, it is worth having a closer look at this type of vulnerability.
Some links are designed to open the linked document in a new browser tab/window. This can be achieved in both HTML and JavaScript. In HTML, specifying _blank as the value of the anchor element’s target attribute will do the trick:
Assuming my banking website “mybank.com” provides a link to one of its partners. The link:
<a href=”https://ourpartner.com” target=”_blank”>Visit our partner page!</a>
will open the partner page in a new browser tab.
Using the JavaScript DOM API, the same can be achieved by simply invoking window.open:
window.open(“https://ourpartner.com”);
Because the browser runs the new window in the same process as the first window, it allows a certain degree of interaction between the two, even if the source page and the target page are located in different domains.
Specifically, it allows the linked document to address the first tab of the browser with the original source page. Being able to do so, the target page is able to redirect/replace the original page to/by a phishing page without any interaction of the user.
With this code snippet,
<script>
const url = “fakebank.com”;
window.opener.location.replace(url);
</script>
The linked target document can replace the original mybank.com page in the first browser tab by a fakebank.com phishing page that might look exactly the same. By providing a login dialog on this page, the malicious fakebank.com site can then send the provided user credentials to an external server of the attacker.
Fortunately, this vulnerability type can easily be mitigated. For HTML links, add the rel attribute:
<a href=”https://ourpartner.com” target=”_blank” rel=”noopener noreferrer”> Visit our partner page!</a>
Instead of setting the noreferrer on every link separately, it’s also possible to add it to the HTTP header:
Referrer-Policy: noreferrer
In addition, various major browser vendors have started to provide an implicit “rel=noopener” behavior in case of the usage of target=”_blank”.
The JavaScript version can be mitigated through:
function openPopup(url, name, options){
// Open the popup and set the opener and referrer policy instruction
var newWin = window.open(null, name, ‘noopener,noreferrer,’ + options);
// Reset the opener link
newWin.opener = null;
// Now load the correct url
newWin.location = url; }
Summary & Conclusions
With only 13 “really” new SAP Security Notes, SAP’s February Patch Day was again a relatively “calm” one.
The only new critical patch (priority HotNews or High) was released for SAP Commerce. This allows affected customers to spend time going through the described manual mitigation steps for their existing installations. With regard to the assigned CVSS score of 9.9 and facing the potential impact on the application, it is strongly recommended to mitigate the vulnerability as soon as possible.
Nearly unknown from previous patch days, this time Reverse Tabnabbing was the top scorer vulnerability. Although this vulnerability type can be avoided very easily, it can be found in almost all of the world’s largest web applications.
As always, the Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.