SAP Security Notes January ‘19: First Critical Note for SAP Cloud Connector and Mobile Patching
Today is the first SAP Security Patch Day for 2019 and 18 security notes were released, including one that was published during the month after the last Patch Day. This month, several platforms that are not usually part of the Patch Day have Security Notes published, including SAP Cloud Connector and three mobile application bugs that were reported by Onapsis researchers. For some of these platforms it is the first security note ever, and for others we have not seen solved bugs in a while.
Two SAP Security Notes have been tagged as HotNews, as well as two as High Priority. Here’s a list of some of the notes and platforms that have corrections this January:
- A HotNews note (#2696233) affecting SAP Cloud Connector is the first critical note ever published for this platform (there is only one other note for this platform tagged as Medium and published in April 2018, #2614141)
- Another HotNews note (#2727624) that affects SAP Landscape Management with over a year without security flaws discovered in this platform (#2531241 and #2520772, both in November 2017)
- A High Priority note (#2727623) is the first one directly affecting BW/4HANA (there are others that affects both BW and BW4/HANA, such as the Low Priority #2638288, affecting OLAP Queries, or others such us #2545530, #2389764, #2453642)
- Two notes affecting mobile platforms:
- The first one (#2725538) affects SAP Work and Inventory Manager and is the first note ever for SAP Inventory Manager and SAP Work Manager for Android platforms (there is a Security Note released in 2014 that affects iOS version of SAP Work Manager, #2039924)
- The second one is the first note in a few years (#2724059) that affects SAP BusinessObjects Mobile for Android (there is another one published in 2014, #2001778)
In today’s blog post, mobile reported vulnerabilities will be explained in more detail, as well as the most critical notes of the month. SAP Mobile usage is something that has not been widely used and is a growing market, having more users every year adopting mobile usage of its products. It is highly important to take care of mobile clients when included into business operations.
Three SAP Mobile Apps for Android, Fixed
Two Medium Priority Security Notes address the same kind of DoS vulnerability in three different SAP Mobile Apps for Android. Both notes were reported by Yvan Genuer, a Sr. Security Researcher at the Onapsis Research Labs. The first note, #2725538, addresses a security bug in both mobile apps SAP Work Manager and SAP Inventory Manager. Both apps are part of the SAP Enterprise Asset Management (SAP EAM). Before describing some technical details, let’s see what these applications are about to understand their possible impact in a more complete way.
- SAP Work Manager is for workers involved in tasks like the maintenance, inspection or installation of company assets, either in a factory or in the field, eliminating paperwork and allowing both online or offline access directly from a mobile device.
- SAP Inventory Manager is a mobile app to manage inventory. It enables workers to deal with customers orders, track the movement of materials and manage inventory levels. Tasks like physical counting, materials receipts, and everything else related to materials management in a warehouse can be achieved by a dedicated workforce.
The bug for both applications is a function within the software, used by both apps, that is not checking a certain parameter in such a way that allows an attacker to crash the application. In other words, the app suddenly stops and needs to be ended and started again to recover from the attack. Because this exploitation only happens locally, an attacker needs to trick the user to install a malicious app designed to exploit this bug. To achieve a sustained Denial of Service (DoS) attack, a malicious app can send the attack repetitively flooding the service, as is explained in the note, making the vulnerable SAP application unusable.
Note that even by only affecting the availability in some work environments, this kind of attack may result in a severe impact on specific business processes at your organization. For example, imagine one or more crew members unable to use their app and start their daily duties.
A second note, #2724059, is for a security bug in SAP BusinessObjects Mobile for Android, an app to access the SAP BusinessObjects Business Intelligence (BI) platform for accessing reports, documents, dashboards, and metrics for the mobile users workforce that helps to make informed business decisions. The vulnerability with this app is, again, because of a failure to process a parameter in an internal function. The Onapsis researcher in this case found two ways for exploiting it. One is by tricking a user to install an evil app that will crash the app or keep it continuously crashing. The second and easier way for the attacker is by making the user access a specially crafted link against the SAP BI platform that will cause the same effect of crashing the mobile app once or continuously resulting in a DoS attack.
You should update mobile applications to stay secure and SAP also recommends an upgrade to the newer SDKs specified in the security notes, if you use it. On the other hand, there are other workarounds or mitigating measures to address these kinds of attacks: running security software that stops or warns about malicious apps, restricting the installation of apps to a list of approved ones with a Mobile Device Management software and configuring regular updates of the approved apps in mobile. Again: these measures do not eliminate the need for keeping applications updated to fix bugs.
HotNews and High Priority Notes
One of the two HotNews notes is #2696233 that affects SAP Cloud Connector. This note fixes two vulnerabilities, a Missing Authentication with a CVSS v3 Base Score 9.3/10 and a Code Injection with a CVSS v3 Base Score 6.0/10. The missing authentication affects the accesses for functionalities where the user identity is required. This bug allows reading, modifying or deleting both sensitive information and accessing administrative functions that otherwise require high privileges. The Code Injection vulnerability allows an evil actor to inject code that can be run by the application to the point of controlling this agent behavior that may lead to executing unauthorized commands, access or disclosure of sensitive information and Denial of Service.
The SAP Cloud Connector is a piece of software that serves as a link between SAP Cloud applications and on-premise systems. It runs as an agent in a secured network and gives detailed control to set which on-premise resources and/or systems will be accessible to the cloud applications. It also controls which cloud applications can make use of the cloud connector. As one can see, a flow of important information is exposed to the vulnerabilities fixed with this patch. SAP provides detailed steps to upgrade to the fixed version of the SAP Cloud Connector 2.11.3.
The other HotNews note is #2727624, an Information Disclosure bug that affects SAP Landscape Management with a CVSS v3.0 Base Score 9.1/10. It is a very bad one because it allows an attacker to harvest typically high privileged user credentials to be used later for other malicious activities. The impact of this security bug is high in the whole security triad for Confidentiality, Integrity, and Availability. The Security Note needs both to apply the patch and perform manual corrections to remove confidential information recorded into the logs. The best advice is to prioritize the patching and cleaning of such systems.
On other hand, there are two High Priority Security Notes. One is #2724788, that fixes several vulnerabilities in Adobe PDF print library that is used by these SAP products: SAP CLOUD PRINT MANAGER 750 and SAPPDFPRINT 750. Because of the use of the vulnerable libraries SAP products inherit them and the solution is to apply the following detailed patches:
- SAP Cloud Print Manager 750 patch 3
- SAP Cloud Print Manager for ByD 750 patch 3
- SAPPDFPRINT 750 patch 3
- SAPPDFPRINT 760 patch 0
The second High Priority tagged Security Note is #2727623 that fixes a Missing Authorization check in SAP BW/4HANA. In this case, the lack of authorization is in the maintenance of master data and leads to an escalation of privileges. That way a user, in certain circumstances, will be able to abuse functionalities reserved for a particular group, and also to have complete access to restricted information. It is advised to install Support Package 12 for SAP BW/4HANA 1.0 for an automatic fix, or use the provided correction instructions.
Summary and Conclusions
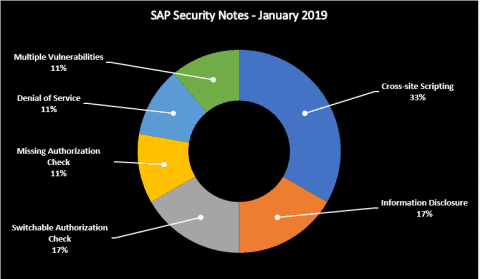
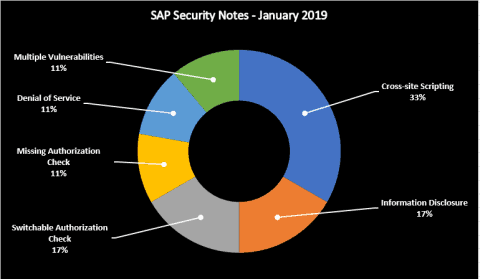
This month there are several relevant SAP Security Notes that, if not addressed, can have serious security implications, including a High Priority Note that affects most SAP customers. Below is a summary of the type of bugs SAP patched this month through its security notes:
SAP recognized Onapsis through a researcher from our research labs, Yvan Genuer, who has “helped SAP improve the security and integrity of their customers’ systems.” As we regularly do at Onapsis, we are working to update the Onapsis Security Platform to incorporate these newly published vulnerabilities. This will allow our customers to check whether their systems are up to date with the latest SAP Security Notes and will ensure that those systems are configured with the appropriate level of security to meet their audit and compliance requirements.
Please follow our ERP security blog or follow us on Twitter for more information about the latest SAP security issues and stay tuned for our year-in-review blog post!
