SAP Security Notes December 2017: What to Know About Re-released ‘Hot News’ Note
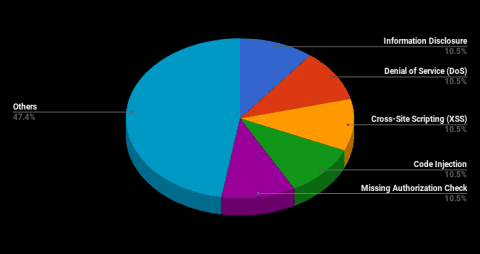
To wrap up 2017, the last SAP Note Tuesday of the year, SAP has released a total of 19 notes this month. Six of these notes have already been released throughout the course of the month with the remaining 13 released today.
During the course of this month SAP published the only Hot News note for the month of December (#2357141). It concerns the re-release of a note linked to a vulnerability discovered by the Onapsis Research Labs. The update in the re-release describes additional manual steps to fix functionality in the SAP GUI which was introduced by a previously released patch. However, we have established that omitting these newly introduced steps does not pose a security risk.
Apart from the re-released Hot News note, SAP published an additional three security notes relating to vulnerabilities found by the Onapsis Research Labs. We have attempted to explain some SAP terms like SAP HANA XSA, SAP GUI for HTML and SAP Startup Services in the context of the found vulnerabilities. You can find the explanation of these concepts and vulnerabilities below.
Three notes were released with high severity this month. Note #2026174 describes a re-release which now contains updated CVSS information. Note #2449757 describes a security flaw in the way that SAP systems trust themselves. Finally, note #2537152 concerns a missing authentication check in SAP Business Intelligence (BI).
The majority of this month’s notes, 15 to be precise, are of a medium severity.
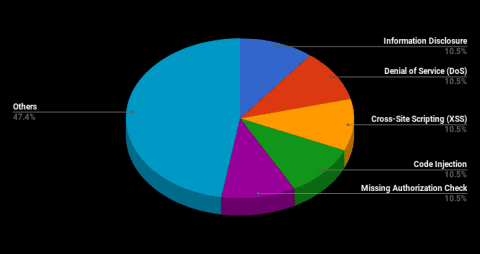
An interesting update is that this month SAP has started to publish CVE numbers in the titles of their security notes and also link to them directly in the note body. This is based on their previous announcement of becoming a CVE authority which is now official, starting this December.
Before going into the details and highlights, there is another medium priority note (#2549983 – [CVE-2017-16687]) concerning information disclosure in SAP HANA User. In this case, an attacker can discover valid users through brute force attacks due to an incorrect error message in the service. Despite the need of installing the patch, it is highly recommended to take into account that more critical bugs have been discovered if SAP HANA Self-Service is enabled. Make sure you address all of them, including SAP Security Note #2424173, which is tagged as Hot News.
Should I worry about the re-released Hot News? How critical is it?
On November 30th, SAP released a Security Note tagged as ‘Hot News’ titled, “OS Command Injection Vulnerability in Report for Terminology Export”. This note is actually a re-released version. Security Note #2357141 was originally published one year ago after being found and reported by the Onapsis Research Labs. When we first talked about the vulnerability in our monthly blog post, we explained that the affected lines of code had been deleted since they were obsolete. Basically, SAP removed all the code that used to run when the report was executed in background. So it is somewhat surprising to see that this security note has been re-released. We will analyze what changed below.
Occasionally, software vendors discover their original patch did not properly solve the bug and they build a second patch to resolve this. When a patch is re-released, it is important to evaluate and implement it from a security perspective. In this case, SAP added a comment in the note claiming they updated the “solution and attachment” information. The solution to patch this vulnerability, which is tagged with a 9.1 / 10 CVSS v3 base score, now contains an additional step. The two steps towards solving the bug are as follows:
- Implement the correction instructions referenced by the SAP note.
- Follow the manual steps in the document “Manual instructions for creating GUI status related to note 2357141.pdf”, which you can find on the SAP customer portal.
Onapsis Research Labs has tested the component and discovered that the previous patch properly solves the bug. Despite securing the vulnerability, it introduced a malfunction in the SAP software. Even though the relevant report is secure, after installing the patch, the report interface then breaks in the SAP GUI by being unresponsive to interactions such as button clicks. New instructions describe how to manually correct this issue to execute the report and stay secure at the same time.
In summary, there are no additional security concerns related to this re-launched security note. If you already applied the original patch, you are protected. If you use this component and reports, it is highly recommended not to delay the note installation, since its usability impact can be easily solved through the new procedure published this month.
What if you didn’t install the patch originally released in 2016? You should do that as soon as possible. The Security Note is tagged as Hot News since a successful exploitation of this vulnerability could lead to escalation of privileges, event data loss or Denial Of Service, if the proper commands are executed. In the following example, we simply execute a ping as a command injection, just to perform a proof of concept:
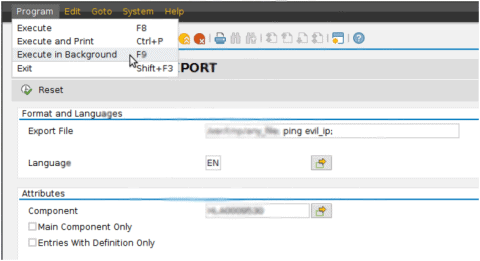
If you go to the server and perform a tcpdump, you will be able to see that the command is executed in the background:
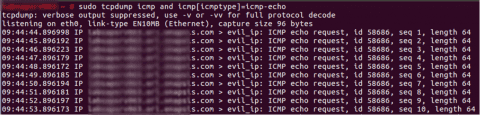
In summary, this is a one-year-old Hot News note that should be addressed with priority, if it wasn’t properly installed originally, but could have less priority if it was originally installed, since the upgrade will only have usability impact.
Security Notes reported by Onapsis Research Labs
All three notes found by Onapsis this month allow the injection of content into parts of the software not equipped to handle it correctly. One of the notes concerns a log injection vulnerability in SAP HANA. More specifically, the bug resides in an SAP HANA application component called XSA. A second bug allows the injection of code into content served to users in the SAP GUI for HTML. Finally, the last note allows a user to be unintentionally redirected by injecting malicious host header information into web requests directed towards startup service ports.
Log injection vulnerabilities in SAP HANA XSA
SAP HANA (high-performance analytic appliance) is SAP’s in-memory (RAM) database platform which enables it to process massive amounts of data very quickly. In SAP HANA versions greater than SP5, a logical software layer was introduced, nestled right on top of the database layer. This first generation application layer is called SAP HANA XS (Extended Application Services) and allows developers to easily interact with the data and functions in the HANA database through HTTP based requests. The XS layer is basically a small footprint application and web server within SAP HANA itself . SAP’s goal was to simplify development for itself, its customers and its partners by providing the development environment “on the box”.
The evolution of XS led to a second generation application layer: XSA (Extended Application Services, advanced model). Even though XSA reuses the strengths of its predecessor, it is a complete redesign of the idea of an on-the-box application server and modeled towards providing tighter integration between HANA on premise and HANA Cloud Platform solutions. From SAP HANA SP11 onwards, the XSA application server offers application developers a rich set of runtimes (Node.js, Java, C++). On top of these runtimes the developers can build web applications, which clients can use and interact with through their browsers.
Two security flaws in XSA were found by Onapsis security researcher, Pablo Artuso. They both concern log injection vulnerabilities and are described together in SAP note #2522510.
The first bug exploits the absence of proper sanitization of user input parameters, while accessing certain HTTP/REST endpoints of the controller service. By sending a custom POST request, unprivileged attackers could forge the audit log with their own chosen log entries.
The second bug applies to UAA (User Account and Authentication services) which is the central infrastructure component in XSA for user authentication. In short, this component facilitates authenticating users. Users log into the web server by performing a certain HTTP POST request. Attackers can forge a login request using bogus credentials, while injecting their own custom text which will be written to the appropriate audit log.
SAP has patched the vulnerabilities. However, as a temporary workaround while you are installing the note, users can keep logging by enabling syslog, instead of local logs.
Code injection vulnerability in ITS
SAP Integrated Transaction Server (ITS) provides the middleware that allows web browsers to interact directly with the SAP server. The interaction happens in the browser through the use of the SAP GUI for HTML interface. With SAP GUI for HTML, transactions can directly be run in the web browser. ITS performs a one-to-one mapping from SAP screen fields in the traditional GUI (text fields, input fields) to the SAP GUI for HTML fields.
Onapsis security researcher Matias Sena found that an attacker with administrator credentials is able to inject malicious code into a ITS middleware component. The malicious code may be subsequently served to an unknowing user, effectively allowing the attacker to control the behaviour of the web application including the execution of client-side scripts (XSS). The vulnerability is described in SAP security note #2526781.
URL redirection vulnerability in Startup Service
The SAP Startup Service provides functions for starting, stopping and monitoring SAP systems, instances and processes. The service runs as sapstartsrv. It fires up the sapstartsrv service SAPHostControl, which monitors the hosts. The services sapstartsrv and SAPHostControl connect ports 5xx13 and 1128, respectively.
Onapsis security researchers Andres Blanco and Nahuel Sanchez found a vulnerability to allow a remote unauthenticated attacker to trick a user into sending a HTTP(S) request with a specially crafted “host header” to the aforementioned ports. After triggering this request the affected services could redirect the affected user into an attacker controlled site.
One more year in SAP Security Notes
To align with SAP this month, we are also adding the CVE number to our SAP Security Notes database. This way our customers can start viewing this information in Assessment Results:
Four researchers from our Research Labs team have been acknowledged by SAP on their webpage this month for their collaboration to keep improving SAP security. As always, we are also working on updating the Onapsis Security Platform to incorporate these newly published vulnerabilities. This will allow our customers to check whether their systems are up to date with the latest SAP Security Notes and will ensure that those systems are configured with the appropriate level of security to meet their audit and compliance requirements.
Today was the last bulk release of the year. We can still expect some more notes before the end of the year. SAP published 271 Security Notes to-date, which would be the lowest amount since 2009, the year of Onapsis’s founding. At the same time this number (close to 300) would confirm what we already analyzed and predicted early this year: SAP Security Security is in a more stable stage. Stay tuned to our blog; we will be publishing more details about the whole year analysis soon.
