SAP Security Notes September 2017: No Hot News updates does not mean you can become complacent
It’s the second Tuesday of the month and another set of SAP Security Notes has been released. Since the previous Patch Day in August, SAP has released 32 notes, including 16 out-of-date and another 16 released this morning. One striking observation is that this is the fifth month in a row without a Hot News note; the highest category for notes based on risk. In addition to that, for the three high-priority notes, two of them are updates for a July note and the other one only affects a single country making the risk much smaller. Based on these facts, we will switch the below blog and instead of going deeper into specific notes, today’s blogpost will consist of smaller descriptions. Lastly, we will give our opinion about what does the absence of Hot News SAP Security Notes mean to SAP customers.
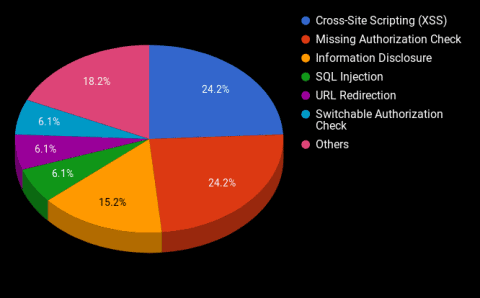
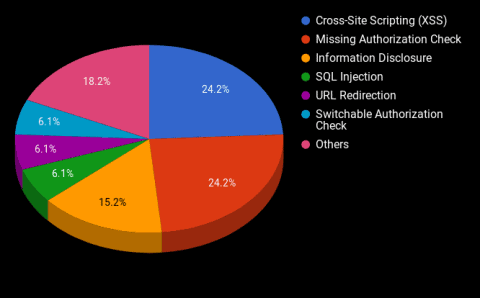
With 32 notes it seems like a will be busy month. However, 9 of the 32 notes (almost 30%) are re-released notes of vulnerabilities already fixed over the past 18 months. The graph below shows the distribution of bug types for this month. One of the notes (#2484707) patches both an information disclosure as well as an authentication check vulnerability. This note therefore contributes to two slices of the pie:
Point Of Sales (POS) ‘several’ updates
Two of the three high priority notes this month are related to SAP Point of Sale (POS) Retail Xpress Server. One of the notes (#2476601) is an update of one already released in July this year, which describes a Missing Authorization Check in functionalities that should have required user identity. As we have written several times in other blog posts, a Missing Authentication Check could lead an attacker to read, modify or delete sensitive information or to directly access administrative or other privileged functionalities.
The second one, (#2520064) has the same title, “Missing Authentication check in SAP Point of Sale (POS) Retail Xpress Server” and the same CVSS score (8.1 / 10 v3). It should be noted, however, this note has more corrections than the original one, including not only added authentication but also added encryption of the communication channel. This note includes the bug described before (#2476601) so you will only need to install this last one.
One more thing you should consider if you are using this product: installing these notes is a manual process that should be implemented in both registers and server at the same time (unpatched registers will be unable to communicate with a patched server).
There’s another note related to POS this month: SAP Security Note #2528596, titled “Hard-coded Credentials in SAP Point of Sale Store Manager”. It has a much lower risk, however with a CVSS v3 Base Score of 3.9 of 10, mostly based on the fact that it is a complex attack with low impact in confidentiality, integrity and availability.
One note…one country?
This month there are two notes that each only affect a single country. As odd as it may seem, it makes complete sense: specific components and applications that only fit within regional or local invoicing/tax requirements can also have vulnerabilities. The other high priority note this month is one of these cases. A Cross-Site Request Forgery (CSRF) vulnerability in Electronic Ledger Management for Turkey 1.0 has been patched in SAP Security Note #2367269.
There is another note that affects only users from one country. SAP Security Note #2497027 fixes a Missing Authority Check in a function for Brazilian invoicing features (Electronic Nota Fiscal, NF-e).
The introduction of Digitally Signed SAP Notes
Fixing what’s broken with an infected patch may create more issues than what an organization began with. Therefore, an important step in the remediation phase is making sure your software updates are coming from an intended and legitimate source, uncorrupted.
To prevent users from patching their systems with maliciously modified SAP note files, SAP is digitally signing their notes to confirm authenticity. In a similar fashion to a web browser verifying an SSL certificate (and giving a warning when seeing unexpected results), SAP users can enable the Note Assistant tool (transaction SNOTE) for note verification. This tool will check the digital signatures of notes to be uploaded, by using an up-to-date version of the SAPCAR tool. A verification failure will finally prevent the extraction of files. SAP Note #2408073 provides more information on the handling of digitally signed notes. Please be aware that for now digital signature verification only works for uploading notes. The possibility of downloading signed notes from the portal is something SAP is planning for release in later months. The information is bundled by SAP in a separate SAP blog post.
SAP, a CVE Numbering Authority
Finally, the SAP Security Response Team has announced this month that it is going to become a CVE Numbering Authority by the end of 2017. Using CVE as a mechanism to disclose patches to vulnerabilities reported by external sources, SAP aims to “facilitate faster patch consumption and transparency for all SAP Customers”. We agree with and respect this decision. It is a great step in to show how this market is further maturing and also shows how SAP security has improved over the past few years.
Opinion: what does the absence of Hot News mean?
We pointed out at the beginning of this post that this is the fifth month in a row without Hot News notes for SAP. What does this mean? Is SAP getting more secure? Before answering these questions (honestly, in our opinion, there are no correct answers), there’s another simpler thing to ask: is this the first time SAP hasn’t published in this category for a long period of time? The answer is no. However, we are close to a record. The last time SAP didn’t publish Hot News for five months in a row was between September 2013 and February 2014 . There’s a bigger period (six months) between July 2007 and January 2008.
And then there is the longest period since SAP started publishing security notes in the early 2000’s: 16 months between August 2004 and January 2006. But that was before Onapsis was created and SAP security developed as a field. Starting in 2007 (the year Onapsis founder Mariano Nunez presented about SAP security at Blackhat and the last year SAP published less than 50 SAP security notes), we are two months away from a breaking record for absence of Hot News publication.
Going back to the big question: is SAP more secure due to the lack of Hot News? It is not accurate to conclude (only because of this fact) that we have a more secure environment. Now that we know this is not the first time this happens it is fair enough to say that this would be a precipitous opinion: what would have happened if we had said the same thing in February 2014? After that we have seen another 40 Hot News notes, including several code injection bugs and the biggest attack in SAP HANA, discovered by Onapsis Research Labs and patched in March this year (last published Hot News so far), you can see the full threat report here.
So, in general, the lack of critical notes patches is not synonymous with security: you never know what is going to happen in the following months.
On the other hand, it is fair enough to say that it could mean something. We are in front of the longer period without critical security notes in almost three years. SAP Security is a more mature field including a bigger research community, a well-recognized market, several improvements from the vendor side (just take a look of the previous sections about this month’s improvements), among others. It wouldn’t be surprising if Hot News updates will be more sparse in the near future.
In conclusion, just because we are getting into a more mature period does not mean we can relax. The fact that it will be more difficult to find a critical bug does not mean that attackers can’t still find them. Other fields such as OS security or WebApp security are clear definitions that there is no “relaxing time” in terms of security and SAP security and business-critical applications security won’t be an exception.
From a customer perspective, this is an opportunity. It is time to go along with the market and the vendor and move your SAP security team to a more mature state. Onapsis Research Labs is already working, adding this month’s notes to our product. Do not hesitate to contact us if you need more help or info about how to patch or secure your SAP systems.

