SAP Security Notes in 2020—an Analysis of an Extraordinary Year
“60% of data breaches are caused by a failure to patch. If you correct that, you’ve eliminated 60% of breaches.” Ricardo Lafosse, CISO of Morningstar, at SecureWorld Chicago.
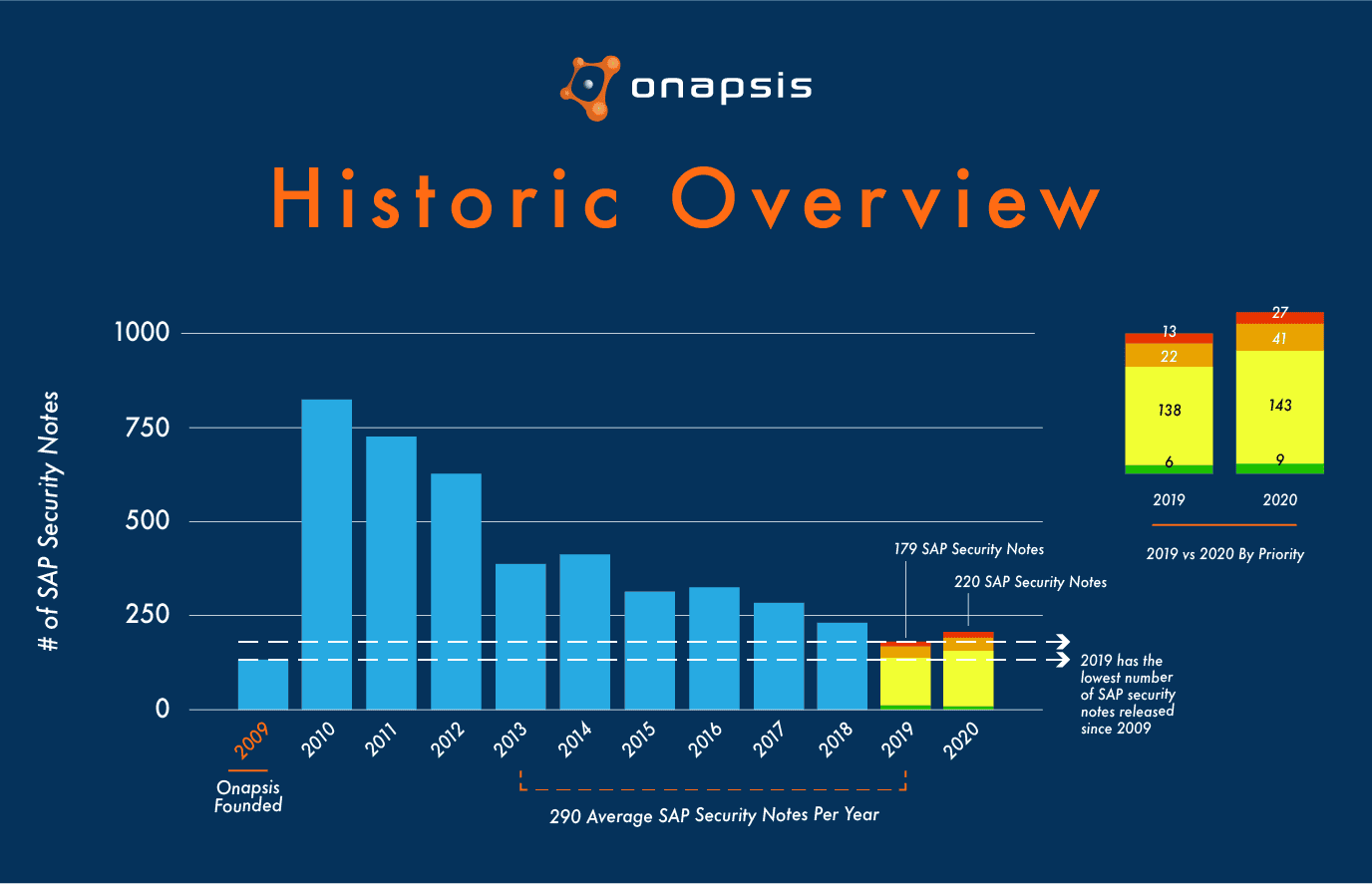
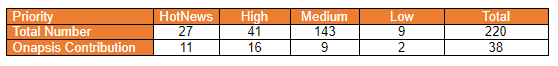
Looking back at the last 10 years, SAP customers could get the impression that SAP systems are getting more secure. With a maximum number of more than 800 released SAP Security Notes in 2010, the number of Security Notes continuously decreased to 179 in 2019. While defining the security of a system by simply looking at the number of released patches must be questioned in general, the decreasing trend was furthermore reversed in 2020. With 220 new and updated SAP Security Notes, the number of released patches increased by 23% compared to 2019. But there is another aspect that should provide more worry—the total number of critical SAP patches (associated with HotNews or High Priority Notes) increased significantly. This important number changed from 35 in 2019 to 68 in 2020, which means an increase by 94%!
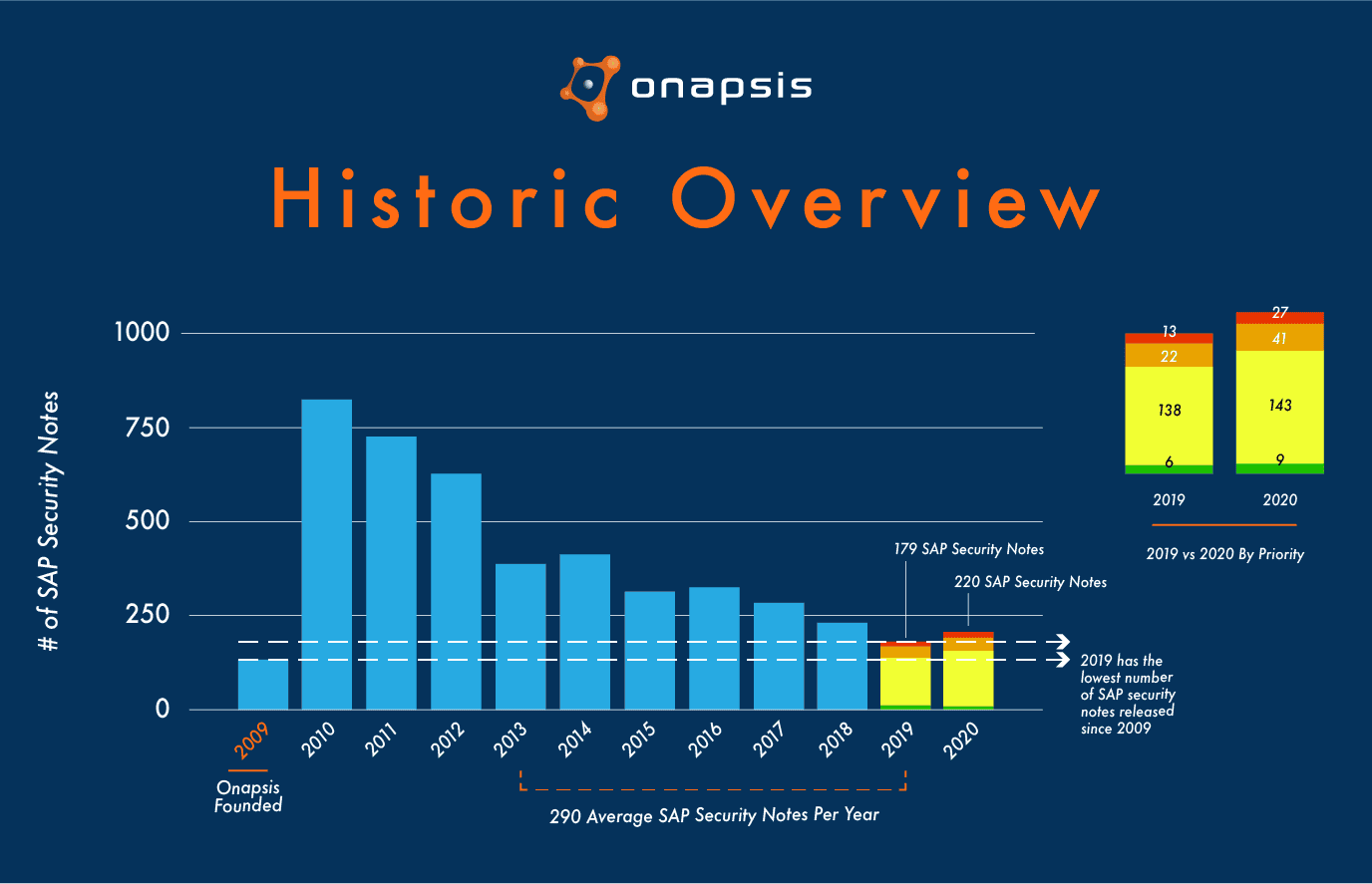
A more detailed analysis of the critical SAP Security Notes shows that the above numbers are not necessarily the result of the continuously growing complexity of SAP landscapes. With SAP Solution Manager (SolMan), SAP NetWeaver AS Java and SAP Business Client, five of the six HotNews Notes that are tagged with the highest possible CVSS score of 10 patch vulnerabilities in “established” SAP components. The sixth HotNews Note that is tagged with a CVSS score of 10 affects a third-party software component that has already been used for several years in SolMan to monitor and manage Java application performance.
Last but not least, it was the Onapsis Research Labs that helped the SAP security team in detecting and solving four of the six vulnerabilities associated with these HotNews Notes. In total, the Onapsis Research Team supported SAP in patching 38 vulnerabilities.
What Are the Lessons Learned From 2020?
Lesson 1: Critical SAP patches should be applied as soon as possible!
Some people still think that the exploit of vulnerabilities in SAP only represents a theoretical scenario. The recognized follow-up activities on the web after the publication of the RECON vulnerability in July 2020 were a hint that this is a very dangerous mindset. In January 2021, Onapsis detected the publication of a fully-functional exploit on the web that abuses CVE-2020-6207 vulnerability targeting SAP SolMan. This vulnerability was properly patched by SAP after Onapsis reported it in March 2020 (SAP Security Note #2890213). A successful attack exploiting this vulnerability would put an organization’s mission-critical SAP applications, business process and data at risk—impacting cybersecurity and regulatory compliance. More details about the exploit can be found here.
Lesson 2: Keep the 24-month rule in mind
SAP is committed to the 24-month rule, stating that critical patches will be provided for all support package levels of an affected component that were released not longer than 24 months ago. Fortunately, SAP does not always strictly follow this rule. Especially in 2020, SAP customers could face a lot of note updates that successively provided patches for older support package levels. Nevertheless, possible impacts of outdated support packages could be:
- There is only a manual, time-consuming workaround available to fix the issue
- An automatic correction is only provided some months after the initial publication of a vulnerability
- There is neither a manual workaround nor a delayed patch provided by SAP
The later two scenarios are especially dangerous. Once a vulnerability has been published, it becomes a race between the attackers and their potential targets with unpatched systems.
Lesson 3: There are more players in the game
In October 2020, SAP released two patches for CA Introscope Enterprise Manager with Security Note #2969828 and #2971638, tagged with CVSS scores of 10 and 7.5. The Onapsis Research Labs reported the corresponding OS Command Injection and Hard-coded Credentials vulnerability some weeks earlier to SAP. This event demonstrates that SAP customers should also consider third-party software in their patch concept. Unlike the CA solution, most of the software vendors have their own delivery channel for installation, updates, and patches, meaning there is more to check than just the SAP Security Notes on the SAP Support Portal.
Conclusion
2020 showed that patching software can be a very important task for an organization and dangerous if not followed properly. The SolarWinds attack demonstrated that it can be easy for attackers to bypass all security measurements established to keep them away from internal networks and systems by compromising the update process of an external software provider.
On the other hand, the three lessons learned from 2020 shows that an organization must continually update its external software to be protected against newly detected vulnerabilities.
It is all the more important that the integrity and quality of the updates are checked by the organization before implementation. SAP supports digitally signed notes since January 2020 to protect its patch process. In order to be best protected when implementing and updating third party software for SAP, the Onapsis Platform provides powerful products to help. With the Assess product, IT and information security teams can continuously assess all SAP systems for missing patches and configuration issues that can leave an organization vulnerable to increasing internal and external threats.
With the Onapsis Transport Inspection capabilities in its Control product, external transport requests are checked against more than 70 criteria that indicate a malicious manipulation of the request. Furthermore, the integrated SAP Custom Code Analysis capabilities in Control checks ABAP Code, as well as SAPUI5(Fiori), XSJS and SQLScript code for more than 160 intentionally or unintentionally implemented vulnerabilities.