Onapsis publishes 12 advisories for Oracle Business Critical Applications
Today we have released 12 new Oracle application advisories which affect two different products: Oracle E-Business Suite and JD Edwards. The advisories include various types of vulnerabilities such as Cross Site Scripting, Denial of Service, Password Disclosure and User Creation. After great success uncovering hundreds of vulnerabilities in SAP systems, our Research Labs are expanding our security advisories to now include Oracle products.
E-Business Suite
This is the first set of advisories we’ve released relating to Oracle E-Business Suite. As a core business application, E-Business Suite manages critical information such as Financial, Human Resources and Customer data. If an organization uses more of the suite’s applications and has larger deployments, there are a greater number of users who have access to the system and who actually use it. All vulnerabilities for this product pertain to Cross Site Scripting attacks (XSS) in different Java Server Page (JSP) components and were fixed in Oracle’s April 2016 Critical Patch Update.
These six advisories are the first of dozens to be released for XSS bugs that we have reported to Oracle for E-Business Suite. As a client-side attack, where the code is executed on the end uses machine, Cross Site Scripting attacks can represent higher risks as there are more users who access the system.
Here is a complete list of advisories with related CVE identification:
- CVE-2016-3439: The vulnerability exists in the JSP file “jtfwcall”. The URL parameter areacode is not sanitized.
- CVE-2016-3439: The vulnerability exists in the JSP file “jtfwcall”. The URL parameter phonenum is not sanitized.
- CVE-2016-3439: The vulnerability exists in the JSP file “jtfwcall”. The URL parameter title is not sanitized.
- CVE-2016-3436: The vulnerability exists in the JSP file “jtfLOVInProcess”. In that page, arbitrary URL parameters can be provided. For example “test” parameter and its content it is not properly sanitized.
- CVE-2016-3437: The vulnerability exists in the JSP file “jtfwtpoa”. The URL parameter “state” is not properly sanitized.
- CVE-2016-3438: The vulnerability exists in the JSP file “czJradHeartBeat”. The URL parameter appletpost is not sanitized.
JD Edwards
The other six advisories relate to JD Edwards – some of them have a relationship with JDENet protocol and others with the Server Manager.
JDENet is a network communication middleware that performs network communications workstation-to-server and server-to-server. It is used to call remote functions, and to authenticate users as well as transmit information between hosts inside a JD Edwards environment. The Server Manager is the server responsible to manage all the JDE Servers. The Server Manager uses the Java Management Extensions (JMX ) technology to connect to all the JD Edwards servers with an agent. This technology relies on Managed Bean and the standard Remote Method Invocation (RMI) protocol.
Listed below are all vulnerabilities on JD Edwards were fixed in the January 2016 Critical Patch Update, as well as a technical description of the most important ones:
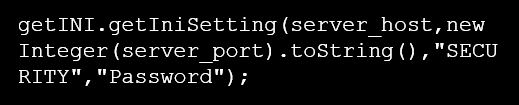
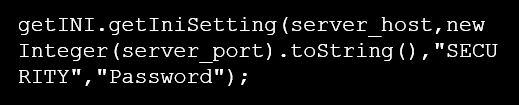
- CVE-2016-0422: This vulnerability exists in the method getIniSetting. An attacker could use it to retrieve the JDE.INI information without authentication. For example, in section “Security” the parameter “password”. This method uses four parameters with host, port, section and parameter name:
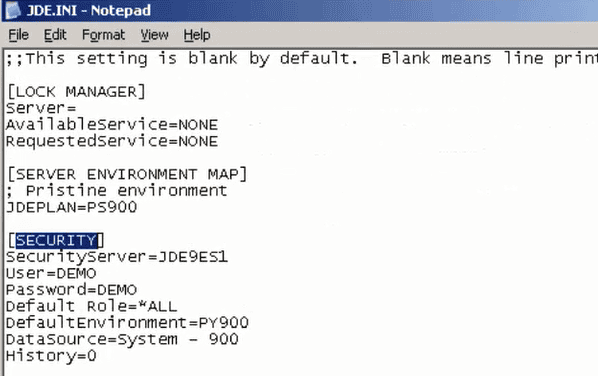
The following screenshot depicts a real scenario in which an attacker could get the administration password with access to JDE Application and JDE Database. The following image is a JDE.INI example, depending on the JDE version the password will be in plaintext or encrypted.
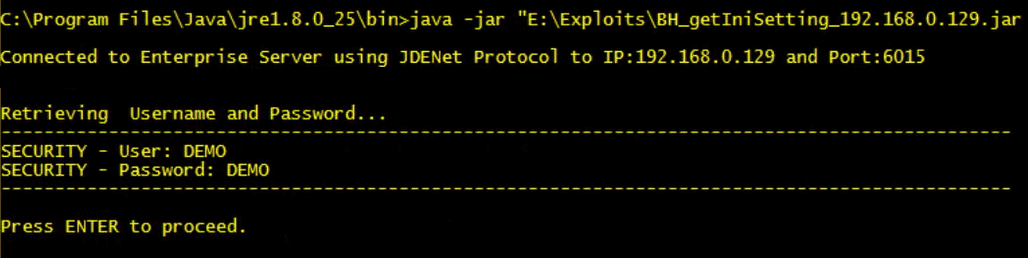
An attacker could use a script to get JDE.INI information such as user and password.
This vulnerability completely affects the confidentiality and integrity in JD Edwards applications and the attacker could compromise the availability too.
To mitigate this vulnerability, implement the January 2016 Critical Patch Update, as well as firewall restrictions to JDENet ports.
- CVE-2016-0424: This vulnerability could be exploited when someone in the network sends a JdeMsg with 8 as type, the Enterprise Server automatically shuts down the JDENet listening processes, without control or authentication.
JdeMsg msg = new JdeMsg(8,1,0);
After the message is sent, any user could interact or login into the JD Edwards application. The following is a real scenario with a JDE shutdown.
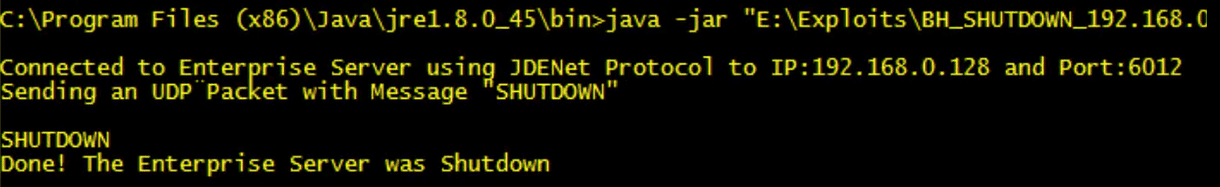
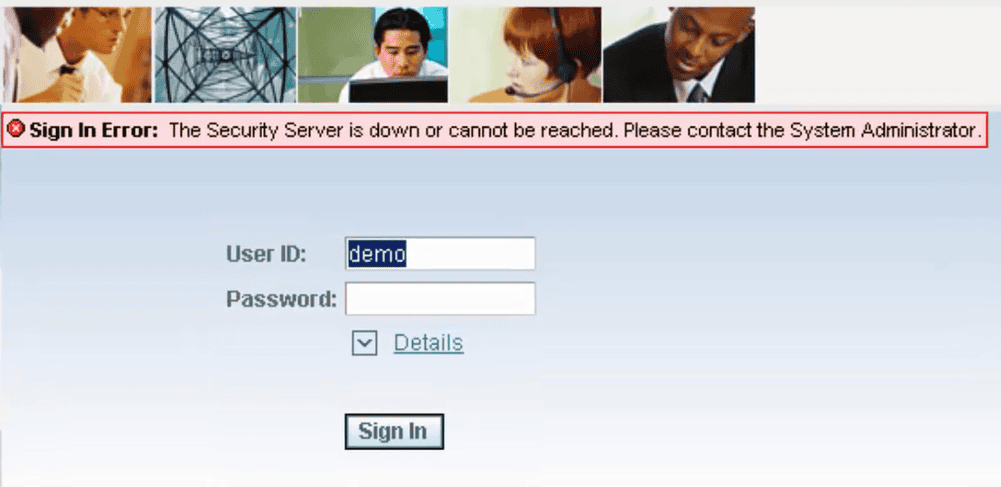
This vulnerability completely affects the availability. After the attack is properly performed, all servers except the database need to be manually restarted. If the attacker schedules a script to shutdown the server once the server is up again, it could be a huge problem for an organization. This is because it will cause more downtime and will require a lot of manual work to solve the problem.
To mitigate this vulnerability, implement the January 2016 Critical Patch Update, as well as firewall restrictions to JDENet ports.
- CVE-2016-0421: The Server Manager uses the Java Management Extensions (JMX ) technology to connect to all JD Edwards servers with an agent. This technology uses Managed Bean and the standard Remote Method Invocation (RMI) protocol. The vulnerability can be triggered by invoking the method shutdown.
- CVE-2016-0420 This vulnerability can be exploited invoking the methods ‘addLocalUser’ and ‘grantUserRole’ to create the user, password and assign the roles. With this new user, it is possible to log into Server Manager and manage all the servers.
- CVE-2016-0425: This vulnerability could be exploited by invoking the method ‘getEncryptedPasswordForUser’ without any authentication mechanism, using it to get the encrypted
- CVE-2016-0423: This vulnerability could be exploited by sending a message with two end of file packets. The Enterprise Server will automatically shut down, without control or authentication.
All advisories mentioned in this post can be downloaded here. As always, all of our published advisories have a patch available to ensure that your systems are up-to-date, and fully protected from cyber attacks.

