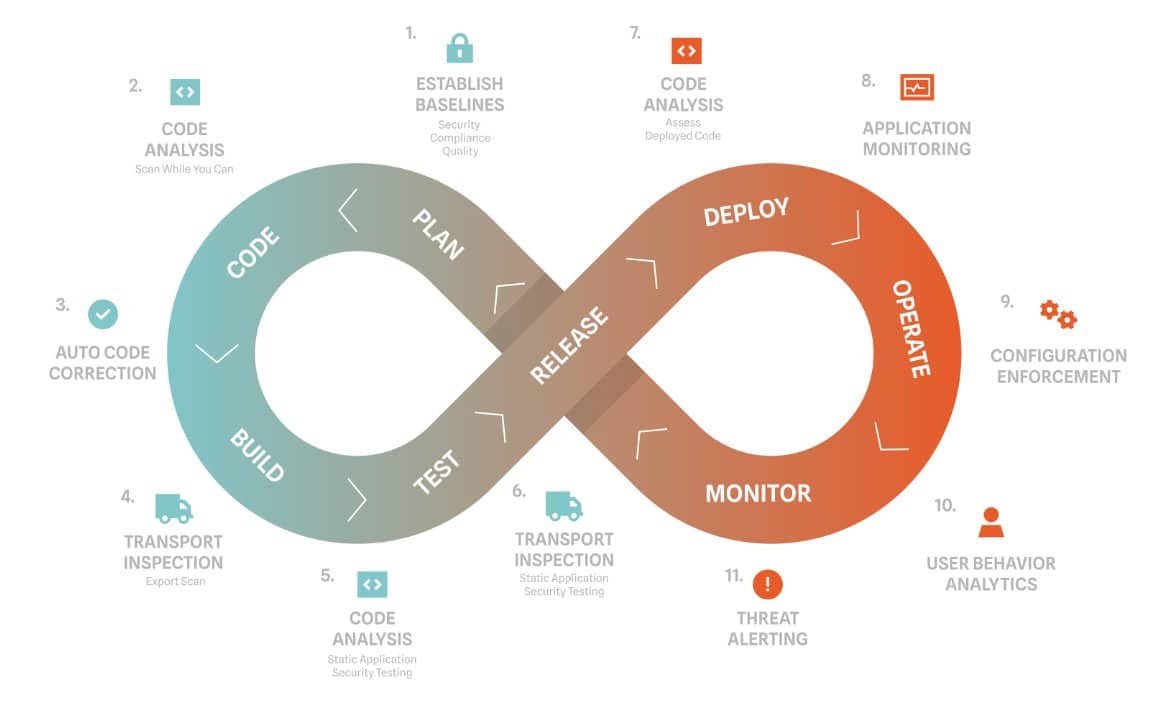
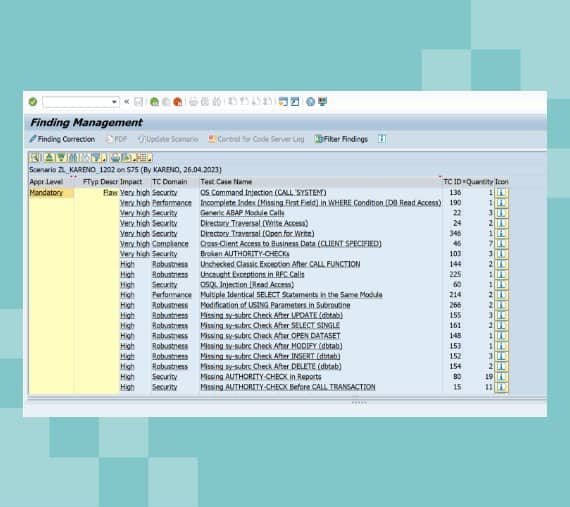
SAP Transport Management (SAP TMS) is more than just a tool—it’s your lifeline for managing the flow of objects and changes across SAP systems. By orchestrating this movement, SAP Transport Management ensures system consistency and prevents potential conflicts that could arise from uncoordinated modifications.
At its core, SAP TMS serves as the vehicle for organizations to effectively manage changes to their SAP landscapes. This critical function allows users to implement updates smoothly, minimizing disruptions to their business processes. The process begins in the development system, where changes are first introduced. From there, SAP TMS facilitates the organized migration of these changes through testing environments and, ultimately, into production systems.
This structured approach yields several key benefits. First and foremost, it acts as a safeguard against errors and data inconsistencies that could otherwise plague systems updated in a haphazard manner. Moreover, SAP TMS doesn’t just focus on functionality—it also increases cybersecurity. With its robust measures to protect against unauthorized access and potential data breaches, it becomes an integral component of an organization’s overall cybersecurity strategy.
SAP Transport Management is not beneficial when moving data—it helps to ensure the integrity, security, and continuous improvement of your SAP solutions. As businesses increasingly rely on their SAP systems for critical business processes, the role of SAP TMS in maintaining a stable and secure environment cannot be overstated.