Dangers in SAP Transport Management: An Intro
This blog post is part of a series about the dangers in SAP Transport Management.
Across industries, organizations implement software solutions, IT controls, policies and procedures to secure their mission-critical applications. Understandably, production systems take priority as they house real customer data and other business-critical information. While dev, test and QA systems are not ignored, they are not always treated as equal. The permissions granted on these systems to developers and others often exceed those granted on production. These differences in access levels are often appropriate, following the “least privileged” model for access management. It must not, however, be overlooked that dev, test and prod systems are interconnected.
Often, we think of interconnected systems as a server reaching out to a database, perhaps an ordering system on a website, checking against inventory in another system. A customer purchases a product, and the inventory is reduced. What happens on one system affects another; this is “interconnected risk”. There are multiple ways to address interconnected risk, as different types of risk are carried when you link systems. This could be knowing what class of data is flowing between systems, access to data after it leaves a source system, or the ability for an attacker to traverse these systems upon successful exploitation. Each of these takes is worthy of its own post. This blog series, however, will focus on the interconnectedness of SAP systems, specifically in the context of transports used in the development cycle, and the risks within that process.

Why Focus on Transports?
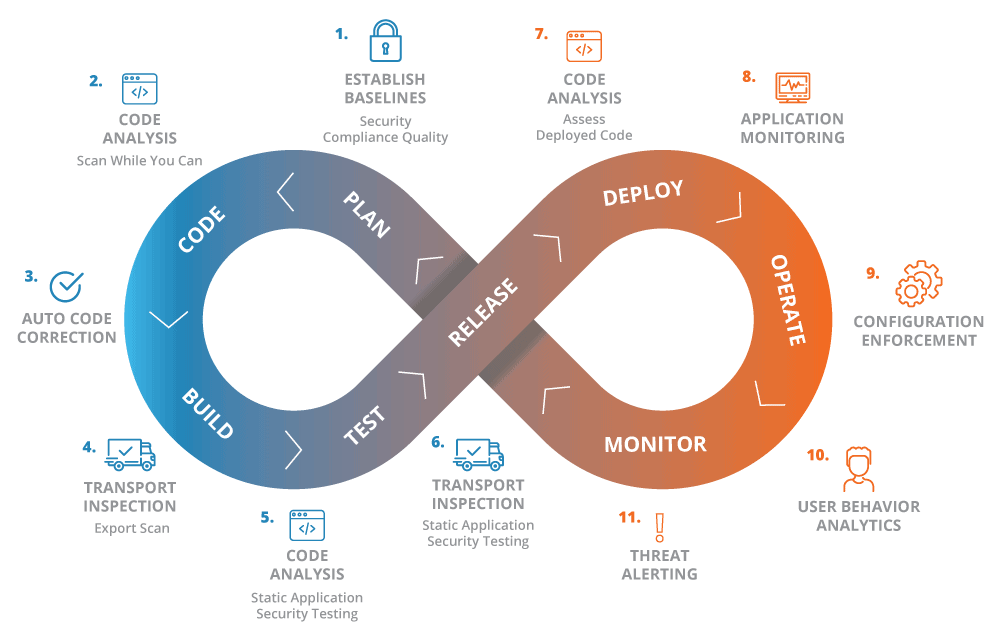
Part of DevSecOps is to bring security to each step of the DevOps process, and more and more organizations are adopting this process. Within the diagram above, SAP transports are used at multiple points in the development cycle. And here lies an often overlooked area where opportunity lies for exploitation, even with appropriate permissions in place. An attacker can leverage a number of techniques on dev systems, to compromise production systems resulting in loss of confidentiality, integrity and availability.
Throughout this series we’ll take a look at techniques like circumventing authority checks, manipulating job management and more. Further, we’ll show what to monitor for within SAP Transports to detect unauthorized actions. Stay tuned and check back for upcoming posts in this series.
