Stress-Free System Updates:
7 Security Best Practices
for SAP Transport Management
What is SAP Transport Management?
SAP Transport Management (SAP TMS) is more than just a tool—it’s your lifeline for managing the flow of objects and changes across SAP systems. By orchestrating this movement, SAP Transport Management ensures system consistency and prevents potential conflicts that could arise from uncoordinated modifications.
At its core, SAP TMS serves as the vehicle for organizations to effectively manage changes to their SAP landscapes. This critical function allows users to implement updates smoothly, minimizing disruptions to their business processes. The process begins in the development system, where changes are first introduced. From there, SAP TMS facilitates the organized migration of these changes through testing environments and, ultimately, into production systems.
This structured approach yields several key benefits. First and foremost, it acts as a safeguard against errors and data inconsistencies that could otherwise plague systems updated in a haphazard manner. Moreover, SAP TMS doesn’t just focus on functionality—it also increases cybersecurity. With its robust measures to protect against unauthorized access and potential data breaches, it becomes an integral component of an organization’s overall cybersecurity strategy.
SAP Transport Management is not beneficial when moving data—it helps to ensure the integrity, security, and continuous improvement of your SAP solutions. As businesses increasingly rely on their SAP systems for critical business processes, the role of SAP TMS in maintaining a stable and secure environment cannot be overstated.
How does SAP Transport Management Work?
SAP Transport Management manages the movement of software and configuration changes. These changes need to cascade across different SAP systems, including development, testing, and production systems. Here’s an overview of how it works:
A transport request is created to package the changes made in a development system. This request includes all the required details. It includes the objects that were altered, the SAP version, and the target system to which the changes will be applied.
The transport request is reviewed and approved by relevant stakeholders, such as developers, QA personnel, and project managers. Once approved, the request is released to be transported to the target system.
The transport request is transported to the target system, where the changes are applied. The target system could be a testing or production system.
After the changes are applied, they are tested to ensure they work as intended and don’t impact other areas of the system.
Once the changes have been tested and verified, the transport request is closed.
Why Should You Use SAP Transports?
Part of DevSecOps is to bring security to each step of the development lifecycle–more and more organizations are adopting tools like SAP Transport Management. Transports can be used at multiple points in the development cycle as shown in the diagram. Because transports are used at multiple points in the development cycle, it can be an overlooked aspect of SAP security, creating opportunities for exploitation across your SAP applications. Even with appropriate access management in place, an attacker can leverage a number of techniques to compromise production systems. This often results in loss of confidentiality, integrity, and availability.
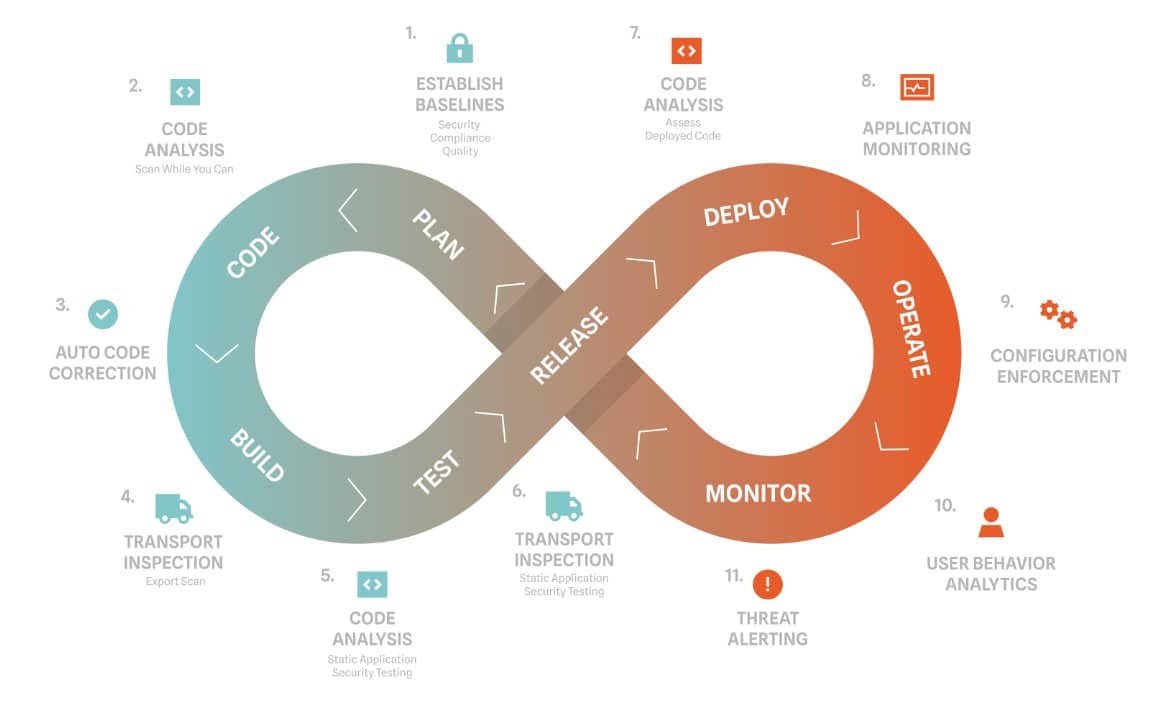
What Security Teams Should Know about SAP Transport Management
Managing enterprise systems is an unending quest to balance optimization and automation with risk management and data security. There are several known security risks associated with SAP Transport Management, including:
To mitigate these risks, it’s important to implement proper access controls, use secure transport protocols, monitor and audit transport activities, and ensure proper segregation of duties. Additionally, implementing encryption and digital signatures can help ensure the integrity and confidentiality of transport requests.
How to Implement the 7 Security Best Practices in SAP Transport Management?
Here is a step-by-step guide on how to implement the best practices for securing SAP Transport Management and other enterprise business applications:
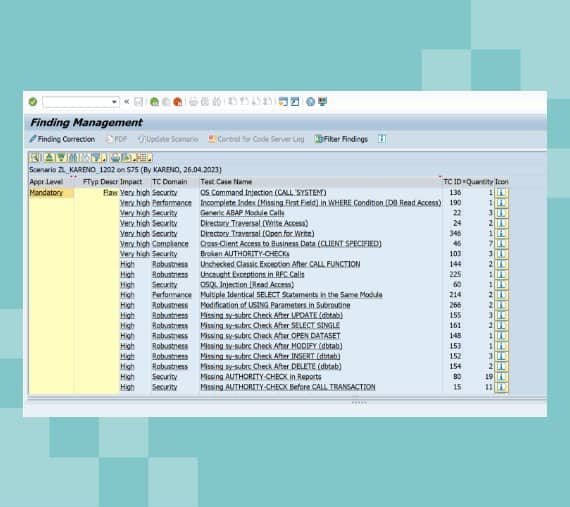
Onapsis for SAP Transport Management
Organizations need to implement the right security solutions to protect their SAP backend development system holistically against cyberattacks. If not properly protected, the SAP Transport Management system represents a significant data security and continuity risk as we have addressed above.
Onapsis Control automates the monitoring of changes that are leaving the development system and provides additional approval workflows for critical situations. Control is ideal for enterprises who want to:

Ready to eliminate your SAP cyber security blindspot?
Let us show you how simple it can be to protect your business applications.
