SAP Security Notes July ‘18: Re-released Hot News and the Rise of Security Notes

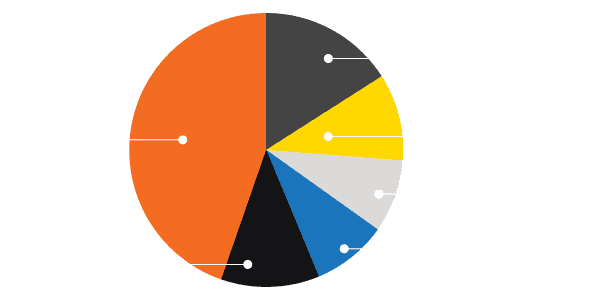
Another second Tuesday of the month has arrived and SAP has brought us a fresh new set of security notes. 15 new notes were published today, summing up a total of 34 security notes released since the last Patch Day. Five notes in total (15%) are tagged as High Priority or Hot News. With the exception of four Low Priority notes, all remaining notes this month are of Medium Priority (25).
The last time there were more than 30 security notes was seven months ago.
These 25 Medium Priority notes for July total 75% of the monthly package. They are mostly new ones, including #2624762, that solves a vulnerability for SAP BusinessObjects reported by Onapsis. It is a Reflected XSS that affects the SAP Crystal Reports, one component of the SAP BusinessObjects Business Intelligence platform. For technical details about this vulnerability, please read on for fixing the Onapsis reported BusinessObjects vulnerability.
This month, the only SAP Security Note tagged as Hot News is, again, re-released. It was published last month and, as we already talked about in our last SAP Security Notes June ‘18: What to Do with Critical Re-released Notes?, customers need to install it again. We will dig deeper into this specific case that happens twice this month: Hot News and High Priority notes released this month.
Below is a chart showing this month’s notes vulnerability category distribution:
 A Fix for the Onapsis reported BusinessObjects vulnerability
A Fix for the Onapsis reported BusinessObjects vulnerability
The Onapsis Research Labs has been focusing on SAP BusinessObjects for many months and this month’s SAP Security Note #2624762 fixes one of the vulnerabilities (Medium Priority, CVSS: 6.1) we reported to SAP recently. It is a Reflected XSS that affects the SAP Crystal Reports, one component of the SAP BusinessObjects BI platform.
In this reflected XSS found by Onapsis, it allows an attacker to manipulate an HTTP request by adding, for example, an arbitrary script. Due the lack of server’s request sanitization, the script is executed on the user’s browser allowing the attacker to manipulate the showed information or another malicious activity. This XSS is not stored in the server either in the client. Such vulnerability, with a CVSS score of 6.1, may allow an attacker to modify the web content, steal users’ information of his/her session and impersonate the user with the same permissions on the system.
Details on IGS and Gateway vulnerabilities
Today’s monthly security notes come with fixes to four vulnerabilities reported by security researcher Yvan Genuer, just before he joined the Onapsis Research Labs last May. Those were tagged as Medium Priority. Three of these affect SAP IGS and one affects SAP Gateway.
Since we have access to the details of these vulnerabilities we are able to analyze them in detail below.
- [CVE-2018-2438] Denial of Service (DoS) in SAP Internet Graphics Server (IGS) (#2644238) – This is a group of five similar Denial of Service (DoS) vulnerabilities in SAP IGS that can be exploited remotely and anonymously. Because of insufficient validation SAP IGS may process remote anonymous invalid requests that may result in long response delays, service interruption or a crash. This impacts service availability. In order to implement the solution, the user has to apply the patch level indicated in the note.
- [CVE-2018-2439] Code Injection Vulnerability in SAP Internet Graphics Server (IGS) (#2644147) – This note addresses a set of three similar code injection vulnerabilities in the IGS that are remotely exploitable, without authentication and could lead to open redirect vulnerability, for example forcing an SAP administrator to access an external website. With them an attacker is allowed to inject arbitrary code that can be executed by the application thus being able to manipulate the behaviour of the application. The impact cover unauthorized execution of commands, sensitive information disclosure and denial of service. As with the previous one, to implement the solution the user has to apply the proper patch supplied.
- [CVE-2018-2437] Unauthorized Command Execution in SAP Internet Graphics Server (IGS) (#2644227) – This vulnerability allows an attacker to externally trigger IGS command executions through the multiplexer RFC listener. This can lead to information disclosure and malicious file insertion or modification. The solution provided is to consult the note #1425765 and create a narrow reginfo entry to avoid external access, also to use the latest SAP Internet Graphics Server (IGS) version available.
- [CVE-2018-2433] Denial of Service (DoS) in SAP Gateway (#2597913) – In this case, the security researcher found two ways of provoking a Denial of Service in SAP Gateway remotely and without authentication, either by crashing or flooding the service. This way the attacker prevents the users from accessing the service. The SAP Gateway is the service that allows connection to the system from other systems or mobile devices within other uses. In order to fix this vulnerability it is advised to apply the proper version and patch level of SAP Gateway as stated in the note.
Hot News and High Priority Notes Released This Month
The only Hot News security note for this month is a re-release of the #2622660, the one that includes periodic security updates for third party web browser controls delivered with the SAP Business Client. The two controls for displaying HTML content are for Internet Explorer and for Chromium. The new security fix for this month is with the open source Chromium, and as we explained in our last month’s blogpost in order to keep the system protected it is required to install the latest SAP Business Client available. Yes, this is the kind of re-released note that has to be installed.
Below, this month’s four High Priority notes are discussed:
- Missing Authorization Check in Printworkbench (#2604054) – The SAP Print workbench is a central development environment for creating standardized outgoing correspondence present in SAP_ABA component from 700 up to 75C. The impact of this vulnerability, caused by the lack of authorization checks, may allow an abuse of functionality restricted to a particular user group and accessing or modifying restricted data. It affects data integrity and confidentiality. The corrections instructions and note must be followed to fix these risks.
- List of Diagnostic Agents can’t be retrieved due to enforced security at API level (#2546807) – In the SAP Solution Manager configuration, due to an improper security enforcement, it is not possible to complete a SolMan configuration. The impact of this is the inability to complete a correct Solution Manager configuration because of lack of information from the list of the mentioned Agents. To fix this problem, follow note #2544779.
- [CVE-2018-2408] Improper Session Management in SAP Business Objects -CMC/BI Launchpad/Fiorified BI Launchpad (#2537150) – This re-launched Security Note adds coverage of the vulnerability for other versions and patch levels of the SAP BusinessObjects Enterprise platform. The impact of the vulnerability is on confidentiality, an attacker will be able to abuse a user session even after the user has changed the password. The security issue may be fixed applying the corresponding patch.
- Denial of Service (DoS) in Internet Sales (#2629535) – Despite the fact that this security note is a re-release of the original, issued earlier this month, it solves a known, old ([2014-0050]) third-party software vulnerability in Apache Tomcat and JBoss Web used by SAP Internet Sales / E-Commerce / Web Channel. A Denial of Service like this affect systems availability. This bug in MultipartStream.java allows remote attackers to cause a denial of service (infinite loop and CPU consumption) via a crafted Content-Type header, crashing or flooding the service. Customers have to implement corrections instructions and apply the corresponding note.
Conclusion
As always, we are working on updating the Onapsis Security Platform to incorporate these newly published vulnerabilities. This will allow our customers to check whether their systems are up to date with the latest SAP Security Notes and will ensure that those systems are configured with the appropriate level of security to meet their audit and compliance requirements. Please check our website for additional information on all topics discussed in this blog post.
