SAP Security Notes Feb ‘18: Onapsis Helps SAP Patch Several Vulnerabilities in HANA XS Advanced
Today is the second Tuesday of February and our readers already know that this means today SAP released its monthly security notes. Below you will find our monthly report on how to improve your ERP security and take care of your most critical information.
SAP released 12 new security notes today, summing up a total of 26 notes, taking into account the ones published after the second Tuesday of last month.
Five notes are tagged as High Priority and should be patched as soon as possible. SAP published two security notes covering several vulnerabilities found by the Onapsis Research Labs and one of them, #2589129 security vulnerabilities in SAP HANA XS Advanced (XSA), was tagged as High Priority. This particular note actually combines a total of eight vulnerabilities reported by Onapsis. We will discuss the notes in the next section.
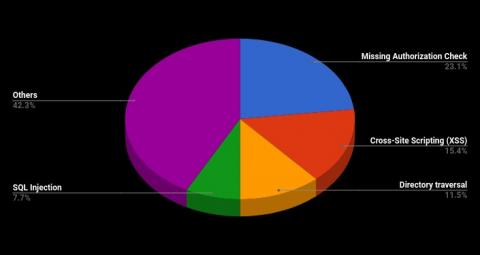
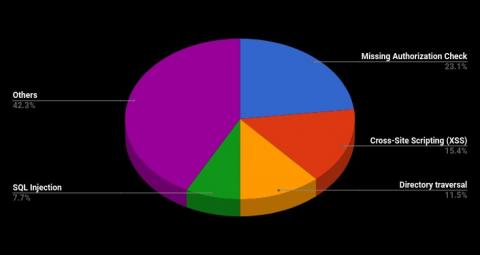
The majority of this month’s notes, nineteen to be precise, are of Medium Priority. Below is a chart showing this month’s attack category distribution.
Reported by Onapsis: Several Bugs in XSA and an XSS in Java
Eight vulnerabilities reported by Onapsis concerning SAP HANA XSA are bundled together in SAP note #2589129. The other note reported by the Onapsis Research Labs, concerning a Cross-Site Scripting bug in AS Java (#2560741), will also be highlighted here.
In our note analysis blog post in December 2017, we explained what SAP HANA XSA is and what SAP’s intention was when creating it. SAP wanted to simplify writing applications for itself, its customers and its partners by providing a development environment “out of the box” in the form of SAP HANA XS. SAP HANA XSA (extended application services, advanced model) is the evolution of XS, providing runtimes on top of which developers can build web applications. It is in XSA that SAP has yet again published a security note (#2589129) solving several bugs originally reported by the Onapsis Research Labs.
SAP has tagged this security note as High Priority. Onapsis researchers have analyzed possible exploitation scenarios and discovered that more than just confidentiality can be compromised. Through the use of obtained credentials, attacks can be leveraged that affect integrity and availability too. When viewing the note, a customer would be able to find details of all the bugs that were corrected in the new release of SAP HANA XSA. Despite the fact that SAP included each CVE with its proper CVSS risk value, there are two specific vulnerabilities that are a lot more critical than the others.
The first one is a vulnerability in which a remote attacker, who obtained access to the low-privilege account of a controller user, and who has the SpaceAuditor authorization, could retrieve database credentials of the technical users that are used by the system to connect XSA applications to the database (only in the space where controller-user has the SpaceAuditor role). When successfully executed, credentials in plaintext and other sensitive information could be obtained. To illustrate, the diagram below shows the typical MVC pattern that SAP uses as the base architecture for XSA. It is the controller layer which exposes the vulnerabilities.
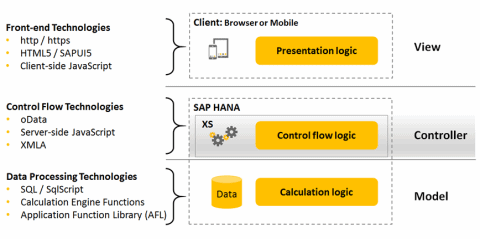
Onapsis researchers Nahuel Sánchez and Pablo Artuso found a number of ways in which malicious clients are able to approach the XSA APIs exposed by the controller, leading to the unintentional exposure of privileged user credentials. The key in all attacks is carefully choosing the parameters to be passed to the vulnerable APIs, which in various cases causes different information to be prompted as a response. The information that could be exposed in this way concerns a variety of sensitive data: HANA database usernames and passwords in plain text, application client secrets and application public keys.
These diverse approaches to exploit the XSA API, in this particular attack, all have something in common: access to the database can be obtained by abusing a user account with the least privileged role assigned in the HANA XSA identity provider. Successful exploitation could result in the ability to query (at least some) database tables, locking users, deleting or updating services or updating service configurations. The exploit could impact confidentiality, integrity and availability on the system under attack, which leads to high risk. This bug was reported with a high CVSS score of 9.1/10, even though the final value published by SAP was lower.
The second critical bug, reported by Onapsis with a CVSS v3 score of 8.6/10, is a blind boolean-based SQL-injection vulnerability. This vulnerability is bundled together with the other HANA XSA vulnerabilities in note #2589129. The controller, mentioned earlier, exposes several APIs which all interface with numerous services. In particular, there is a service inside the exposed API which allows any person without authentication to inject SQL commands inside statements sent to the API, changing the normal execution of the vulnerable service. These SQL-queries are wrapped in web requests sent to the API. Blind SQL-injection is, “a type of SQL injection attack that asks the database true or false questions and determines the answer based on the application’s response.” In this case, the “blind and boolean-based” aspect of the SQL injection is due to the fact that the attacker iterates over the database content by guessing text values through specially crafted SQL-queries containing a boolean expression. For each iteration the API will return either a result (expression evaluates to TRUE) or no result at all (expression evaluates to FALSE), which allows the attacker to deduce all the text content of the table without literally retrieving that content. As a result, a remote unauthenticated attacker is able to read any arbitrary system view.
Based on the affected component (SAP HANA XSA), the size of the note (eight bugs in one) and the impact (high impact on confidentiality, integrity and availability), we believe this SAP security note should be treated with the same priority as any other critical bug.
Finally, another note was published that patches another one of the Onapsis reported bugs. In note #2560741, SAP discloses a vulnerability in the SAML 2.0 service provider of Application Server (AS) Java. SAML, which stands for Security Assertion Markup Language, is a standardized way of communicating authentication and authorization data. In the case of SAP, it is used to streamline authentication by configuring AS Java as an SAML 2.0 service provider. As a service provider, user authentication can be offloaded to an identity provider, which can then be deployed for single sign-on. Onapsis researcher Gaston Traberg has found that the SAML 2.0 service provider contains a classic cross-site scripting (XSS) vulnerability. The service provider serves received web requests right back to the user without proper sanitation. This bug could be used by an attacker to construct a URL which executes custom JavaScript code when the URL is accessed. By tricking an already authenticated user into clicking the URL, arbitrary JavaScript code could be executed on the victim’s machine.
Monthly High Priority Notes
A total of five High Priority notes were published this month. The one reported by Onapsis, which bundles a total of eight notes, has been discussed and now we will cover the remaining four High Priority notes.
1 and 2. Two High Priority notes have been published in tandem this month (notes #1584573 and #1977547). These notes are a re-release of an old note published as far back as 2011. It concerns an SQL-injection vulnerability in the component BC-UPG. The latter mentioned note is auxiliary to the first, in that it supplements correction instructions for it. It was also released before, in 2014. The supplement is only relevant for newly installed systems, or systems which have never been changed using Software Update Manager 1.0 or 2.0 in the years since the first note was created. SAP found that the correction instructions were not fitting in all situations, which led to the creation of the auxiliary note. We advise you to take this opportunity to review the necessity of the note for your specific situation.
3. The SAP note #2525222 also bundles multiple vulnerabilities within a single publication. The note provides an overview of no less than 14 security bugs, all found in the SAP Internet Graphics Server (IGS). The IGS is an engine used by SAP for generating visual components like graphics or charts. The SAP note shows that IGS has been exposing a wide variety of bugs: Denial of Service (DoS), Cross-Site Scripting (XSS) and Log Injection attacks, amongst others. Nevertheless, only one High Priority vulnerability (CVE-2018-2394) is mentioned. It constitutes a DoS attack which allows an unauthenticated attacker, “to prevent legitimate users from accessing the SAP IGS, services and/or system files”. The remaining bugs are of medium severity.
4. The final High Priority note this month is #2565622. It concerns the SAP NetWeaver System Landscape Directory (SLD). SAP SLD is a central storage component for information about all installable and installed components of a system landscape. Like many other services, users can interface with the SLD through client APIs. This particular vulnerability seems to lie within the Java Naming and Directory Interface (JNDI), which is a Java API which can be approached by clients to look up data; in this case about the SAP landscape. Due to the bug, no authentication checks are performed for functionalities which should require user identity. This means that unauthenticated users could interact with the SLD in such a way that sensitive data could be unintentionally exposed.
Conclusion
After a calm first month of the year, from an SAP note perspective, we are now seeing a more usual number of monthly notes again. This is mainly due to the fact that SAP has bundled multiple vulnerabilities into fewer notes. This month, Gaston Traberg, Nahuel Sánchez, Martín Doyhenard and Pablo Artuso from our Research Labs have been acknowledged by SAP on their webpage for their collaboration to keep improving SAP security. As always, we are working on updating the Onapsis Security Platform to incorporate these newly published vulnerabilities. This will allow our customers to check whether their systems are up to date with the latest SAP Security Notes and will ensure that those systems are configured with the appropriate level of security to meet their audit and compliance requirements.
