Log4j Vulnerability: Threat Intelligence and Mitigation Strategies to Protect Your SAP Applications

On Thursday, December 9, a critical vulnerability (CVE-2021-44228) in Apache log4j, a widely used Java logging library, was made public. Some are calling it “the most serious vulnerability they have seen in their career.”
Since we became aware of Log4j, Onapsis has been working around the clock to understand the impact of this vulnerability on some of the most widely used SAP products. Onapsis and SAP partnered together for a session on protecting SAP applications from the threat of Log4j vulnerability. Read on for the highlights or watch the full webinar here.
Watch Now: Log4j Vulnerability: Threat Intelligence and Mitigation Strategies to Protect Your SAP Applications
How Log4j Works
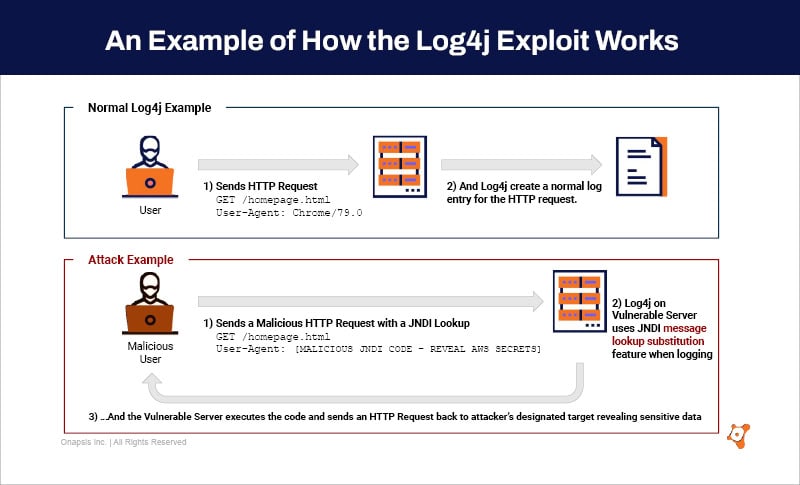
Log4j (CVE-2021-44228) is a remote code execution (RCE) vulnerability that enables threat actors to execute arbitrary code and take full control of vulnerable devices. In a normal flow, a user would send an HTTP request to a web server, the web server would react, invoking a logging library, and write a log. On a vulnerable system with a malicious request, the same request goes to the web server, but inside of that request, there is malicious code written in such a way that when that web server invoked the JNDI message lookup feature, it would execute the malicious code. If there is a vulnerable system, it’s very easy for the attacker to establish themselves and to get that code executed.
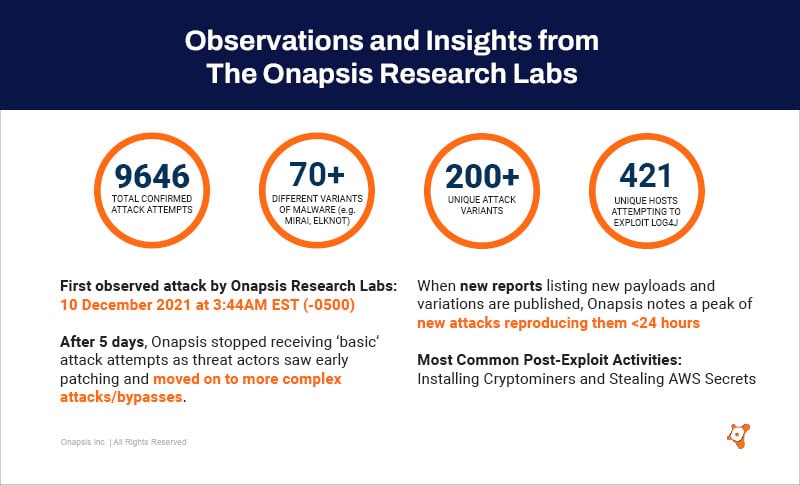
Here’s what we’ve seen (as of 27 January 2022):
- The first attack we saw was logged on 10 December 2021 @ 3:44 AM EST (“-0500”). Since then, there have been over 9,646 attacks.
- After five days, Onapsis stopped receiving ‘basic’ attack attempts as threat actors saw early patching and moved on to more complex attacks/bypasses
- More than 200 variants of the attack, with the majority of them being automated attacks and/or from bots
- Over 421 unique hosts attempting to exploit the Log4j vulnerability on our cloud
- 70 different variants of malware, such as the Mirai botnet and Elknot, have been observed exploiting this vulnerability
- Threat actors’ attempts to bypass firewalls include using base64 encoding; using uppercase/lowercase letter combinations; and leveraging obfuscation in order to avoid string matching
- Post-exploitation attempts have involved installing crypto miners and stealing AWS secrets
The good news? Onapsis researchers did not see any exploitation activity directly targeting SAP systems. Most of the attacks seen in our Threat Intelligence Cloud look for mass-exploitation.
Next Steps for Organizations
- Identify vulnerable software and systems and take immediate action to mitigate or patch the Log4j vulnerability. Leverage CISA and Apache Foundation resource pages as a starting point.
- CISA has urged all organizations to upgrade their systems or apply their appropriate vendor-recommended mitigations immediately to prevent any risks.
- The Apache Log4j team has issued patches and suggested mitigation steps to address the Log4j vulnerability.
- Adopt an assumed breach mentality and review logs for impacted applications for unusual activity.
- Implement a risk-based vulnerability management program with a focus on business-critical applications and timely, impactful threat intelligence to keep pace with the evolution of the Log4j threat moving forward.
More Log4j Resources
On-Demand Webinar: Watch our on-demand session with Richard Puckett, Chief Information Security Officer at SAP and Sadik Al-Abdulla, Chief Product Officer at Onapsis for the threat intelligence around the Log4j vulnerability and implications of the vulnerability on SAP applications.
Onapsis Security Advisory: For the most up-to-date information from Onapsis regarding the Log4j vulnerability, please refer to our security advisory.
SAP Patch Tuesday: Stay up-to-date with the latest SAP Security Notes in our monthly Patch Tuesday analysis.
For further assistance with the Log4j vulnerability and the impact to your SAP systems, contact our team.
