Ch4tter: Threat Actors Attacking SAP for Profit
New Intelligence to Protect SAP from Ransomware and Data Breaches

Unpatched SAP vulnerabilities are being exploited and used in ransomware campaigns, as highlighted by Onapsis Research as well as CISA.
The SAP threat landscape is seeing well-established, highly sophisticated threat actors and state-sponsored groups.
These groups are more aggressively targeting SAP applications for financial gain, espionage and sabotage.
There is high interest around SAP Vulnerabilities, demonstrated by the conversations in cybercriminal forums, as well as its active exploitation.
SAP and Onapsis have been proactively warning organizations of the increased risk of malicious activity and ransomware threats targeting SAP applications for years. It is imperative for organizations to act to protect themselves.
CH4TTER Report
Onapsis and Flashpoint have joined forces to level the playfield, revealing how threat actors are attacking SAP applications. This report covers:

On Demand Webinar
Threat Actors Attacking SAP for Profit
Over the past few years, the threat landscape around SAP applications has evolved significantly. What has driven this change? Threat actors are increasingly seeing the profit derived from SAP applications, associated data they hold, and taking advantage of vulnerabilities.
Pulling from Onapsis’ expertise in SAP cybersecurity and Flashpoint’s depth of threat intelligence, this webinar covers:
Speakers

JP Perez-Etchegoyen
CTO & Co-founder | Onapsis

Christian Rencken
Senior Strategic Advisor | Flashpoint
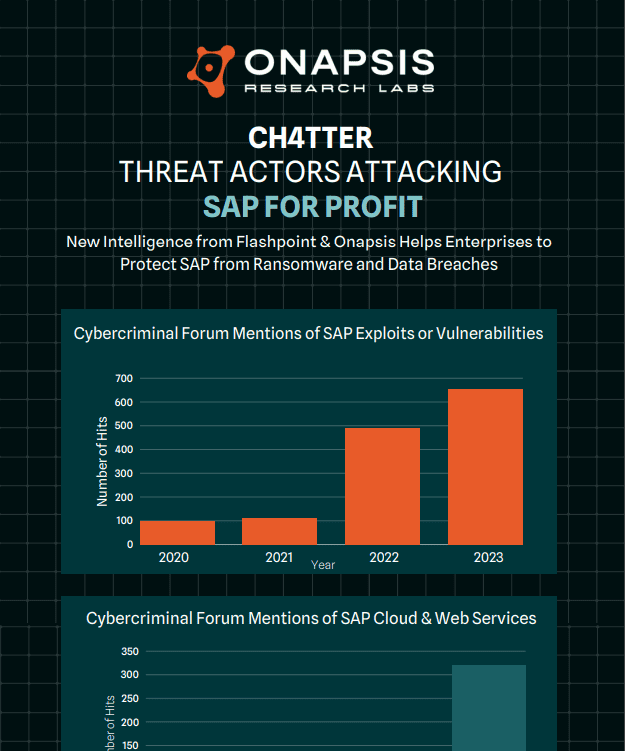
New Intelligence from Flashpoint & Onapsis Helps Enterprises to Protect SAP from Ransomware and Data Breaches
Gain crucial insights into the evolving landscape of cybersecurity threats with our latest infographic and discover how sophisticated threat actors not only encrypt an organization’s data for ransom but also engage in data exfiltration, subsequently selling it on illicit markets. Download now to stay informed and protect your organization against these growing threats.
Would you like to hear from Onapsis Research Labs one-on-one to learn more about their findings?
Request a 1-2-1 briefing with our team.

Frequently Asked Questions

Stay Ahead of CH4TTER Vulnerabilities with Onapsis Research Labs
Cybersecurity demands proactive measures, and protecting your SAP systems from the vulnerabilities being exploited is a critical endeavor. Don’t hesitate—reach out to us today to start strengthening your SAP environment’s security. Together, we can ensure your systems remain resilient and safeguarded against evolving threats.




