Onapsis Secure RISE AcceleratorTM
Accelerate your cloud transformation. Embed security into every phase of SAP Activate to de-risk your RISE migration and ensure a secure-by-design go-live.
Accelerate and De-Risk your RISE with SAP Transformation
The Onapsis Secure RISE Accelerator is designed to lower risk and reduce SAP RISE security and compliance obstacles in RISE projects. We deliver a proven framework that helps you make better-informed, faster security decisions.
Our accelerator narrows the scope for an optimized secure-by-design go-live. It de-risks the threat of costly project delays with automation and expert guidance that reduces manual effort, ensuring your move to the cloud aligns with the strategic vision of RISE with SAP as the future of business transformation. You can explore our full range of Onapsis SAP security solutions to see how we support every stage of your journey.










Why Companies Choose the Onapsis Secure RISE Accelerator
The Onapsis Secure RISE Accelerator combines expert guidance with powerful automation to transform your RISE security journey. Our dedicated security advisors work alongside your team, leveraging a proven framework to streamline critical decisions. Powered by Onapsis Research Labs, our automated platform continuously scans for vulnerabilities, monitors threats in real-time, and validates compliance, which is a key component of effective SAP RISE security.
- Accelerates project planning and execution: We guide you through each SAP Activate phase, de-risking costly project delays due to security or compliance obligations (e.g., under NIS2 or SOX).
- Narrows the scope: We help you better understand and focus on critical “must-haves” required for a compliant, secure-by-design go-live, enabling more efficient planning.
- Delivers powerful automation: Our technology automates manual effort, while our experts guide your teams with templates, best practices, and active participation every step of the way.
- Future-proofs your transformation: We provide assurance, operational efficiency, and scalability to confidently adopt future SAP innovations after go-live.
Barriers to Cyber Resilience in the Cloud
Moving to RISE with SAP transforms your infrastructure, but it also introduces new risks that can stall your migration if not addressed early. Organizations typically face four critical hurdles:
Onapsis SAP RISE security solutions overcome these barriers by providing the automation and visibility needed to secure the “customer half” of the shared responsibility model. We align your security, development, and audit teams with a unified platform that keeps your cloud transformation safe, compliant, and on schedule. This approach enables your organization to realize the business benefits of RISE.
SAP + Onapsis: Complete Security for RISE with SAP
SAP has implemented strong capabilities to protect the RISE with SAP cloud infrastructure, freeing you to concentrate only on the security and compliance areas you are responsible for. Onapsis simplifies and streamlines those responsibilities by providing a dedicated partner.

The RISE with SAP Shared Security Responsibility Model – full coverage with SAP & Onapsis
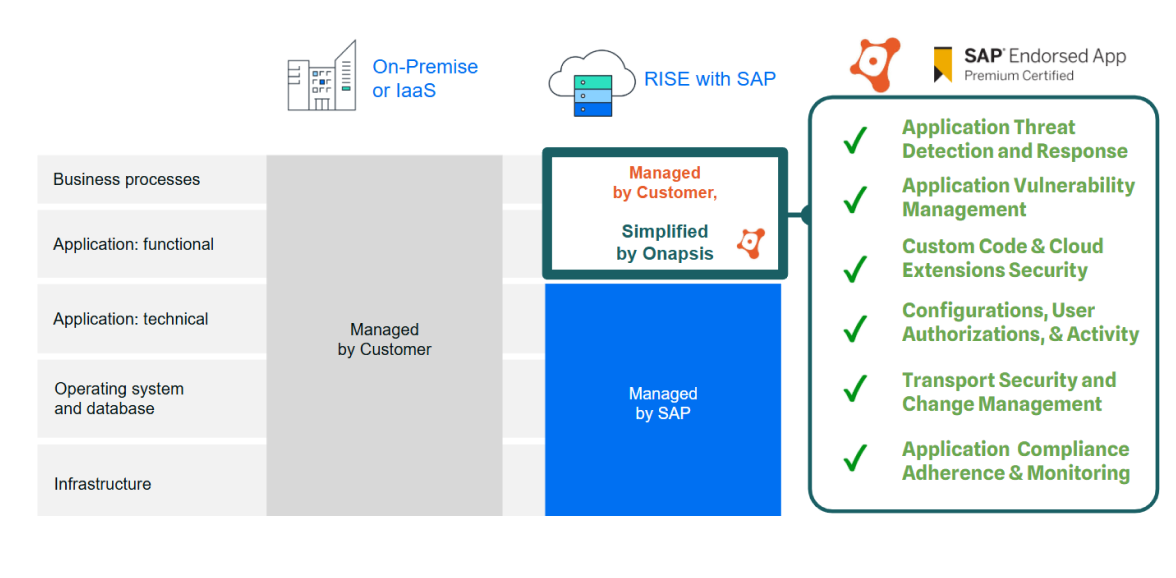
The RISE with SAP Shared Security Responsibility Model – full coverage with SAP & Onapsis

“Together, SAP and Onapsis provide enhanced security for RISE with SAP. SAP delivers a highly-secure and compliant RISE with SAP cloud infrastructure, enabling customers to focus solely on securing their SAP applications and data. Onapsis strategically complements SAP’s role, delivering the essential security and compliance capabilities customers need to achieve this.”
– Roland Costea | CISO, RISE with SAP
Webinar
Maximizing Security in RISE with SAP
In this informative presentation featuring Roland Costea, CISO at SAP Enterprise Cloud Services (ECS), and Mariano Nunez, CEO & Co-Founder of Onapsis, you will discover how the people, processes, and technologies at SAP ECS combined with the Onapsis capabilities, empower customers to better secure their Cloud ERP systems and promote long term business resilience.
Watch Now
What Our Customers Are Saying
Establish Good Code Security from the Beginning
Legacy vulnerabilities and insecure custom code are the primary causes of delays in RISE migrations. Onapsis eliminates these roadblocks before they impact your timeline.
- Eliminate Manual Reviews: Manual code reviews are slow and prone to error. Onapsis automates code security reviews wherever developers work, including Eclipse for SAP BTP, to identify errors and vulnerabilities instantly, freeing your team to focus on innovation.
- Implement Gate Checks: Prevent “bad transports” from breaking your new system. Bulk scan migrated legacy code, new development, and transports to prevent vulnerable objects from causing performance issues or downtime in your RISE production environment.
- Validate Code from Third Parties: RISE projects rely heavily on System Integrators (SIs). Onapsis allows you to verify the security and robustness of third-party code before you bring it into your production systems, ensuring you don’t inherit risk from your partners.


Minimize Your SAP Attack Surface & Streamline Compliance
Reduce the risk of your transformation by ensuring your new environment is hardened and compliant from day one.
- Automate Vulnerability Management: Proactively identify misconfigurations and authorization issues in your cloud environment. By catching these risks early in the Prepare and Explore phases, you prevent them from becoming go-live blockers.
- Streamline Audit & Compliance: Replace manual audit evidence collection with automated reporting. Our out-of-the-box Comply Packs help you validate compliance with SOX, GDPR, and NIST, reducing the burden on your team during the migration.
- Enforce a Clean Core: Ensure that your system configuration stays aligned with SAP best practices. We help you detect “configuration drift” immediately, ensuring your RISE environment remains secure and upgrade-ready long after the project concludes.
Continuously Monitor for Threats Across New & Legacy Landscapes
Once you are in the cloud, the threat landscape changes. Onapsis provides the specialized visibility required to protect hybrid and cloud-hosted SAP environments.
- Identify Suspicious User Behavior Faster: Insider threats and compromised credentials are top risks in the cloud. Onapsis monitors user behavior, critical access, and system activity to instantly detect anomalies and potential indicators of compromise.
- Detect and Mitigate Threat Actor Activity Faster: Defend against sophisticated attacks with the best exploit protection available. Powered by Onapsis Research Labs, we detect zero-day exploits in real-time and empower rapid response with detailed explanations and mitigation guidance.
- Easily Implement Compensating Controls: You cannot patch every vulnerability immediately. Onapsis helps you mitigate the risk of open vulnerabilities in your environment with granular monitoring and alerts, allowing you to meet regulatory requirements even when patching windows are limited.

Ready to build your business case?
Secure Your RISE Journey: From Phase 0 to Go-Live
Learn More About the Secure RISE Accelerator
The Onapsis Secure RISE Accelerator simplifies and streamlines your SAP RISE security journey. It delivers a comprehensive, proven SAP security framework that empowers you to make better-informed, faster decisions. The accelerator also narrows the scope for an optimized, secure-by-design go-live, while expert guidance and automation technology work together to de-risk costly project delays by reducing manual effort and costs.
Ready to Get Started?
Talk to our experts on how Onapsis and the Secure RISE Accelerator framework can de-risk your RISE project and help you make better project decisions and move faster.

Frequently Asked Questions
What are the key benefits of using Onapsis for RISE with SAP Security?
Onapsis eliminates the blind spots in the “Shared Responsibility Model.” While SAP manages the cloud infrastructure, Onapsis secures the application layer, including your data, customizations, and user identities. This reduces the risk of data breaches, ensures compliance with regulations like SOX and GDPR, and prevents project delays caused by late-stage security findings.
How does Onapsis support secure development practices for cloud-based systems?
Onapsis integrates directly with SAP BTP and modern development environments like Eclipse. It enables a “Shift Left” approach by automatically scanning code for vulnerabilities as it is written. This ensures that new cloud extensions and applications are secure-by-design, preventing “bad code” from ever entering your production environment.
Does migrating to RISE with SAP mean SAP handles all my security?
No. SAP provides world-class security for the physical data centers and the underlying infrastructure (IaaS). However, the customer remains responsible for the application layer. This includes securing custom code, managing user access, configuring application security settings, and monitoring for threats within the application. Onapsis provides the tools to manage these customer responsibilities.
How can we validate the work of our System Integrator (SI) during a RISE project?
Onapsis allows you to independently audit the deliverables from your SI. By scanning transports and configurations before they are deployed, you can verify that your partners are adhering to your security standards. This “Trust, But Verify” approach prevents you from inheriting security risks or misconfigurations that could cause issues after go-live.



