Onapsis Research Labs
Onapsis Research Labs is a team of the world’s leading cybersecurity experts dedicated to uncovering and mitigating threats in business-critical applications. As the most prolific contributor to SAP and Oracle security research, the Labs have discovered and helped patch over 1,000 zero-day vulnerabilities. Their threat intelligence powers the Onapsis Platform, ensuring that organizations can defend their ERP landscapes against the latest sophisticated attacks before they are exploited in the wild.

ICMAD: Critical Vulnerabilities in SAP Business Applications Require Immediate Attention
Onapsis Research Labs discovered a set of extremely critical vulnerabilities affecting SAP applications actively using the SAP Internet Communication Manager (ICM) component. This discovery requires immediate attention by most SAP customers.

The Elephant Beetle in the Room: Older, Unpatched SAP Vulnerabilities Are Still A Threat
Threat group ‘Elephant Beetle’ exploited two SAP vulnerabilities to steal millions of dollars from financial organizations. Here’s what that means for your SAP security.

Log4j Vulnerability & The Impact on SAP Applications
Onapsis Research Labs shares data and threat intelligence surrounding Log4j vulnerability, SAP security, and SAP applications.
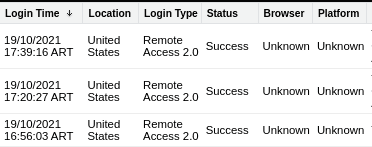
Salesforce Security Auditing: An Overview – Login History
In this blog series, Onapsis Research Labs will introduce you to the different types of audit capabilities that Salesforce has, analyze them, and see how they complement each other.

Cybersecurity Awareness Month: Onapsis’s Mission to Protect Business-Critical Applications
If you’re not already familiar with vulnerabilities in business-critical applications like SAP, Cybersecurity Awareness Month is a great time to start.
Black Hat 2021: Onapsis Research Labs Shares Learnings
Onapsis Research Labs shares their experiences and learnings from their SAP training session at Black Hat 2021.

Learn from the Business-Critical Application Security Experts at Black Hat USA 2021
Meet Onapsis at Black Hat 2021 for a training session on a complete approach for both Offensive and Defensive of SAP systems.

Salesforce Aura: Potential Vulnerabilities in the ‘Without Sharing’ Annotation
The Salesforce Winter ‘21 patch for Aura should remediate the security risk that allowed any authenticated user the ability to use web services exposed with the @auraenabled decorator. However, Onapsis Research Labs has some security concerns that we found within Aura that we’ll be covering in this blog post.

Q&A: Active Cyberattacks on Mission-Critical SAP Applications
During our recent webinar covering our threat report, we received a lot of great questions from attendees. In this post, we are going to address some of the questions that were asked in the live session.
