JP Perez-Etchegoyen
As CTO, JP leads the innovation team that keeps Onapsis on the cutting edge of the Business-Critical Application Security market, addressing some of the most complex problems that organizations are currently facing while managing and securing their ERP landscapes. JP helps manage the development of new products as well as support the ERP cybersecurity research efforts that have garnered critical acclaim for the Onapsis Research Labs. JP is regularly invited to speak and host trainings at global industry conferences, including Black Hat, HackInTheBox, AppSec, Troopers, Oracle OpenWorld and SAP TechEd, and is a founding member of the Cloud Security Alliance (CSA) Cloud ERP Working Group. Over his professional career, JP has led many Information Security consultancy projects for some of the world’s biggest companies around the globe in the fields of penetration and web application testing, vulnerability research, cybersecurity infosec auditing/standards, vulnerability research and more.

Sharing Best Practices at Cybersecurity for SAP Customers
Join us at SAPInsider’s Cybersecurity for SAP Customers event November 28 – 30 in Orlando, FL.
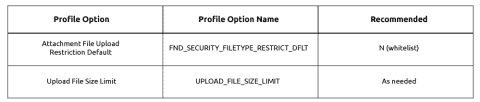
Restrict the File Types Uploaded to Your EBS Application
When it comes to Oracle EBS security, there are many steps to take to proactively protect your organization. Restricting file type and size is one of them. Learn more about why and how to prevent unintended consequences.
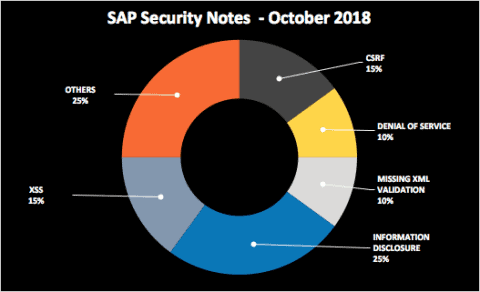
SAP Security Notes October ‘18: First Critical BusinessObjects Note in Five Years
Our monthly report on how to improve your SAP security and take care of your most critical information by exploring the latest SAP Security Notes for October 2018.
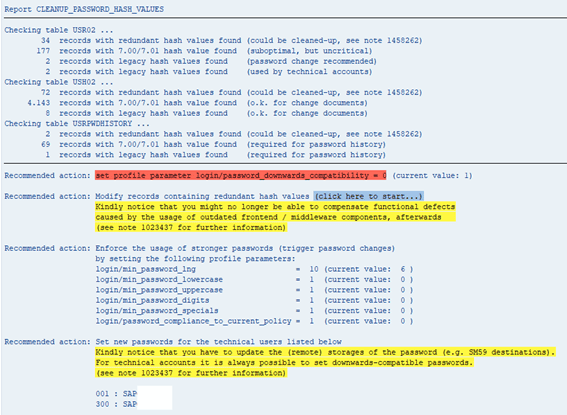
How Do You Check Old Hashes in Your ABAP System?
Learn how to further protect your SAP systems by checking if your ABAP systems contains stored insecure hashes.
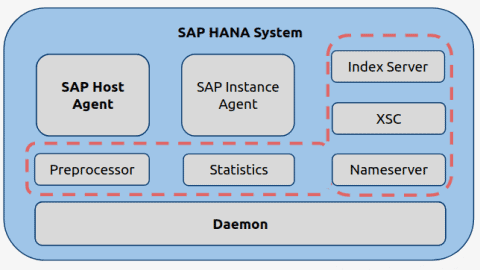
Analysis of the SAP HANA Internal Communication Interface
SAP HANA is a very fast growing product in many SAP environments, that has moved away from just an in-memory database to a complete application plus database system. In today’s blogpost we’ll talk about the SAP HANA internal communication interface, discuss its use in different scenarios, the configuration parameters involved and the different options that…
Oracle July CPU Analysis: Onapsis helps patch critical vulnerability in E-business Suite
As a security vendor and Research Labs with the goal of protecting our customer’s business-critical applications we also have the continuous balance of proactively informing the community about emerging threats affecting their critical applications. A big part of this is our continuous work with vendors to help them secure vulnerabilities in their software. Today, for…
Protecting Oracle E-Business Suite: Reducing the Attack Surface
This is the fourth consecutive blog post in our series on how to make Oracle E-Business Suite more secure. In this post, we will focus on reducing the attack surface – something that is a critical component for any successful information security strategy. The more you can reduce the components that are exposed to attackers (and…

Protecting Oracle E-Business Suite: Password Policy
For a third week, we’re providing you with best practices for securing your Oracle E-Business Suite implementation. Today, we are going to talk about a common topic: password security. When it comes to password policy, the first thing that probably comes to mind is having a secure password. That is why in addition to all network security…

