JP Perez-Etchegoyen
As CTO, JP leads the innovation team that keeps Onapsis on the cutting edge of the Business-Critical Application Security market, addressing some of the most complex problems that organizations are currently facing while managing and securing their ERP landscapes. JP helps manage the development of new products as well as support the ERP cybersecurity research efforts that have garnered critical acclaim for the Onapsis Research Labs. JP is regularly invited to speak and host trainings at global industry conferences, including Black Hat, HackInTheBox, AppSec, Troopers, Oracle OpenWorld and SAP TechEd, and is a founding member of the Cloud Security Alliance (CSA) Cloud ERP Working Group. Over his professional career, JP has led many Information Security consultancy projects for some of the world’s biggest companies around the globe in the fields of penetration and web application testing, vulnerability research, cybersecurity infosec auditing/standards, vulnerability research and more.

White Paper: The Critical Controls Implementation for SAP
Onapsis, in collaboration with The Cloud Security Alliance (CSA), a not-for-profit, organization dedicated to defining and raising awareness of best practices to help ensure a secure cloud computing environment, has completed The Critical Controls Implementation for SAP white paper.

DevOps + Security = DevSecOps
More and more companies are promoting close cooperation between development and operations to accelerate the delivery of high-quality software. But the fast DevOps environment requires an integrated security approach, bringing us DevSecOps.
Before You Migrate Critical Applications to the Cloud
In this post, we’ll explore some considerations for cloud migrations that help ensure security and success.

Scary Application Security Horror Stories
With Halloween upon us, here are three cybersecurity horror stories that just may scare you straight when thinking that you are protecting the applications your organization relies on.
Why the RECON Vulnerability Is a Before and After for SAP Cybersecurity Introduction
Anywhere from 2,500 up to potentially 10,000 internet-facing systems were exposed to RECON at the date of the release of the patch. Considering those numbers and that approximately 30% to 40% of the systems could still be vulnerable (based on estimations of diverse samples), that provides an enormous attack surface and risk. Learn more in our blog post here.

Podcast: Emerging Security Threats to Your Digital Supply Chain
Jason Frugé, Vice President of Business Application Cybersecurity at Onapsis, was recently featured on an episode of the Enterprise Security Weekly Podcast, Emerging Security Threats to Your Digital Supply Chain.

Ten Recommendations for Better ABAP
ABAP stands for Advanced Business Application Programming and is SAP’s proprietary programming language. Here are ten recommendations for better ABAP.
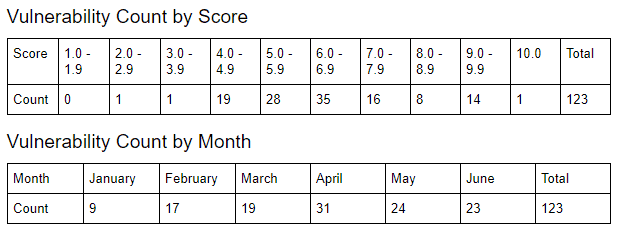
Top 10 SAP Vulnerabilities in 2020 Ranked by CVSS Score
In this blog, we cover the 10 top-scoring vulnerabilities from the first half of 2020. Of those, half were detected by Onapsis Research Labs, including the most severe.

What is CVSS and How Does Onapsis Use It?
It is nearly impossible to create error-free software or hardware, and for complex systems, this is even more true. Not every bug is a vulnerability, but many bugs are. A CVSS score ranks these vulnerabilities from highest to lowest priority.
