SAP Vulnerability Management
See what your traditional scanners miss. Automated vulnerability management, assessment, and risk prioritization specifically designed for business-critical SAP applications.
Why Traditional Scanners Fail SAP Vulnerability Management
General-purpose network scanners are engineered to scan operating systems and network infrastructure. However, they encounter a hard technical limit when applied to SAP Vulnerability Management.
Because these tools do not natively support SAP proprietary protocols (such as RFC and DIAG) or interpret ABAP programming logic, they stop at the OS layer. This leaves the SAP Application Layer (where your business logic and data reside) unmonitored and exposed. Onapsis security solutions eliminate this blind spot by natively analyzing the application layer to identify specific, high-risk vulnerabilities that generic tools miss:
Onapsis Assess: Proactive SAP Vulnerability Management
Onapsis Assess empowers you to identify risk, prioritize remediation, and reduce your overall attack surface. As the only cybersecurity and compliance solution in the SAP Endorsed Apps program, it provides the proven visibility you need for the business-critical application layer across cloud, on-premises, and hybrid environments.
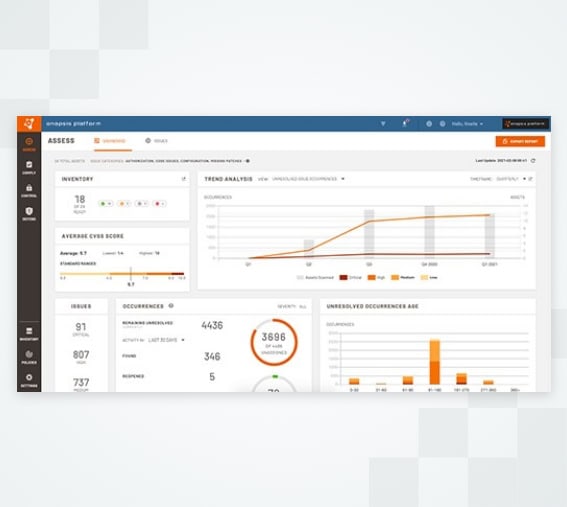
- Identify & Prioritize: Powered by insights from the Onapsis Research Labs, Assess correlates vulnerabilities with real-time threat intelligence, helping you focus on the specific risks that matter most to your business.
- Eliminate False Positives: Our patented analysis engine traces data flow to ensure we only flag real issues, maintaining a <5% false positive rate to save your Basis team hundreds of hours.
- Automate Remediation: We don’t just find problems; we help you fix them. Assess provides automated “one-click” fixes for code errors and validates that manual patch steps were performed correctly.

Connect with an Onapsis SAP Vulnerability Management Expert
We provide the visibility, intelligence, and speed you need to secure your cloud, hybrid, and on-premise business-critical applications. Talk to us today to learn how we can help protect your business.
Frequently Asked Questions
How does Onapsis help with managing vulnerabilities in business applications?
Onapsis automates the vulnerability management lifecycle for business-critical applications by moving beyond simple scanning. We identify vulnerabilities across the application layer (including custom code and configurations), prioritize them based on real business risk rather than just technical severity, and streamline remediation by validating that patches and manual correction steps are applied correctly.
What are the best tools for managing vulnerabilities in SAP and Oracle systems?
The best tools are those specifically engineered for the application layer of ERP systems. While generic scanners are excellent for infrastructure, they cannot see inside SAP or Oracle protocols. Onapsis Assess is the industry standard for these environments because it natively supports proprietary protocols (RFC, DIAG) and integrates with vendor-specific workflows to provide visibility that generalist tools miss.
Can Onapsis help with securing on-site ERP systems?
Yes. Onapsis provides comprehensive security for on-premises, cloud, and hybrid ERP landscapes. Whether your SAP or Oracle systems are hosted in your own data center, in a private cloud, or managed via a service like RISE with SAP, Onapsis delivers consistent vulnerability assessment and protection across the entire estate.
How does vulnerability management support regulatory compliance?
Vulnerability management is a core requirement for major frameworks like GDPR, SOX, PCI-DSS, and NIST. Onapsis simplifies compliance by mapping technical vulnerabilities directly to these regulatory controls. This allows you to prove to auditors that your financial and customer data is protected and that you have a repeatable process for identifying and mitigating risk.
What is the ROI of automating SAP vulnerability management?
Automation significantly reduces the “Mean Time to Remediation” (MTTR) and operational costs. By replacing manual audits (which can take weeks) with automated scanning, and by eliminating up to 95% of false positives, Onapsis allows security teams to do more with fewer resources. This efficiency prevents costly downtime and frees up Basis teams to focus on strategic initiatives rather than chasing false alarms.


