Resources

Onapsis Protecting Your Mission-Critical App: How to (Properly) Understand Your Risks
Evaluate and quantify the value of solutions that are designed to help manage your risks and reduce your operational costs by establishing a proper understanding of risk. Watch this webinar to learn how to protect your mission-critical applications and more.

Volume XVII: Remote Function Call: The Whole Picture
The aim of this publication is to fully introduce and explain the concept of Remote Function Call (RFC) and the impact on the Gateway and Message Server. We will focus not only on the importance of it, but also how to implement secure communication in your landscape. Onapsis strives to provide the most complete security…
Cybersecurity Experts Discuss How Businesses are Protecting Themselves to Remain Cyber Resilient
Hear from Khaja Ahmed, Head of Global Product and Application Security at SAP, and Onapsis General Manager of Product and Technology, Anshuman Kanwar, discuss the challenges and strategies companies have for protecting their mission-critical applications to maintain business success.
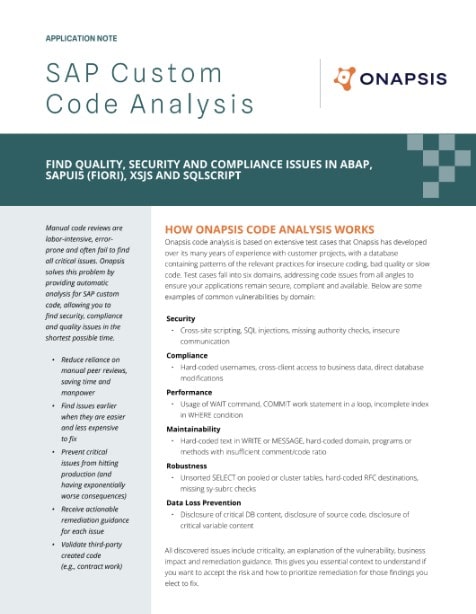
SAP Custom Code Analysis
Find quality, security and compliance issues in ABAP, SAPUI5 (FIORI), XSJS and SQLSCRIPT. Learn how Onapsis can help.

SAP Transport Inspection
Avoid import errors, business outages, downgrades, security vulnerabilities and compliance violations by inspecting all transports before import. Learn how Onapsis can help.

Critical Controls for SAP Implementation
A two part implementation document to help organizations securely migrate to and operate ERP applications in the cloud

Working with Onapsis to Strategically Move to the Cloud
Hear from Preston Futrell, leader of the Global Business Services organization at IBM, as he discusses how they help customers develop their SAP implementations as they migrate to the cloud and how working with Onapsis enables them to assure that security is included.

Defense Federal Acquisition Regulation Supplement (DFARS)
An unauthenticated attack exploiting a misconfiguration or vulnerability in your mission-critical applications, which many organizations use to manage supply chains with their partners, could allow malicious actors to manipulate underlying data without touching user applications or leaving an audit trail, violating DFARS.

EU General Data Protection Act (GDPR)
The EU GDPR regulation requires companies to protect any personal data that is stored in their systems, from both theft and manipulation. Hackers could target a misconfiguration or vulnerability in the company’s mission-critical applications, and gain access to this data without using business applications or leaving an audit trail, violating GDPR.
