Resources

Secure Every SAP Build in Your CI/CD Pipelines
Minimize Hidden Risks in modern SAP Custom Code development

Leading Automotive Manufacturer, Škoda, Secure-by-Design Approach Improved Performance of ERP Systems While Saving Time
Onapsis Control for Code has helped them maintain more compliant and secure system landscapes, contributing to overall stability and risk reduction.

Defending What Matters Most: Smarter, Faster Incident Response with Onapsis and Microsoft Sentinel for SAP
This webinar provides security professionals with an in-depth, educational look at both the latest tactics, techniques, and procedures used by threat actors to directly attack SAP, as well as the next-gen methodologies and tooling required to defend against them.
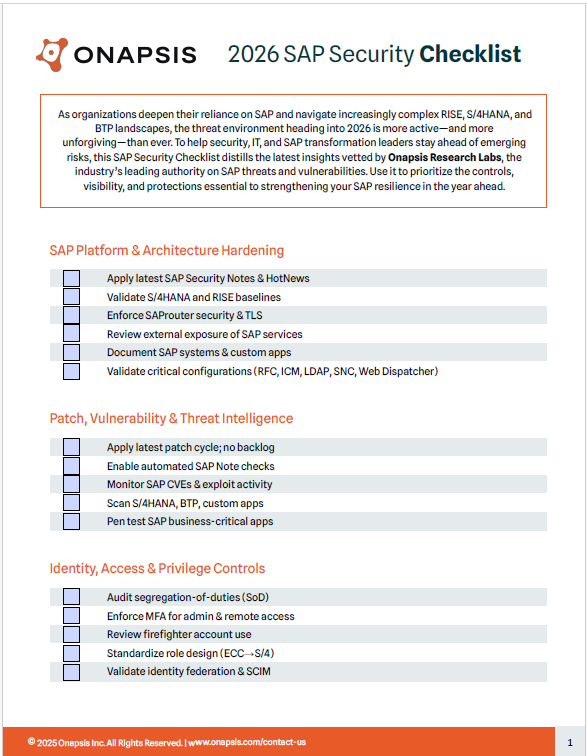
2026 SAP Security Checklist
Onapsis 2026 SAP Security Checklist: Secure your S/4HANA, RISE, and BTP landscapes against emerging threats. Prioritize critical controls for platform hardening, patching, access management, monitoring, and cloud security.

The State of SAP Security: 2025 Vulnerabilities, Exploits & Lessons Learned
JP Perez-Etchegoyen and Paul Laudanski from Onapsis Research Labs (ORL) recap the top SAP security vulnerability trends from 2025, provide an anatomy of real attacks to SAP Applications, and share practical guidance to help you strengthen your SAP defenses for 2026.

Empowering Security Operations with Unified SAP Threat Detection and Response
Onapsis Defend & Microsoft Sentinel solution for SAP

Securing Your Future: Preparing for a Successful SAP RISE Transformation
Watch Marc Rosson, Enterprise Architect at Snohomish County PUD and Paul Kurchina, SAP community leader for enterprise architects, as they discuss the essential security preparations you must complete before your SAP RISE transformation, with an emphasis on the shared responsibility model.

ERP Today Magazine: Q3 2025 Edition
This edition of ERP Today highlights how enterprise leaders are protecting business applications against SAP cyber threats with our CEO & Co-Founder Mariano Nunez. With the increase of SAP related cyber attacks we’ve seen just this year alone, organizations can’t wait until after they’ve been compromised to invest in SAP security. If there’s ever been a time to be proactive about SAP cybersecurity it’s now and we’re proud to be at the forefront of this movement. Learn more inside this edition of ERP Today.

The Technology Leader’s 2025 Agenda for SAP
Discover the top challenges, priorities, and investments of technology leaders at SAP customer organizations in 2025. This report details how SAP S/4HANA migration, AI, and data strategy are shaping the modern enterprise.
