Webinar: Cybersecurity in Transition With Reza Mehman
“The task of art today is to bring chaos into order.”
Theodor Adorno, 1903-1969
Unlike Theodor Adorno, at Onapsis, we want to actually achieve the contrary: We want to bring order to chaos. With new technologies, like the Internet of Things, or massive trends like digital transformation, we are getting a new dimension of complexity, which might feel a little bit like chaos, at least from the IT landscape perspective.
The cybersecurity industry is powerful and full of experts. Still, successful cyberattacks happen all the time, all over the globe. Why is it like that? Why do hackers find new ways to attack their targets?
The problem is not that the cybersecurity industry is not evolving fast enough. To be honest, I think it is even the contrary—we are evolving very fast. The problem is, as IT security expert Bruce Schneier says, the target of cybersecurity is constantly moving. More and more new technologies with greater complexities are coming onto the market. And they all have their own attack surfaces. And therefore, as complexity grows, we are losing ground.
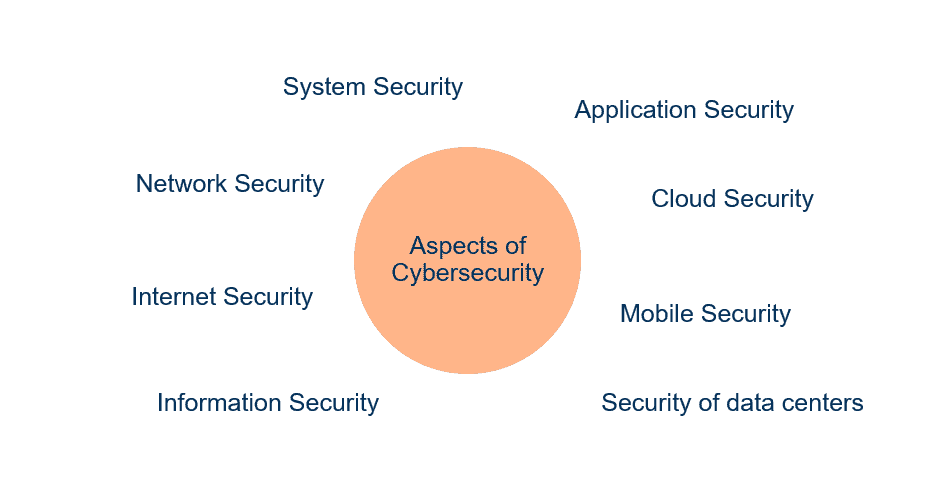
Aspects of Cybersecurity
There are many different targets for hackers in your IT landscape. To mention some of them:
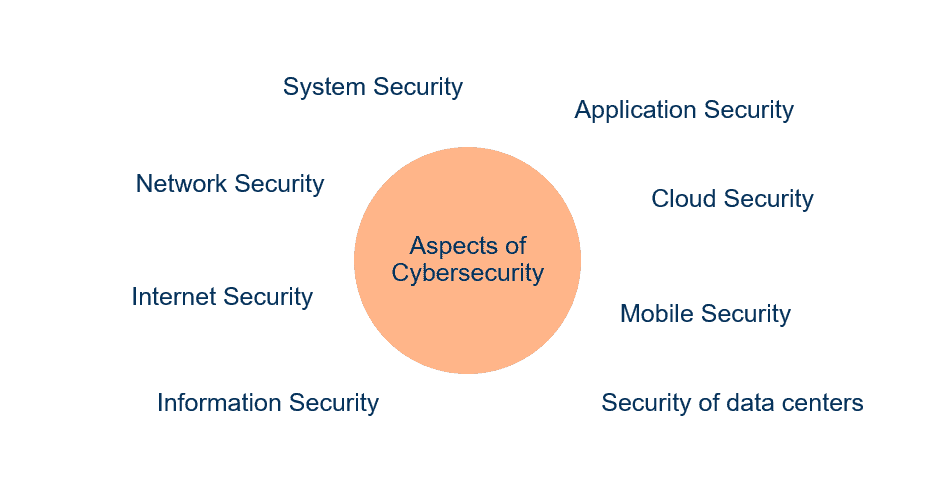
- Network Security
- Securing data and resources in your computer network
- System Security
- Applying safe configurations to your systems
- Application Security
- Having secure development guidelines for your business-critical applications
- Cloud Security
- Having the right measures implemented to prevent data loss, service failure or unauthorized access.
- Mobile Security
- Protection of data, for example on Smartphones or IoT devices
- Datacenter Security
- Physical protection of data centers against unauthorized access
- Information Security
- Usage of encryption techniques
- Internet Security
- Having secure browsers and tools in place for your corporate users
If you consider that all these topics require their own experts or expertise, you get an idea of how complex cybersecurity can be.
Although it is crucial to cover the technological side of cybersecurity, we need to keep in mind, that the majority of all successful attacks actually don’t focus on technology. The largest number of attacks focus on exploiting the human elements the vulnerability. And some of you have probably experienced attacks like phishing emails, malware etc. That even adds another attack vector to your overall risk management strategy.
Security Objectives
At the end of the day, the three main objectives of security are:
1. Ensure Business Continuity
The nightmare of every IT manager: The system fails or is unavailable and the entire business processes come to a standstill. Every second your systems are down, you will lose valuable revenue.
2. Ensure Compliance
Companies must comply with local legal requirements. And as you can see from GDPR and other privacy regulations, more and more countries are implementing laws to protect information systems.
3. Adhere to Contracts With Stakeholders
Finally, you have contracts with customers and partners for your products and services. Typically these contracts involve confidential customer or partner information. Imagine now suffering from a data leak or data loss. You may have to pay large penalties or even worse, lose trust from customers and partners.
To play by the rules, many different attack vectors need to be secured by organizations. For example:
- Protection from external or even internal hackers to prevent industrial espionage and fraud.
- Overlooking new attack surfaces because of “BYOD” (bring your own device) policies. Personal smartphones, tablets and IoT devices within your company network are potential gateways into your systems.
- Anticipating new development paradigms, that, for example, allow rapid development of prototypes, but where security is unfortunately not the highest priority.
- Simultaneous operations of on-premise and cloud applications, where you need to connect your firewall-protected on-premise applications to cloud services via the internet.
Recommendations on Mastering Complexity
So what would I recommend to master this complexity?
1) Create security awareness throughout your organization. Train your employees well. Most cyberattacks focus on the user, not the technology. At the end of the day, we are all human. One second of inattention and a link from a phishing email is clicked, especially during a time when many organizations are working from home. Train your employees to have a healthy suspicion for digital information coming in.
2) Secure your systems and applications properly. Implement a risk management strategy, that delivers actionable intelligence, continuous monitoring and automated governance of your business critical applications. The Onapsis Platform is the right product to support you on this for protecting your SAP and Oracle ERP applications.
3) And last but not least, deal with new technologies and new ways of access that you are using. Can you control access to your network and critical applications to mitigate risk? What are these new IoT devices about? Which software frameworks are implemented? Are those regularly patched? What does it mean to bring your own devices into your company? Do they have any known vulnerabilities that we need to take care of?
One important answer on where cybersecurity is heading is Machine Learning. In my next blog, I will give you some insights about this new trend that helps companies to run their business safer. Watch my latest webinar on-demand here to learn more about the current and future state of cybersecurity.

