Understanding ERP Cyber Risk—Where Are You Vulnerable & How to Assess?
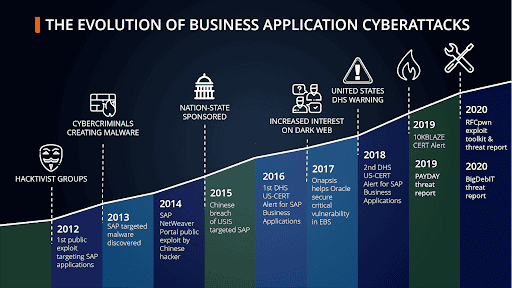
ERP systems, such as SAP and Oracle E-Business Suite (EBS), are the operational engine of an organization, running the mission-critical applications and holding the data needed for businesses to function. Yet despite the importance of these systems, they almost always fall in a cybersecurity blind spot, left unprotected against internal misuse and external attacks. Consider:
- 64% of ERP systems have been breached in the last two years
- 53.4% of SAP users indicated that it is ‘very common’ for SAP security flaws to be uncovered during the audit process
Challenges to ERP Cybersecurity—What’s Behind This Risk?
No Visibility for InfoSec Teams
These mission-critical applications are usually out of scope for information security teams, generally managed by a separate team within the IT organization, whose priority is availability and uptime. While some security elements, such as authorizations and IDM issues, may be addressed by this team, they typically have limited tools to identify or understand the importance of secure configurations at the application layer. This dissonance in priorities often results in systems going unpatched or “dangerously” configured for years in the interest of operational performance.
Patch Problems
Speaking of patches, ERP is just like any other software and requires patches regularly for updates, fixes, and improvements. Unfortunately, just like any other software, ERP patches are often neglected, delayed, or ignored altogether due to fear that the application will stop working as a result, a lack of time or resources, inability to discern which patches are critical and need to be prioritized, the list goes on. This becomes a major problem when the patch addresses security vulnerabilities. Missing these patches puts your most important applications and data at risk—60% of last year’s breaches involved unpatched vulnerabilities.
Security Often Isn’t Prioritized During Implementation
Perhaps not surprising given the InfoSec blindspot discussed above, security is often an afterthought in ERP deployments, taking a backseat to operational priorities and project timelines or budgets. In fact, a recent survey found a majority (69%) of SAP users believe their organizations didn’t place enough focus on security during previous SAP implementations. Failing to build security baselines and ongoing monitoring into deployments from the start leaves organizations with no easy way to measure their risk posture and understand where they might be vulnerable.
Misplaced Trust in Traditional Security Approaches
Many large enterprises rely on manually instrumenting and configuring built-in tools to secure their mission-critical applications (e.g., SAP’s Solution Manager, Oracle Security Console). However, these tools are often not purpose-built for security and, most importantly, are generally not managed by or accessible to security teams (adding to the blind spot discussed above).
Similarly, traditional firewalls, vulnerability scanners, IPS and IDS products focus on identifying attack signatures at a different layer and depth than required in mission-critical applications. These solutions give you insight into how you have secured your infrastructure and network, but not your most critical business applications.
Transformation and Modernization Are Increasing Risk
New industry dynamics (e.g., the looming deadline for SAP customers to upgrade to S4/HANA) and internal initiatives (e.g., migrating to the cloud, making more applications accessible via the internet) are also threatening mission-critical applications and expanding the risk surface.
For example, a majority of businesses (69%) are moving their ERP to the cloud, but taking these critical systems off-premises has many concerned about security—60% view security as a barrier to migration—especially because cloud providers are not responsible for application security.
Increase in Cyberattacks Against Mission-Critical Applications
Finally, malicious activity against these applications is at a record-high across all threat actor types. Cybercriminals and hacktivist groups have taken a keen interest in these systems in the past few years, and as a result, our research has found a 160% increase in exploits targeting these applications and systems.
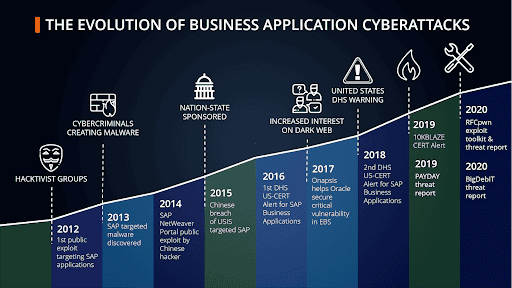
Quantifying and Addressing ERP Cyber Risk
It’s clear that many factors are working together to put the applications at the heart of your business at risk, but how much and in what ways? How can you identify and understand the business impact of the issues within your environment?
Onapsis recently launched a new assessment offering to do just that. The Cyber Risk Assessment provides a detailed report of existing vulnerabilities and misconfigurations highlighting potential exploits and compliance violations.
The results Onapsis delivers will help:
• Identify existing misconfigurations and vulnerabilities
• Prioritize and expedite remediation plans
• Reduce the overall attack surface
• Protect your mission-critical applications
Run remotely and simple to execute, the Cyber Risk Assessment can be completed in less than two hours and does not require installation of any software or agents on production systems. Request your Cyber Risk Assessment here.
p.s. We realize security is only one part of protecting your mission-critical applications. We also offer assessments on Audit Efficiency to help you eliminate resource-consuming manual audit processes, and Operational Resiliency to help prevent application downtime and costly business disruptions.


