SAP Transport Security Webinar: Transformation with Less Risk and More Efficiency
My name is Andreas Gloege, and I am the Vice President of North American Sales Engineering at Onapsis. After more than 25 years of experience working with and for SAP, I have spoken at numerous conferences around the world about the importance of securing your SAP systems, throughout both regular change management processes as well as major transformation projects, such as a cloud migration or the upcoming S/4HANA migration deadline.
If you were unable to join my recent webinar, SAP Transport Security: Transformation with Less Risk and More Efficiency, you may be wondering how you can keep your SAP environment secure when moving changes into production. A perfect real-life example would be if some members within your organization want to be able to have business processes accessible on their mobile devices. Ultimately, we’ll be running this specific business process through the SAP application, but accessing through the phone.
What’s Involved in Implementing This Type of Change in SAP?
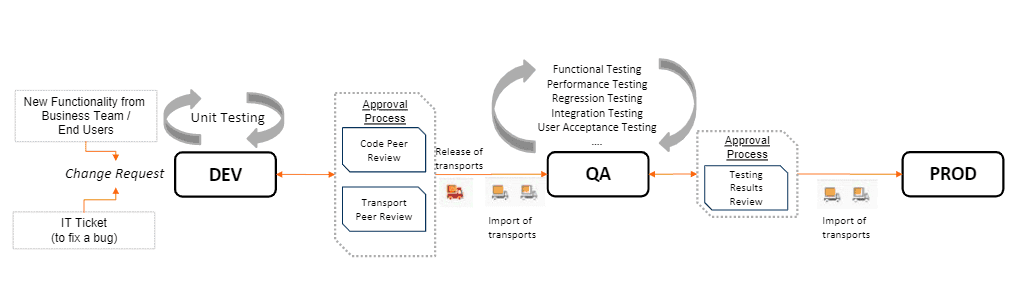
There are a lot of steps in place behind the scenes to make this type of change happen. Here is a visual representation of how changes move through the SAP landscape to development:
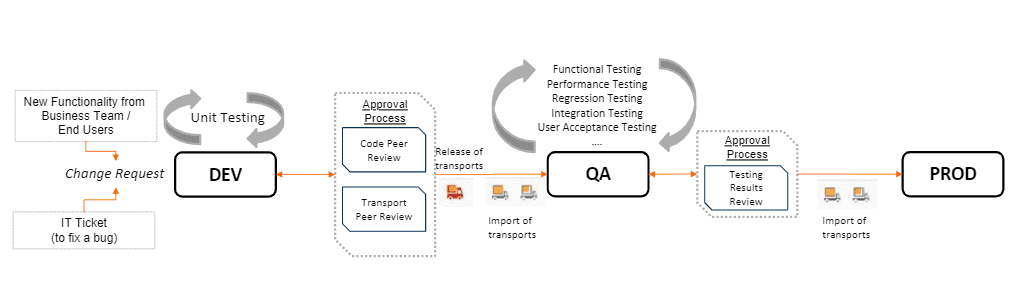
After the change request comes in, we go through the development phase. Once testing has been completed, the transport is released and then imported into the target system, in this case, the QA system where we can do our function testing, regression testing, performance testing, all the different types of, user acceptance testing, etc. Once the testing is successfully completed and reviewed, we will input those changes into production (again, via transport import). This is obviously on a very high level, and a very simplified view, on how changes move from Dev into production, but nevertheless you can see the critical role that transports play in the process.
Transports: Essential for Change, but Can Hide Threats
While production systems and the critical personal, customer, financial and product data they hold are generally highly secured, transports offer a dangerous gateway to these critical systems. Leveraging the generally weaker security around development systems, bad actors could create something they wouldn’t normally be able to create in production and then hide it in a transport to move it over. Considering most organizations see around 170 transports per month on average, this leaves open a lot of opportunities for vulnerabilities, including data espionage or manipulation.
For example, an employee’s current salary is set to $50,000 within the production system. I’m the developer; I write in development where the data is not relevant, but I can adjust the salary set in our development system. I could easily increase that to $60,000 for a nice 20% increase, but since it’s just in development, it doesn’t really matter…or does it? I can use a transport to get this change into the production system and suddenly that employee has a higher salary! And not only is this bad, but it gets worse—in the import log, it’s very easy to remove with it all traces of it ever happening, with no information in the object list.
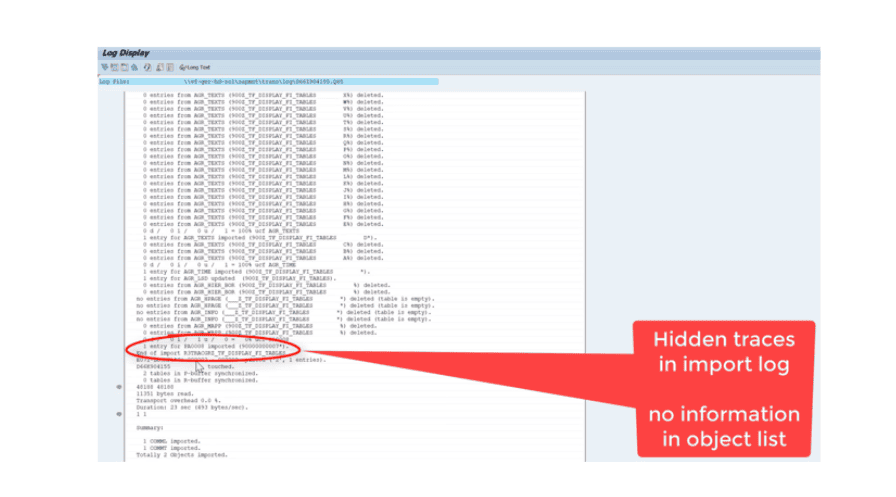
Whether it’s manipulation, like the example above, or espionage or sabotage, transports pose considerable risks for SAP security. And most companies are not yet aware that the SAP transport system involves extremely high-security risks.
To learn more about the hidden threats posed by transports, how they introduce risk to your SAP landscape and how to incorporate security checks into your change management process, watch the on-demand webinar now.


