SAP Security Notes: October 2025 Patch Day

Three new HotNews Notes published by SAP in collaboration with Onapsis
Highlights of October SAP Security Notes analysis include:
- October Summary – Twenty-three new and updated SAP security patches released, including six HotNews Notes and two High Priority Notes
- Insecure Deserialization Vulnerabilities – SAP has published a HotNews Note with additional security hardening recommendations in collaboration with the Onapsis Research Labs
- Onapsis Research Labs Contribution – Our team supported SAP in patching three new vulnerabilities, covered by two HotNews Notes and one Medium Priority Note
SAP has published twenty-three new and updated SAP Security Notes in its October Patch Day, including six HotNews Notes and two High Priority Notes. Four of the fourteen new Security Notes were published in contribution with the Onapsis Research Labs.
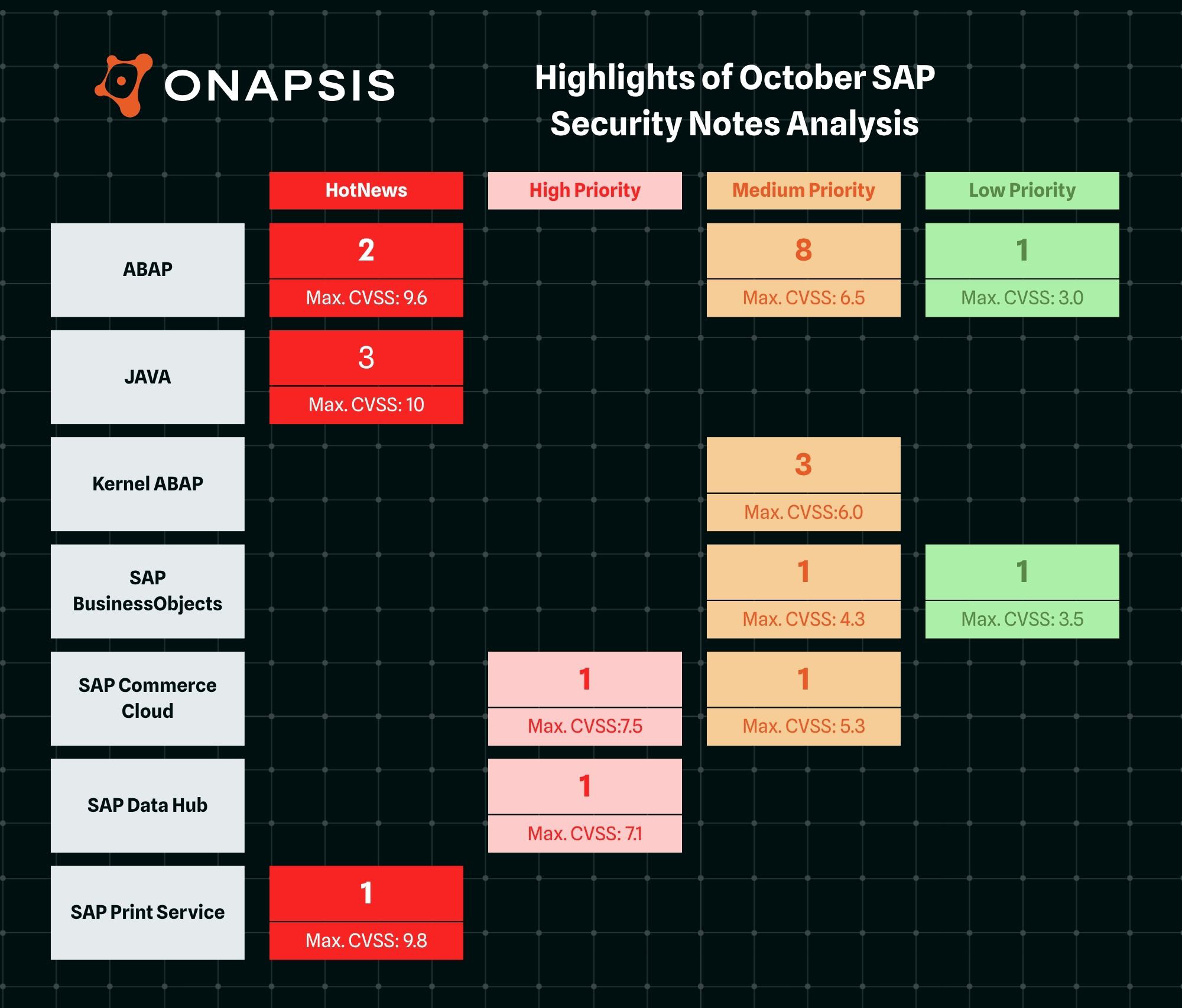
The HotNews Notes in Detail
Three of the six HotNews Notes are released for the first time, in collaboration with the Onapsis Research Labs (ORL).
SAP Security Note #3660659, tagged with a CVSS score of 10.0, provides an additional layer of protection for a series of Insecure Deserialization vulnerabilities that were detected and individually patched in SAP NetWeaver AS Java during the last months. The latest one was patched on SAP’s September Patch Day with SAP Security Note #3634501. The additional layer of protection is based on implementing a JVM-wide filter (jdk.serialFilter) that prevents dedicated classes from being deserialized. The list of recommended classes and packages to block was defined in collaboration with the ORL and is divided into a mandatory section and an optional section.
Onapsis has already released a module for their customers that checks the correct implementation of the note. It first makes sure the SAP NetWeaver and the SAP Java Virtual Machine (JVM) version are new enough to use this security feature. Next, it checks that the security patches provided in SAP Security Note #3660659 are implemented. If not, the module will check for the implementation of the temporal workaround proposed by SAP reviewing if the filter is set up and working correctly, specifically looking for any typos that would break it. Finally, the module checks the filter’s list of blocked items against SAP’s recommended lists of mandatory and optional classes.
The ORL team supported SAP in patching a critical Directory Traversal vulnerability in SAP Print Service. SAP Security Note #3630595, tagged with a CVSS score of 9.8, describes that the vulnerability allows unauthenticated attackers to perform directory climbing and over-write system files. A successful exploit can cause a high impact on confidentiality integrity and availability of the application.
SAP Security Note #3647332, tagged with a CVSS score of 9.0, patches an Unrestricted FIle Upload vulnerability in SAP Supplier Relationship Management(SRM). The ORL team detected that, due to missing verification of file type or content, the application allows an authenticated attacker to upload arbitrary files. These files could include executables hosting malware. When downloaded and executed by the user this could lead to high impact on confidentiality, integrity and availability of the application.
SAP Security Note #3634501, tagged with a CVSS score of 10.0, was initially released on SAP’s September Patch Day in collaboration with Onapsis. SAP has now added a reference to the new hardening recommendation in SAP Note #3660659.
SAP Security Note #3643865, tagged with a CVSS score of 9.9 and SAP Security Note #3302162, tagged with a CVSS score of 9.6, were only extended by minor textual changes that do not require any customer action.
The High Priority Notes in Detail
SAP Security Note #3664466, tagged with a CVSS score of 7.5, patches a Denial of Service vulnerability in SAP Commerce Cloud (Search and Navigation). The application uses a vulnerable version of the jetty web server caused by a flaw in the HTTP/2 protocol.The vulnerability allows a malicious client to open further streams and send crafted requests that could cause the server to reset the streams and consume excessive resources over a short period of time.
SAP Security Note #3658838, tagged with a CVSS score of 7.1, patches a vulnerability in SAP Datahub Suite that is caused by the Apache CXF 3.5.1 libraries with JMS/JNDI configuration. Keeping unpatched, an unauthenticated user can configure JMS and supply malicious RMI/LDAP endpoints (CVE-2025-48913) which could leverage a Code execution vulnerability. The patch includes version 3.6.8 of Apache CXF that is not vulnerable to CVE-2025-48913.
Onapsis Contribution
In addition to three HotNews Notes, the Onapsis Research Labs (ORL) supported SAP in patching a Medium Priority vulnerability. The ORL team identified a remote-enabled function module in SAP Financial Service Claims Management that allows authenticated attackers with non-administrative privileges the enumeration of valid user accounts. SAP Security Note #3656781, tagged with a CVSS score of 4.3, patches the vulnerability through enforcing proper authorizations and changes in the returned error response of the function module.
Summary & Conclusions
Due to the increasing number of active exploits of SAP vulnerabilities, it is important to have multiple lines of defense. SAP NetWeaver AS Java customers should therefore definitely implement SAP Security Note #3660659, which is another good example of the successful collaboration of SAP with Onapsis.
| SAP Note | Type | Description | Priority | CVSS |
| 3634501 | Update | [CVE-2025-42944] Insecure Deserialization vulnerability in SAP Netweaver (RMI-P4) BC-JAS-COR-RMT | HotNews | 10.0 |
| 3660659 | New | [CVE-2025-42944] Security Hardening for Insecure Deserialization in SAP NetWeaver AS Java BC-JAS-COR | HotNews | 10.0 |
| 3643865 | Update | [CVE-2025-42922] Insecure File Operations vulnerability in SAP NetWeaver AS Java (Deploy Web Service) BC-JAS-DPL | HotNews | 9.9 |
| 3630595 | New | [CVE-2025-42937] Directory Traversal vulnerability in SAP Print Service BC-CCM-PRN | HotNews | 9.8 |
| 3302162 | Update | [CVE-2023-27500] Directory Traversal vulnerability in SAP NetWeaver AS for ABAP and ABAP Platform BC-DOC-RIT | HotNews | 9.6 |
| 3647332 | New | [CVE-2025-42910] Unrestricted File Upload Vulnerability in SAP Supplier Relationship Management SRM-UIA-SHP-BD | HotNews | 9.0 |
| 3664466 | New | [CVE-2025-5115] Denial of service (DOS) in SAP Commerce Cloud (Search and Navigation) CEC-SCC-COM-SRC-SER | High | 7.5 |
| 3658838 | New | [CVE-2025-48913]Security Misconfiguration vulnerability in SAP Data Hub Integration Suite CEC-SCC-INT-HUB | High | 7.1 |
| 3635587 | Update | [CVE-2025-42912] Missing Authorization check in SAP HCM (My Timesheet Fiori 2.0 application) PA-FIO-TS | Medium | 6.5 |
| 3643832 | Update | [CVE-2025-42917] Missing Authorization check in SAP HCM (Approve Timesheets Fiori 2.0 application) PA-FIO-TS | Medium | 6.5 |
| 3503138 | Update | [CVE-2025-0059] Information Disclosure vulnerability in SAP NetWeaver Application Server ABAP (applications based on SAP GUI for HTML) BC-FES-WGU | Medium | 6.0 |
| 3652788 | New | [CVE-2025-42901] Code Injection vulnerability in SAP Application Server for ABAP (BAPI Browser) BC-MID-API | Medium | 5.4 |
| 3642021 | New | [CVE-2025-42908] Cross-Site Request Forgery (CSRF) vulnerability in SAP NetWeaver Application Server for ABAP BC-ABA-SC | Medium | 5.4 |
| 3409013 | Update | [CVE-2025-42915] Missing Authorization Check in Fiori app (Manage Payment Blocks) FI-FIO-AP-PAY | Medium | 5.4 |
| 3627308 | New | [CVE-2025-42902] Memory Corruption vulnerability in SAP Netweaver AS ABAP and ABAP Platform BC-SEC-LGN | Medium | 5.3 |
| 3634724 | New | [CVE-2025-42906] Directory Traversal vulnerability in SAP Commerce Cloud CEC-SCC-PLA-PL | Medium | 5.3 |
| 3656781 | New | [CVE-2025-42903] User Enumeration and Sensitive Data Exposure via RFC Function in SAP Financial Service Claims Management FS-CM | Medium | 4.3 |
| 3625683 | New | [CVE-2025-42939] Missing Authorization Check in SAP S/4HANA (Manage Processing Rules – For Bank Statements) FI-FIO-AR-PAY | Medium | 4.3 |
| 3577131 | New | [CVE-2025-31331] Authorization Bypass vulnerability in SAP NetWeaver CA-GTF-TS-GMA | Medium | 4.3 |
| 3623504 | Update | [CVE-2025-42918] Missing Authorization check in SAP NetWeaver Application Server for ABAP (Background Processing) BC-CCM-BTC | Medium | 4.3 |
| 3540622 | Update | [CVE-2025-42907] Server-Side Request Forgery in SAP BI Platform BI-BIP-SRV | Medium | 4.3 |
| 3617142 | New | [CVE-2025-31672] Deserialization Vulnerability in SAP BusinessObjects (Web Intelligence and Platform Search) BI-RA-WBI | Medium | 3.5 |
| 3643871 | New | [CVE-2025-42909] Security Misconfiguration vulnerability in SAP Cloud Appliance Library Appliances BC-VCM-CAL | Medium | 3.0 |
As always, the Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Monthly Newsletter.
