SAP Security Notes: November 2025 Patch Day

Critical Vulnerabilities in SQL Anywhere Monitor and SAP Solution Manager
Highlights of November SAP Security Notes analysis include:
- November Summary — Twenty-six new and updated SAP security patches released, including four HotNews Notes and two High Priority Notes
- SQL Anywhere Monitor — Hard-coded credentials allow attackers to execute arbitrary code
- Onapsis Research Labs Contribution — Our team supported SAP in patching eight vulnerabilities, covered by seven SAP Security Notes
SAP has published twenty-six new and updated SAP Security Notes in its November Patch Day, including four HotNews Notes and two High Priority Notes. Seven of the eighteen new Security Notes were published in contribution with the Onapsis Research Labs.
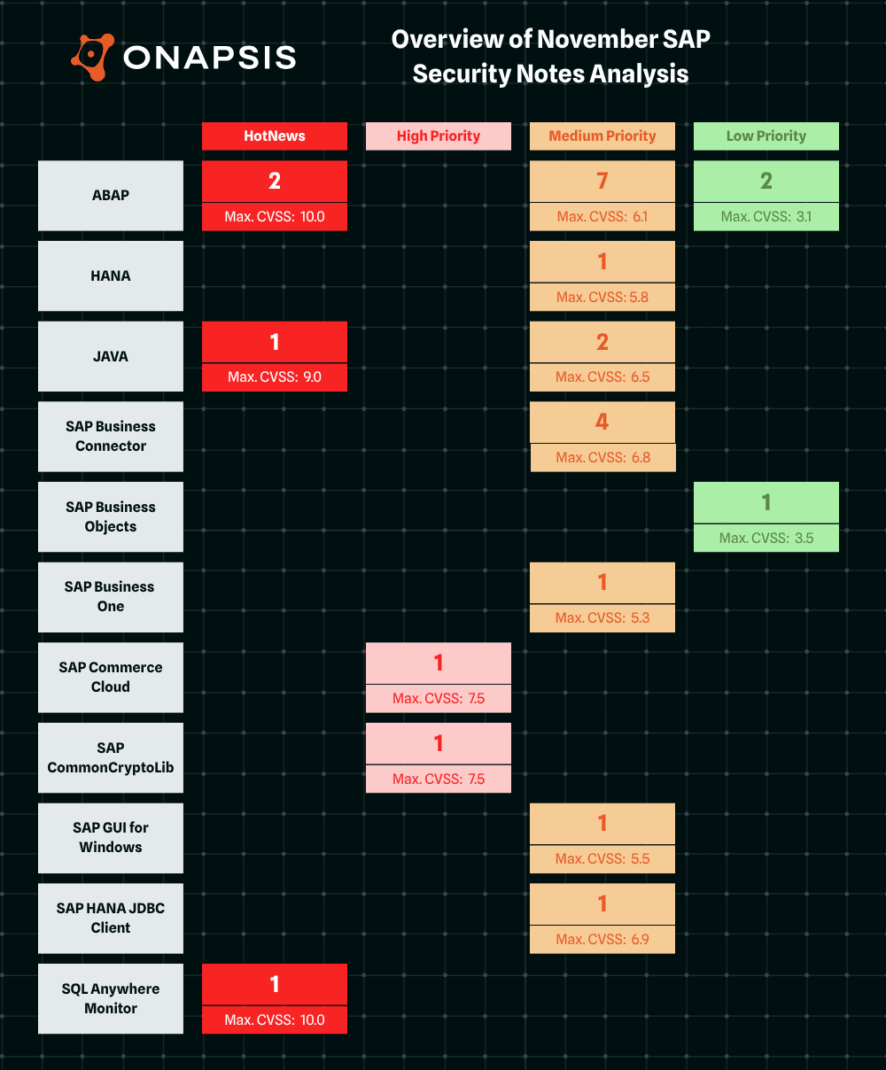
The HotNews Notes in Detail
SAP Security Note #3666261, tagged with a CVSS score of 10.0, patches an Insecure key & Secret Management vulnerability in SQL Anywhere Monitor. Hard-coded credentials allow attackers to execute arbitrary code. A successful exploit poses the system’s confidentiality, integrity, and availability at high risk. The patch removes the SQL Anywhere Monitor completely. As a temporary workaround, SAP recommends to stop using SQL Anywhere Monitor and to delete any instances of SQL Anywhere Monitor database.
The second new HotNews SAP Security Note patches a Code Injection vulnerability in SAP Solution Manager. Due to missing input sanitization in an remote-enabled function module, authenticated attackers are able to inject malicious code into the system. SAP Security Note #3668705, tagged with a CVSS score of 9.9, patches this vulnerability through adding an input check that rejects most of the non-alphanumeric characters.
SAP Security Note #3660659, tagged with a CVSS of 10.0, was initially released in collaboration with Onapsis on SAP’s October Patch Day. The patch blocks vulnerable JDK and third-party classes in SAP NetWeaver AS Java to prevent the exploit of Insecure Deserialization vulnerabilities. SAP has added a pre-requisite note and re-structured the workaround section.
SAP Security Note #3647332, tagged with a CVSS score of 9.0, was also initially released in collaboration with Onapsis in October. The patched vulnerability in SAP Supplier Relationship Management allows an authenticated attacker to upload arbitrary files which could host malware. SAP has updated the note with extended validity information.
The High Priority Notes in Detail
SAP Security Note #3633049, tagged with a CVSS score of 7.5, patches a Memory Corruption vulnerability in SAP CommonCryptoLib. Missing boundary checks enable an attacker to send malicious data which could result in memory corruption followed by an application crash. The issue is fixed as of CommonCryptoLib 8.5.60. The note points out that some components include CommonCryptoLib and refers to SAP Note #3628110 for the respective Patch Levels. An additional KBA note is in preparation (SAP Note #3677814).
SAP Security Note #3664466 is an update on a Denial of Service vulnerability in SAP Commerce Cloud. The note is tagged with a CVSS score of 7.5 and includes changes in the ‘Symptom’, ‘Reason and Prerequisites’, and ‘Solution’ section.
Onapsis Contribution
Once again, the Onapsis Research Labs (ORL) could contribute significantly to SAP’s Patch Day. No less than seven SAP Security Notes were published today in collaboration with the ORL including four patches for SAP Business Connector.
SAP Business Connector (BC) is a relatively old component that can be installed and managed independently of the SAP system. SAP BC enables the extension of business processes via the internet and the integration of non-SAP products using open standards. It was first released in 1999 and has been superseded by newer technologies like SAP Process Orchestration and SAP CLoud Platform Integration. But the fact that its maintenance end has been repeatedly postponed from the end of 2020 to the end of 2030 shows that it is still very popular and widespread.
SAP Security Note #3665900, tagged with a CVSS score of 6.8, patches an OS Command Injection vulnerability in SAP BC. The vulnerability allows an authenticated attacker with administrative access and adjacent network access to upload specially crafted content to the server. If such content is processed by the application, execution of arbitrary OS commands becomes possible leading to a full compromise of the system.
SAP Security Note #3666038, tagged with a CVSS score of 6.8, patches a Path Traversal vulnerability detected by the ORL team. The team realized that an attacker authenticated as an administrator with adjacent access could read, write, overwrite, and delete arbitrary files on the host system. Successful exploitation could enable the attacker to execute arbitrary operating system commands on the server, resulting in a complete compromise of the confidentiality, integrity, and availability of the affected system.
SAP Security Note #3665907, tagged with a CVSS score of 6.1, addresses a Reflected Cross-Site Scripting (XSS) vulnerability in SAP BC. If not patched, an unauthenticated attacker could generate a malicious link and make it publicly accessible. If the link is accessed subsequently by an authenticated victim, the injected input is processed during web page generation and the malicious content is executed in the victim’s browser context.
An Open Redirect Vulnerability in SAP BC was patched by SAP in collaboration with the ORL team with SAP Security Note #3662000, tagged with a CVSS score of 6.1. The vulnerability allows an unauthenticated attacker to craft a malicious URL that, if accessed by a victim, redirects them to an attacker-controlled site displayed within an embedded frame. Successful exploitation could allow the attacker to steal sensitive information and perform unauthorized actions, partially impacting the confidentiality and integrity of web client data.
The ORL team detected a JNDI Injection Vulnerability in SAP NetWeaver Enterprise Portal that is patched with SAP Security Note #3660969, tagged with a CVSS score of 6.5. Unauthenticated attackers can inject JNDI environment properties or pass a URL used during JNDI lookup operations, enabling access to an unintended JNDI provider. This could lead to disclosure or modification of information about the server.
Multiple Open Redirect vulnerabilities were detected by our team in SAP S/4HANA landscape SAP E-Recruiting BSP. They allow an unauthenticated attacker to craft malicious links. Clicked by a victim, they could be redirected to a page controlled by the attacker. The issue is patched with SAP Security Note #3642398, tagged with a CVSS score of 6.1.
A Missing Authentication vulnerability in SAP HANA 2.0 (hdbrss) is patched with SAP Security Note #3639264, tagged with a CVSS score of 5.8. Our team detected that the application allows an unauthenticated attacker to call a remote-enabled function that will enable them to view information which causes low impact on confidentiality.
Summary & Conclusions
SAP’s November Patch Day comes with critical patches for SQL Anywhere Monitor and SAP Solution Manager. With seven SAP Security Notes, the Onapsis Research Labs has contributed once more significantly to the protection of all SAP customers.
| SAP Note | Type | Description | Priority | CVSS |
| 3666261 | New | [CVE-2025-42890] Insecure key & Secret Management vulnerability in SQL Anywhere Monitor (Non-Gui) BC-SYB-SQA-ADM | HotNews | 10 |
| 3660659 | Update | [CVE-2025-42944] Security Hardening for Insecure Deserialization in SAP NetWeaver AS Java BC-JAS-COR | HotNews | 10 |
| 3668705 | New | [CVE-2025-42887] Code Injection vulnerability in SAP Solution Manager SV-SMG-SVD-SWB | HotNews | 9.9 |
| 3647332 | Update | [CVE-2025-42910] Unrestricted File Upload Vulnerability in SAP Supplier Relationship Management SRM-UIA-SHP-BD | HotNews | 9 |
| 3633049 | New | [CVE-2025-42940] Memory Corruption vulnerability in SAP CommonCryptoLib BC-IAM-SSO-CCL | High | 7.5 |
| 3664466 | Update | [CVE-2025-5115] Denial of service (DOS) in SAP Commerce Cloud (Search and Navigation) CEC-SCC-COM-SRC-SER | High | 7.5 |
| 3643385 | New | [CVE-2025-42895 ] Code Injection vulnerability in SAP HANA JDBC Client HAN-DB-CLI | Medium | 6.9 |
| 3665900 | New | [CVE-2025-42892] OS Command Injection vulnerability in SAP Business Connector BC-MID-BUS | Medium | 6.8 |
| 3666038 | New | [CVE-2025-42894] Path Traversal vulnerability in SAP Business Connector BC-MID-BUS | Medium | 6.8 |
| 3660969 | New | [CVE-2025-42884] JNDI Injection vulnerability in SAP NetWeaver Enterprise Portal EP-PIN-APF-CAT | Medium | 6.5 |
| 3642398 | New | [CVE-2025-42924] Open Redirect vulnerabilities in SAP S/4HANA landscape (SAP E-Recruiting BSP) PA-ER | Medium | 6.1 |
| 3662000 | New | [CVE-2025-42893] Open Redirect vulnerability in SAP Business Connector BC-MID-BUS | Medium | 6.1 |
| 3665907 | Update | [CVE-2025-42886] Reflected Cross-Site Scripting (XSS) vulnerability in SAP Business Connector BC-MID-BUS | Medium | 6.1 |
| 3597355 | Update | [CVE-2025-42942] Cross-Site Scripting (XSS) vulnerability in SAP NetWeaver Application Server for ABAP BC-MID-ICF | Medium | 6.1 |
| 3639264 | New | [CVE-2025-42885] Missing authentication in SAP HANA 2.0 (hdbrss) HAN-DB-ENG | Medium | 5.8 |
| 3651097 | New | [CVE-2025-42888] Information Disclosure vulnerability in SAP GUI for Windows BC-FES-GUI | Medium | 5.5 |
| 2886616 | New | [CVE-2025-42889] SQL Injection vulnerability in SAP Starter Solution (PL SAFT) FI-LOC-SAF-PL | Medium | 5.4 |
| 3441087 | Update | [CVE-2025-42984] Missing Authorization check in SAP S/4HANA (Manage Central Purchase Contract application) MM-PUR-HUB-CTR | Medium | 5.4 |
| 3643603 | New | [CVE-2025-42919] Information Disclosure vulnerability in SAP NetWeaver Application Server Java BC-JAS-WEB | Medium | 5.3 |
| 3652901 | New | [CVE-2025-42897] Information Disclosure vulnerability in SAP Business One (SLD) SBO-BC-SLD | Medium | 5.3 |
| 3627644 | Update | [CVE-2025-42911] Missing Authorization check in SAP NetWeaver (Service Data Download) SV-SMG-SDD | Medium | 5 |
| 3643337 | New | [CVE-2025-42882] Missing Authorization check in SAP NetWeaver Application Server for ABAP BC-DB-DB6 | Medium | 4.3 |
| 3530544 | New | [CVE-2025-42899] Missing Authorization check in SAP S4CORE (Manage Journal Entries) FI-FIO-GL-TRA | Medium | 4.3 |
| 3617142 | Update | [CVE-2025-31672] Deserialization Vulnerability in SAP BusinessObjects (Web Intelligence and Platform Search) BI-RA-WBI | Low | 3.5 |
| 3426825 | New | [CVE-2025-23191] Cache Poisoning through header manipulation vulnerability in SAP Fiori for SAP ERP OPU-GW-COR | Low | 3.1 |
| 3634053 | New | [CVE-2025-42883] Insecure File Operations vulnerability in SAP NetWeaver Application Server for ABAP (Migration Workbench) BC-SRV-DX-DXW | Low | 2.7 |
As always, the Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
To review the strategic importance of this monthly patch cycle and the process of continuous vulnerability remediation, see our full SAP Patch Day overview.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Monthly Newsletter.
