SAP Security Patch Day March 2022: SAP Focused Run Affected by Several Vulnerabilities

Highlights of March SAP Security Notes analysis include:
- March Summary – 17 new and updated SAP security patches released, including four HotNews Notes and one High Priority Note
- Most critical patch for SAP Focused Run – CVSS 9.3 vulnerability which can lead to full compromise of the affected systems
- Onapsis Research Labs Collaboration – Onapsis Research Labs contributed to fixing four new vulnerabilities
Time to breathe… After the shock waves that went through the SAP community with Log4j and ICMAD, SAP’s March Patch Tuesday is a calmer one.
SAP has published 17 new and updated Security Notes on its March Patch Day (including the notes that were released or updated since last Patch Tuesday). This includes four HotNews Notes and one High Priority Note.
One of the four HotNews Notes is an update of the critical ICMAD note #3123396 that was initially released on February’s Patch Day. It contains some additional information, including a reference to the Knowledge Base Article #3148968 which contains an FAQ about the patch.
The HotNews Notes in Detail
SAP Security Note #3154684, tagged with a CVSS score of 10.0, is another Log4j patch. It affects the SAP Work Manager and SAP Inventory application. Both applications run on SAP Mobile Platform (SMP) and only on-premise installations of the SMP are affected. The note recommends upgrading to SAP Work Manager 6.6.1 and/or SAP Inventory Manager 4.4.1 since these application versions were built with the new library versions of the log4j library. As a workaround, a direct replacement of the vulnerable log4j library on the SMP server can be implemented. Due to the fact that SAP Work Manager versions prior to 6.4 do not use log4j libraries, they are not affected by the Log4j vulnerabilities.
HotNews Note #3131047 is the central SAP Security Note for the Log4j vulnerability and was updated with information about the new note #3154684.
The central SAP document on Log4j was last updated on March 7. Log4j patches are still pending for:
- Customer Applications on BTP Cloud Foundry Environment
- SAP Commerce Cloud (in Public Cloud)
- SAP Commerce Cloud (in SAP Infrastructure V1.0 and V1.2)
- SAP Commerce (On-Premise)
- SAP Contact Center 7.0
The good news is that workarounds are available for all of these applications.
SAP Security Note #3145987, tagged with a CVSS score of 9.3, patches a Missing Authentication vulnerability in the SAP Simple Diagnostics Agent. This agent is installed and deployed as an add-on to the SAP Host Agent and it is a prerequisite for using the Simple System Integration (SSI) in SAP Focused Run.
The Onapsis Research Labs detected the critical vulnerability which allows an attacker to access administrative or other privileged functionalities and read, modify, or delete sensitive information and configurations. The only thing that prevents it from being tagged with a CVSS score of 10 is that, for a successful exploit to occur, local OS access to the SAP Focused Run system — or to one of the managed systems — is required. However, a successful exploit can lead to a complete compromise of the affected system.
In order to patch the vulnerability, SAP customers need to update both the SAP Simple Diagnostics Agent and the SAP Host Agent.
Other SAP Security Notes Released in Collaboration With the Onapsis Research Labs
The Onapsis Research Labs contributed significantly to this SAP Patch Tuesday. In addition to supporting SAP in patching the Missing Authentication vulnerability described in HotNews Note #3145987, assistance was given to SAP with patching three other vulnerabilities, one of them rated with High Priority.
SAP Security Note #3149805, tagged with a CVSS score of 8.2, patches a Cross-Site Scripting (XSS) vulnerability in SAP Fiori launchpad. Our research team detected that SAP Fiori launchpad allows an unauthenticated attacker to manipulate the SAP-theme URL parameter — and inject HTML code — and create a link over the network for a user to click on. Once the link is clicked, successful exploitation allows the attacker to hijack user privileges that can be used to exfiltrate data and craft a CSRF attack to manipulate data. This can limit the application’s confidentiality and pose risks to its integrity, as well as increase the likelihood of it being completely compromised.
Since SAP Focused Run was the focus of its current investigation, the Onapsis Research Labs also helped SAP with patching two additional vulnerabilities for that application:
SAP Security Note #3147283, tagged with a CVSS score of 5.4, patches a Cross-Site Scripting (XSS) vulnerability in the Real User Monitoring application of SAP Focused Run. Insufficient input validation in the SAP Focused Run REST can lead to a remote attack, but with limited impact on the system’s confidentiality and integrity.
SAP Security Note #3147102, tagged with a CVSS score of 5.3, patches another vulnerability in the SAP Diagnostics Agent. A successful exploit allows an attacker to gather information that can be used to exploit open source security exploits in the future.
Summary and Conclusion
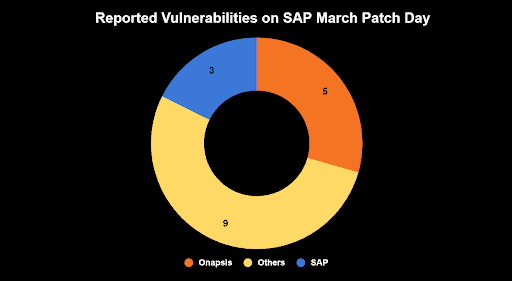
With 17 new and updated Security Notes, including four HotNews Notes (with two of them being new) and one High Priority Note, this is finally a calmer Patch Day for SAP customers. 14 of the 17 patched vulnerabilities were reported by external contributors and 5 of these by the Onapsis Research Labs. This demonstrates the importance of external researchers, like Onapsis Research Labs, to the SAP ecosystem. As a major provider for software solutions protecting business-critical applications, Onapsis continues to invest in its research and proactively analyze and investigate developments in business-critical applications to deliver security insights and threat intelligence.
Onapsis Research Labs automatically updates The Onapsis Platform with the latest threat intelligence and security guidance so that our customers can stay ahead of ever-evolving threats and protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Newsletter.
