SAP Security Patch Day July 2021: Serious Vulnerabilities in SAP NetWeaver AS Java fixed

Highlights of July SAP Security Notes analysis include:
- July Summary—16 new and updated SAP security patches released, including two HotNews Notes and two High Priority Notes
- Highest CVSS Score of Patched Vulnerabilities is 8.8—New SAP Business Client patch includes Google Chromium 91.0.4472.101
- Onapsis Research Labs Collaboration—Our team has helped SAP in fixing two vulnerabilities in SAP NetWeaver AS Java – one rated with High Priority
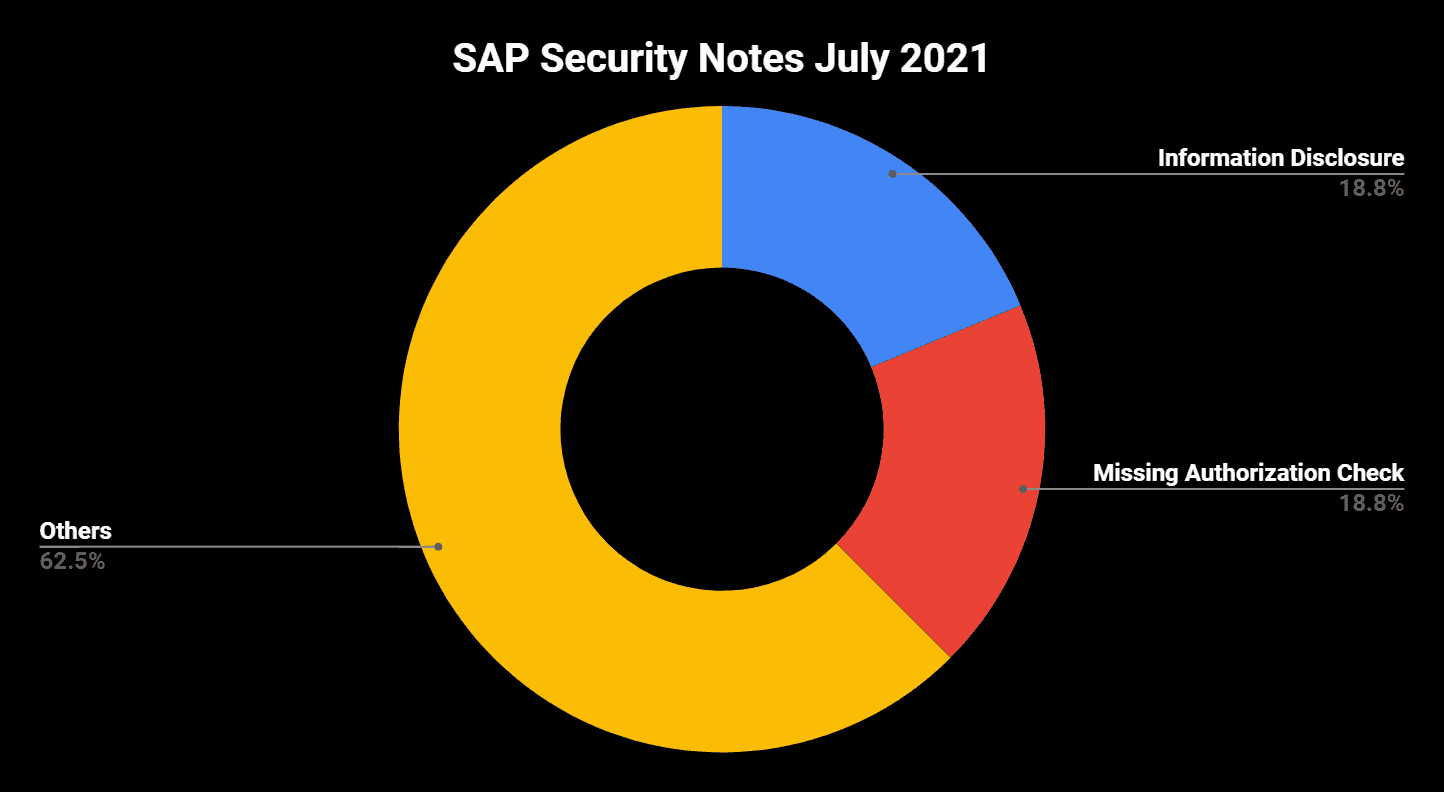
SAP® has published 16 new and updated Security Notes on its July Patch Day. This number includes two HotNews Notes and two High Priority Notes.
However, upon deeper analysis of the most important Security Notes, it is clear that SAP’s July Patch Day is mostly uneventful.
The vulnerability with the highest CVSS is patched with the newest SAP Business Client update provided with HotNews Note #2622660. The vulnerabilities that are fixed with the included Google Chromium update have a maximum CVSS score of 8.8 (Keep in mind that the CVSS score of 10, associated with the note, represents the all-time high of all vulnerabilities patched with this note in the past). Because of this, the note is considered to be a de facto High Priority Note rather than a HotNews Note. The included Google Chromium version 91.0.4472.101 comes with 67 patches, with one of them rated as Critical and 28 rated with High Priority (the last two numbers only consider externally reported vulnerabilities). The critical patch, together with the fact that Google has confirmed that the patched High Priority vulnerability related to CVE-2021-30551has already been exploited in the wild, means that SAP Business customers should apply the new SAP Business Client update immediately.
The second HotNews Note, SAP Security Note #3007182, is tagged with a CVSS score of 9.0 (and thus formally with a higher CVSS score than note #2622660) but it includes just a minor update on a vulnerability that was initially fixed on June’s Patch Day. SAP has added an additional SP Stack Kernel version to the support packages section.
In Focus: SAP NetWeaver AS Java
SAP has released two High Priority Notes on its July Patch Day:
SAP Security Note #3059446, tagged with a CVSS score of 7.6, patches a Missing Authorization vulnerability in SAP NetWeaver Guided Procedures (SAP GP).
SAP GP is part of the Composite Application Framework (CAF) and allows the modelling and management of workflows. It provides role-based access to tools, resources and guidance through the workflows at runtime and helps end users easily identify and complete their tasks. SAP GP enables access to multiple backend systems, consistently combining different types of services and applications into processes. In addition, GP supports collaboration, ad-hoc items, and offline task management using interactive forms.
The Missing Authorization vulnerability was found in the Administration Workset component of SAP GP. It represents the central administration tool for GP and allows a wide range of activities, like:
- Execute general administration tasks related to the GP design time, runtime and background frameworks
- Manage transports
- Manage archiving and deleting jobs
- Configure forms
- Control communication with SAP Systems
A Missing Authorization Check could lead to unauthorized reading, modification, or deletion of data. Fortunately, there is also a workaround available for fixing the issue – just disable the corresponding application in SAP NetWeaver Administrator if it is not required.
The second High Priority Note, SAP Security Note #3056652, is tagged with a CVSS score of 7.5. Its release is a result of the continuous collaboration between Onapsis Research Labs and SAP. Some weeks ago, the Onapsis team detected that an SAP NetWeaver AS for Java does not perform a proper validation of HTTP requests when storing monitoring data. This could allow an attacker to manipulate HTTP requests and might lead to an exhaustion of system resources, directly impacting the system’s availability. An exploit of this vulnerability is quite simple as the attack complexity is low and doesn’t require privileges or user interaction to perform an attack.
Further Contribution by Onapsis Research Labs
Onapsis Research Labs helped SAP in patching an Information Disclosure vulnerability in SAP Enterprise Portal. The correction is provided with SAP Security Note #3059764, tagged with a CVSS score of 4.5. One HTTP endpoint of the portal exposes sensitive information that could be used by an attacker with administrator privileges, in conjunction with other attacks (e.g. XSS). Since there is a wide range of possible impacts related to these attacks, Onapsis recommends implementing the provided patch as soon as possible, regardless of the relatively low CVSS score.
Summary and Conclusions
Since there are only two updated HotNews Notes and two new High Priority Notes, SAP’s July Patch Day can be considered a fairly uneventful patch day. One lesson learned from SAP Security Note #3059764: is that a note’s CVSS score does not necessarily take into account the worst case scenario. The assigned numerical level of severity does not consider the impact of subsequent attacks that could occur or attacks that might gain a broader attack surface through an exploit of the given vulnerability.
As always, Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.
