SAP Security Notes: September 2025 Patch Day Analysis

September Patch Day: Key Highlights and a Critical Warning
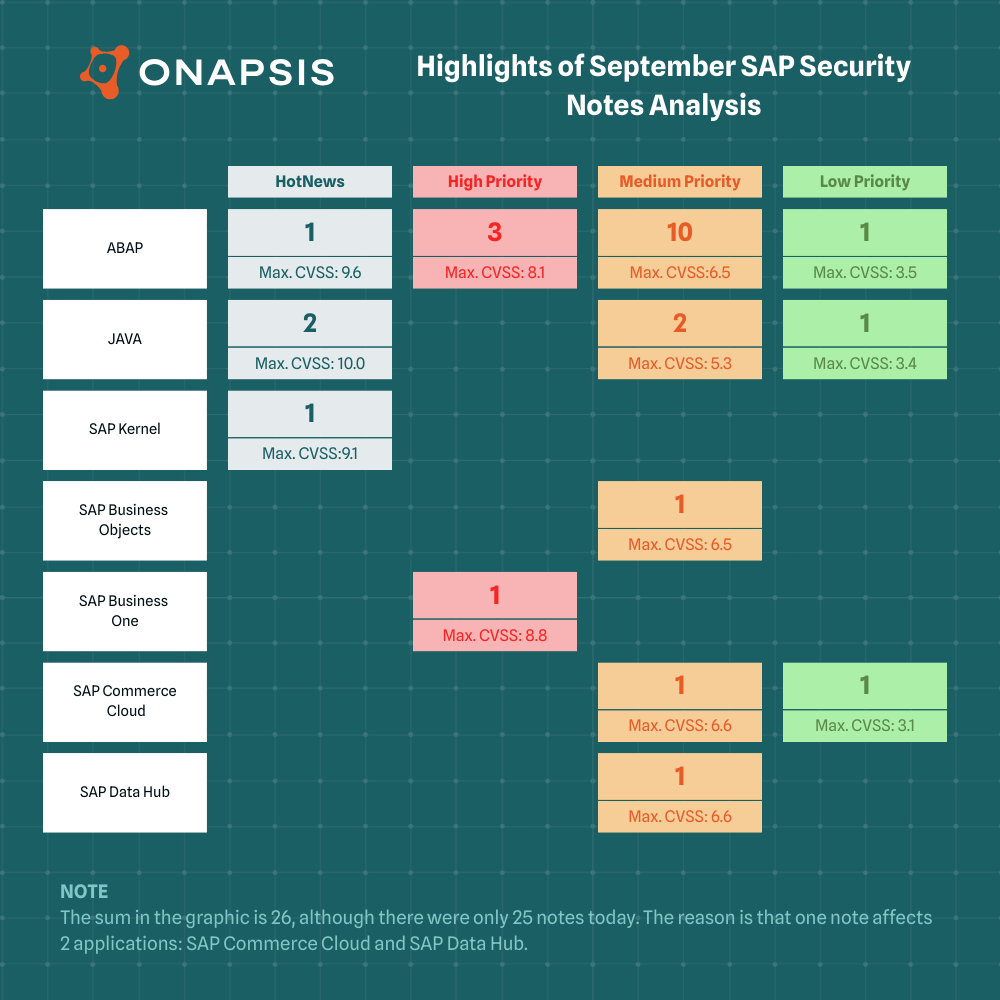
SAP has published twenty-five new and updated SAP Security Notes in its September Patch Day, including four HotNews Notes and four High Priority Notes. Seven of the twenty-one new Security Notes were published in contribution with the Onapsis Research Labs.
This month’s SAP Patch Day delivered a busy set of critical and high-priority notes. Here is a brief rundown of the key highlights from our analysis:
Key Highlights from Our September 2025 Analysis
- September Summary — Twenty-five new and updated SAP security patches released, including four HotNews Notes and four High Priority Notes
- SAP NW AS Java — Two critical HotNews SAP Security Notes released
- Onapsis Research Labs Contribution — Our team supported SAP in patching seven vulnerabilities, covered by two HotNews and five Medium Priority SAP Security Notes
HotNews Notes: Analyzing Critical Vulnerabilities
The Onapsis Research Labs (ORL) supported SAP in patching two critical vulnerabilities in SAP NetWeaver AS Java.
SAP Security Note #3634501, tagged with the highest possible CVSS score of 10.0, patches an Insecure Deserialization vulnerability in the RMI-P4 module of an AS Java. The vulnerability allows an unauthenticated attacker to execute arbitrary OS commands by submitting malicious payload to an open port. A successful exploit can lead to full compromise of the application. As a temporary workaround, customers should add P4 port filtering at the ICM level to prevent unknown hosts from connecting to the P4 port.
SAP Security Note #3643865, tagged with a CVSS score of 9.9, addresses an Insecure File Operations vulnerability in SAP NetWeaver AS Java. The ORL team detected a service flaw that allows an attacker, authenticated as a non-administrative user, to upload arbitrary files. On file execution, the system can be fully compromised.
The third new HotNews Note is SAP Security Note #3627373, tagged with a CVSS score of 9.1. The note patches a Missing Authentication Check in SAP NetWeaver applications running on IBM i-series. High privileged unauthorized users are able to read, modify, or delete sensitive information, as well as access administrative or privileged functionalities.
SAP HotNews Note #3302162, tagged with a CVSS score of 9.6, was initially released in March 2023 and patches a Directory Traversal vulnerability in SAP NetWeaver AS ABAP. The note was updated with additional correction instructions.
A Closer Look at High Priority Vulnerabilities
SAP Security Note #3642961, tagged with a CVSS score of 8.8, patches an Insecure Storage of Sensitive Information vulnerability in the System Landscape Directory backend service of SAP Business One. Due to a lack of proper encryption of some APIs, sensitive credentials could be exposed within the HTTP response body resulting in a high impact on the confidentiality, integrity, and availability of the application.
SAP S/4HANA (Private Cloud or On-Premise) is affected by High Priority SAP Security Note #3635475, tagged with a CVSS score of 8.1. An ABAP report of the application allows the deletion of arbitrary tables, that are not protected by an authorization group, leading to a high impact on integrity and availability of the database.
SAP Security Note #3633002 patches the same vulnerability in SAP Landscape Transformation Replication Server.
SAP Security Note #3581811 was initially released in April 2025. The note is tagged with a CVSS score of 7.7 and patches a Directory Traversal vulnerability in SAP NetWeaver and ABAP Platform (Service Data Collection). The note has been re-released with updated correction instructions.
Onapsis Research Labs’ Contributions
In addition to the two vulnerabilities in SAP NetWeaver AS Java that were patched by HotNews Notes, the ORL team supported SAP in fixing five Medium Priority vulnerabilities.
SAP Security Note #3614067, tagged with a CVSS score of 6.5, patches a Denial of Service vulnerability in SAP Business Planning and Consolidation. The ORL team identified a remote-enabled function module, whose parameters could be crafted by authenticated standard users to cause an almost infinite loop, consuming excessive resources and resulting in system unavailability.
SAP Security Note #3629325, tagged with a CVSS score of 6.1, describes a Cross-Site Scripting (XSS) vulnerability in SAP NetWeaver ABAP Platform. Due to insufficient encoding of URL parameters an unauthenticated attacker could generate a malicious link and make it publicly accessible. If an authenticated user clicks on this link, the injected input is processed during the website’s page generation, resulting in the creation of malicious content. When executed, this content allows the attacker to access or modify information within the victim’s browser scope, impacting the confidentiality and integrity while availability remains unaffected.
SAP Security Note #3647098, tagged with a CVSS score of 6.1, patches another XSS vulnerability in SAP Supplier Relationship Management. A possible exploit and the impact is exactly the same as for SAP Security Note #3629325.
The ORL team identified a remote-enabled function module in SAP NetWeaver (Service Data Download) that could grant access to information about the SAP system and operating system. The vulnerability is patched with SAP Security Note #3627644, tagged with a CVSS score of 5.0, by adding a proper authorization check to the function module.
SAP Security Note #3640477, tagged with a CVSS score of 4.3, patches a Predictable Object Identifier vulnerability in the IIOP service of SAP NetWeaver AS Java. A lack of randomness in assigning Object Identifiers in the IIOP service allows an authenticated attacker with low privileges to easily predict the identifiers. This could enable them to get access to limited system information.
Summary and Final Recommendations
With twenty-five Security Notes, including four HotNews Note and four High Priority Notes, SAP’s September Patch Day is another busy one. Special attention should be paid to the two critical HotNews Notes for SAP NetWeaver AS Java that were patched in collaboration with the Onapsis Research Labs.
| SAP Note | Type | Description | Priority | CVSS |
| 3634501 | New | [CVE-2025-42944] Insecure Deserialization vulnerability in SAP Netweaver (RMI-P4) BC-JAS-COR-RMT | HotNews | 10.0 |
| 3643865 | New | [CVE-2025-42922] Insecure File Operations vulnerability in SAP NetWeaver AS Java (Deploy Web Service) BC-JAS-DPL | HotNews | 9.9 |
| 3302162 | Update | [CVE-2023-27500] Directory Traversal vulnerability in SAP NetWeaver AS for ABAP and ABAP Platform BC-DOC-RIT | HotNews | 9.6 |
| 3627373 | New | [CVE-2025-42958] Missing Authentication check in SAP NetWeaver BC-OP-AS4 | HotNews | 9.1 |
| 3642961 | New | [CVE-2025-42933] Insecure Storage of Sensitive Information in SAP Business One (SLD) SBO-BC-SLD | High | 8.8 |
| 3635475 | New | [CVE-2025-42916] Missing input validation vulnerability in SAP S/4HANA (Private Cloud or On-Premise) CA-DT-CNV-BAS | High | 8.1 |
| 3633002 | New | [CVE-2025-42929] Missing input validation vulnerability in SAP Landscape Transformation Replication Server CA-LT-OBT | High | 8.1 |
| 3581811 | Update | [CVE-2025-27428] Directory Traversal vulnerability in SAP NetWeaver and ABAP Platform (Service Data Collection) SV-SMG-SDD | High | 7.7 |
| 3620264 | New | [CVE-2025-22228] Security Misconfiguration vulnerability in Spring security within SAP Commerce Cloud and SAP Datahub CEC-SCC-PLA-PL | Medium | 6.6 |
| 3643832 | New | [CVE-2025-42917] Missing Authorization check in SAP HCM (Approve Timesheets Fiori 2.0 application) PA-FIO-TS | Medium | 6.5 |
| 3635587 | New | [CVE-2025-42912] Missing Authorization check in SAP HCM (My Timesheet Fiori 2.0 application) PA-FIO-TS | Medium | 6.5 |
| 3614067 | New | [CVE-2025-42930] Denial of Service (DoS) vulnerability in SAP Business Planning and Consolidation EPM-BPC-NW-SQE | Medium | 6.5 |
| 3611420 | New | [CVE-2023-5072] Denial of Service (DoS) vulnerability due to outdated JSON library used in SAP BusinessObjects Business Intelligence Platform BI-BIP-INV | Medium | 6.5 |
| 3629325 | New | [CVE-2025-42938] Cross-Site Scripting (XSS) vulnerability in SAP NetWeaver ABAP Platform CRM-BF-ML | Medium | 6.1 |
| 3647098 | New | [CVE-2025-42920] Cross-Site Scripting (XSS) vulnerability in SAP Supplier Relationship Management SRM-EBP-TEC-ITS | Medium | 6.1 |
| 3409013 | New | [CVE-2025-42915] Missing Authorization Check in Fiori app (Manage Payment Blocks) FI-FIO-AP | Medium | 5.4 |
| 3619465 | New | [CVE-2025-42926] Missing Authentication check in SAP NetWeaver Application Server Java BC-WD-JAV | Medium | 5.3 |
| 3627644 | New | [CVE-2025-42911] Missing Authorization check in SAP NetWeaver (Service Data Download) SV-SMG-SDD | Medium | 5.0 |
| 3610322 | Update | [CVE-2025-42961] Missing Authorization check in SAP NetWeaver Application Server for ABAP BC-DB-DBI | Medium | 4.9 |
| 3623504 | New | [CVE-2025-42918] Missing Authorization check in SAP NetWeaver Application Server for ABAP (Background Processing) BC-CCM-BTC | Medium | 4.3 |
| 3450692 | New | [CVE-2025-42923] Cross-Site Request Forgery (CSRF) vulnerability in SAP Fiori App (F4044 Manage Work Center Groups) PP-BD-WKC | Medium | 4.3 |
| 3640477 | New | [CVE-2025-42925] Predictable Object Identifier vulnerability in SAP NetWeaver AS Java (IIOP Service) BC-JAS-COR-RMT | Medium | 4.3 |
| 3624943 | New | [CVE-2025-42941] Reverse Tabnabbing vulnerability in SAP Fiori (Launchpad) CA-FLP-FE-COR | Low | 3.5 |
| 3525295 | New | [CVE-2025-42927] Information Disclosure due to Outdated OpenSSL Version in SAP NetWeaver AS Java (Adobe Document Service) BC-SRV-FP | Low | 3.4 |
| 3632154 | New | [CVE-2024-13009] Potential Improper Resource Release vulnerability in SAP Commerce Cloud CEC-SCC-PLA-PL | Low | 3.1 |
To truly protect your SAP environment, immediate action is required. We strongly recommend that you begin by prioritizing the application of HotNews and High Priority security notes. This risk-based approach, combined with the use of SAP security automation tools, ensures you can address the most critical vulnerabilities swiftly and efficiently. Do not delay, as attackers often move quickly to exploit newly disclosed vulnerabilities.
As always, the Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Monthly Newsletter .
Frequently Asked Questions
Why is a structured patch management strategy critical for SAP?
A structured patch management process is essential for reducing your attack surface, ensuring compliance, and protecting business-critical data. Beyond simply applying patches, a comprehensive strategy involves prioritizing vulnerabilities based on risk and automating processes. For a deeper understanding of these best practices, review our SAP Security Notes Overview.
How can reviewing past SAP Security Notes improve our threat intelligence?
By analyzing historical patch data, organizations can gain valuable insight into evolving threat actor tactics and the types of vulnerabilities being targeted. This proactive approach allows you to better anticipate and defend against future threats. You can access all our past monthly analysis in the SAP Patch Day blog archive.
How should we prioritize patches based on SAP and CVSS scores?
Patches should be prioritized based on risk, with HotNews (CVSS 9.0-10.0) and High Priority (CVSS 7.0-8.9) notes being addressed first due to their potential for severe impact. It’s also critical to consider factors like exploit availability and whether a vulnerable system is exposed to the internet.
