SAP Security Notes November ‘18: The Mobile Client Side Menace
Today SAP released 12 security notes for November’s SAP Security Patch Day as it is scheduled. This makes a total of 16 security notes after adding the four released since October’s patch day. Among these SAP security notes there are three that fix a number of vulnerabilities reported by the Onapsis Research Labs. Two of them are critical. The first note #2657670 is for a Denial of Service (DoS) vulnerability in SAP BusinessObjects BI Suite (BOBJ) allowing an attack on its Central Management Server (CMS) and Console (CMC) that makes the BOBJ platform unresponsive. The second critical note #2691126 addresses five vulnerabilities in SAP Fiori Mobile App for Android of which the one with the highest impact is a Code Injection vulnerability that allows an attacker to spy on the user’s mobile. The third note covering an Onapsis reported vulnerability is #2695896, affecting SAP Mobile Secure for Android with a vulnerability that allows a DoS by crashing this Mobile Device Management client software.
Seven Onapsis Reported Vulnerabilities Fixed
The SAP Security Note #2657670 fixes a vulnerability reported by Onapsis Research Labs recently. This is a Denial of Service vulnerability that affects SAP BusinessObjects (BOBJ) Platform 4.1 and 4.2.
As you probably know, the BOBJ platform has the CMS that stores, in its own System Database, all the configuration data including users, folders, access rights, SSO, services, and other management data. The CMS hosts a web-based application called Central Management Console (CMC) which plays an important role for managing the BOBJ administrative tasks and security configuration. This console is served by a Tomcat web server.
The security bug resides in the BOBJ’s Web Intelligence Richclient 3 tiers mode gateway component. It was found by Onapsis researcher Gaston Traberg, and its exploitation works as follows. When a malicious actor sends a single and specifically crafted HTTP request to the CMS, the process responsible for processing that HTTP request (a Tomcat handling thread) will enter in a never-ending loop that rapidly consumes two important system resources that severely impact the server.
That looped thread has a high CPU usage and disk space usage that, if not stopped, will exhaust all available disk space making the system almost unresponsive. At that point, when no more disk space is available, many services will stop working, in particular, the proper BOBJ’s CMS, consequently not allowing the users to log in or access folders and reports, and the system administrator not being allowed use of the BOBJ’s CMC. What makes this remote attack worse is that no credentials are needed, it is an unauthenticated attack. Just by having network access is enough to exploit this vulnerability.
A possible recovery from such unexpected behavior, caused by the attack, requires for the system administrator to detect the lack of CPU response and sudden disk space shortage. The administrator may restart the whole server and then clean-up the large log files generated in the attack; another way to exit that problematic situation requires the Tomcat web server to be stopped, the large error logs cleaned and the re-start of the web server. If this is not patched the attacker will be able to drop the malicious request again and keep the system out of business. We strongly recommend patching the system as the SAP security note recommends. With OSP’s Missing Patches policy,it is possible to check if the appropriate fixes are in place.
The other critical SAP Security Note #2691126 is for SAP Fiori Mobile App for Android and brings fixes for five vulnerabilities reported by Onapsis. The most remarkable of the pack is a Code Injection vulnerability with a CVSS v3 base score: 8.6. By exploiting it an attacker has a simple way to spy on a mobile user as well as exfiltrate sensitive data of the configured SAP system.
SAP Fiori Mobile App is a native mobile client application used to communicate with the SAP Fiori server. This client is designed to be more integrated and efficient than a standard browser as a Fiori client. This application has high privileges on the Android device as can be seen in the app web page under Permissions.
The security bug resides in the core of the application and breaks Android’s sandboxing, a security mechanism for separating running programs. It was found by Onapsis researcher Yvan Genuer, and its exploitation works as follows. A malicious actor could forge a permissionless application, which once installed into the end user device, can perform arbitrary tasks into the SAP Fiori application with its high privileges without any notification.
An attacker could remotely control his malware, to exfiltrate sensitive devices contents, like all phone contacts, all calendar schedule, pictures, SAP system configuration file, and cookie sessions. This information can be used to develop more critical attacks or spying on end users, retrieve date and time of an important meeting, record audio during this interval and exfiltrate the audio file. What makes this remote control worse is that no notification will appear on the device.
The other four vulnerabilities fixed in this security note for SAP Fiori Mobile Client are: 1) a DoS (CVE-2018-2488) that allows a malicious non-privileged application to crash the Fiori mobile app making it unavailable to the user; 2) a Remote HTML Injection (CVE-2018-2491) that allows under certain circumstances the execution of arbitrary remote javascript execution or an open redirect vulnerability controlled remotely and without authentication by an attacker but needing the user interaction with the app log viewer; 3) and 4) are vulnerabilities due to Missing authorization checks that allow an arbitrary Android app to the data deletion (CVE-2018-2489) of the Fiori Client SSO configuration and the last one allows a non-authenticated application to sniff (receive) sensitive information from broadcasts (CVE-2018-2490) before the legitimate SAP Fiori client app.
We strongly recommend installing SAP Fiori Client version 1.11.5 from Google Play store to all SAP Fiori user’s mobile devices as advised by the SAP Security Note #2691126. Medium and large organizations may make use of a Mobile Device Management software (MDM) to push or enforce a client update like this. We also advise to globally avoid installing untrusted applications on the user’s mobile devices. As we already described, this is the attacker’s way for compromising the mobile. Keep in mind that the SAP Fiori Client app versions cannot be verified by OSP.
A third security note issued today to address another Onapsis reported vulnerability is tagged as Medium Priority. It is note #2695896 and fixes a new vulnerability that affects the Android application SAP Mobile Secure, the re-branded SAP Afaria. By exploiting this vulnerability, a malicious non-privileged application may produce a Denial of Service of application, leading to a direct impact on availability for end users.
This Android application is the re-branded well-
known SAP Afaria android client. It is the mobile client for SAP Afaria Server 7 which provides companies the opportunity to manage mobile devices landscapes and simplify the deployment and maintenance of smartphones and tablets. This software is an MDM.
The security bug resides in one broadcast receiver of the SAP Mobile Secure application. It was found by Onapsis researcher Yvan Genuer, and its exploitation works as follows. A malicious actor could forge a permissionless application, which once installed into an end-user device, can crash (stop) the SAP Mobile Secure application without any other user interaction. This results in a lack of management and control that the SAP Mobile Secure provides to the mobile and to the MDM administrator, since its agent is not working. The mobile user would not detect the situation unless he/she is familiar with this client software activity signs.
We strongly recommend patching each mobile system as the SAP security note recommends. The latest update for this client is version 6.60.19942.0 available in the Google Play store. Since this is a mobile SAP app, client side, it cannot be verified by our OSP solution.
Hot News and High Priority Notes
Among the most critical issued by SAP this month there are one Hot News and five High Priority security notes. The Hot News for November is the note #2681280 for HANA Streaming Analytics because of a highly scored security vulnerability (CVSS v3 9.9/10) in a third-party library it uses. This is the Spring Framework Library that has remote code execution vulnerabilities and affects not only this SAP product but others. It’s advised to follow the security note to apply the appropriate support package if you use the affected in your HANA landscape.
In addition to the already detailed High Priority notes, SAP issued another three ones as follows. The SAP Security Note #2701410 is for a Zip Slip vulnerability found in the SAP Disclosure Management product. This vulnerability consists of a fail in the location where the files are written when decompressed. It is a widespread vulnerability because it is originated in many commonly used libraries. This vulnerability can be exploited when a malicious archive is processed by a vulnerable decompressing extraction code. With it, an attacker may delete or overwrite data, target remote files he can execute or read the content of arbitrary files. The patch prevents further uploads of specially crafted compressed files.
Like with the note #2392860 from the past month, the note #2693083 deletes the same reserved transaction code from another standard SAP role. That transaction code can be abused by someone with development privileges and having the possibility to get it transported to a production system.
The last High Priority tagged note is a re-released one, #2699726, about Missing Network Isolation in Gardener, which brings an updated solution for this security issue advising to update to Gardener to release 0.12.4 or higher.
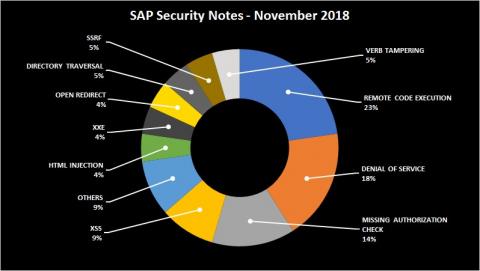
Finally, here’s a summary of the type of bugs SAP patched this month through its security notes:
This month SAP recognized Onapsis, through two researchers from our Research Labs, Yvan Genuer and Gaston Traberg, who have helped SAP to improve the security and integrity of their customers’ IT systems. As we regularly do at Onapsis, we will continue to publish our SAP Security Notes Patch Day analysis blogs every Patch Tuesday and work to update the Onapsis Security Platform to incorporate these newly published vulnerabilities. This will allow our customers to check whether their systems are up to date with the latest SAP Security Notes and will ensure that those systems are configured with the appropriate level of security to meet their audit and compliance requirements.
Please follow our ERP security blog or follow us on Twitter for more information about the latest SAP security issues.
