SAP Security Notes: Looking Back at 2019 and Forward to 2020
“After the Match is before the Match…!” – Sepp Herberger, Well-known German Soccer Manager
It was in 1954 after the quarter-final of the soccer world championships, when Germany’s team manager, Sepp Herberger, said these words. Two matches later, Germany unexpectedly won the World Cup. With his simple statement, he tried to explain that you can never rest on your success and efforts of the past—the next match will always need your full attention and 100% preparation.
The same rule applies to the constant new challenges posed by cyberattacks, with only one exception: you might have won all the matches before, but if you lose the next match, it could be your last one!
Reviewing The Last Match
When looking back to 2019, 10KBLAZE demonstrated that we are still a far way from always patched and up-to-date SAP environments. Although configuration instructions for covering the vulnerability had already been provided by SAP several years ago, an estimated 9 out of 10 SAP customers were still open to an attack due to missing configurations. But why hadn’t businesses patched this even after so much time had passed? Well, the reason is that the corresponding instructions involve the maintenance of customer-specific Access Control Lists, a manual configuration step that could never be covered by a follow-up support package or kernel patch.
So, what are the lessons learned from 10KBLAZE?
- Not every correction instruction can be covered by a follow-up support package or kernel patch
- The criticality of a vulnerability might increase over time (e.g. if the corresponding exploits are published)
In April 2019, the Onapsis Research Labs reported a serious vulnerability in SAP Diagnostics Agent to Walldorf. SAP Solution Manager (SolMan) has a basic functionality to execute some specially crafted and limited commands on the agents through a specific SolMan component. These commands are checked against a whitelist to prevent arbitrary command executions. The Onapsis Research Labs has previously found a bypass on one of the allowed commands to execute any other operating system command as the SolMan Admin user—on any of the connected SAP systems! The first patch for this vulnerability was released in July (SAP Security Note #2808158). The review of the published solution through our research team resulted in two updates (SAP Security Note #2823733 in September and SAP Security Note #2839864 in November). The first update covers additional operating systems that were missing in the original patch and the second update considers further predefined whitelisted commands that could be exploited to execute arbitrary commands on a connected satellite system. Because of its large attack vector and the fact that SAP Diagnostics Agent is distributed across the complete SAP landscape, the vulnerability was rated with a CVSS of 9.1. There are two things to keep in mind:
- Pay additional attention to your technical key components (or referring to the introductory metaphor: “your key players”)
- Teamwork is a crucial factor in defending cyberattacks:
- Onapsis(Research & Report vulnerability) > SAP(Patch vulnerability) > Customer(Apply Patch)
A constant companion of the monthly SAP Patch Days in 2019 was SAP Security Note #2622660 that informs customers about the most recent Google Chromium version supported by SAP Business Client. A review of the Note’s history shows that the CVSS rating of the patched vulnerabilities varies between 8.8 and 9.8. This should remind everyone that there are also 3rd party products involved in the “match” that need extra attention—and while new Chromium versions are covered by SAP Business Client updates, fixes for other external products might not be included in SAP patches.
- Constantly check the product specific channels of your 3rd party products for important security updates
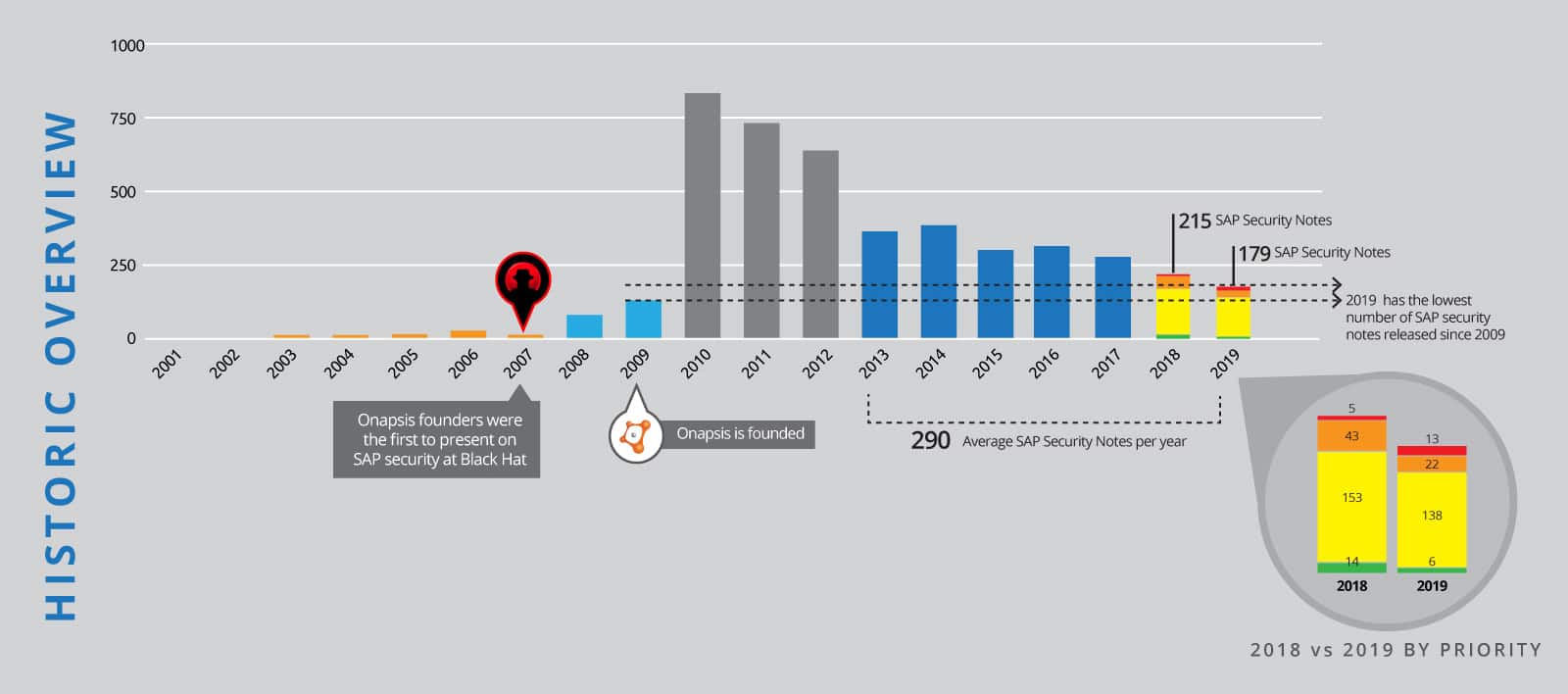
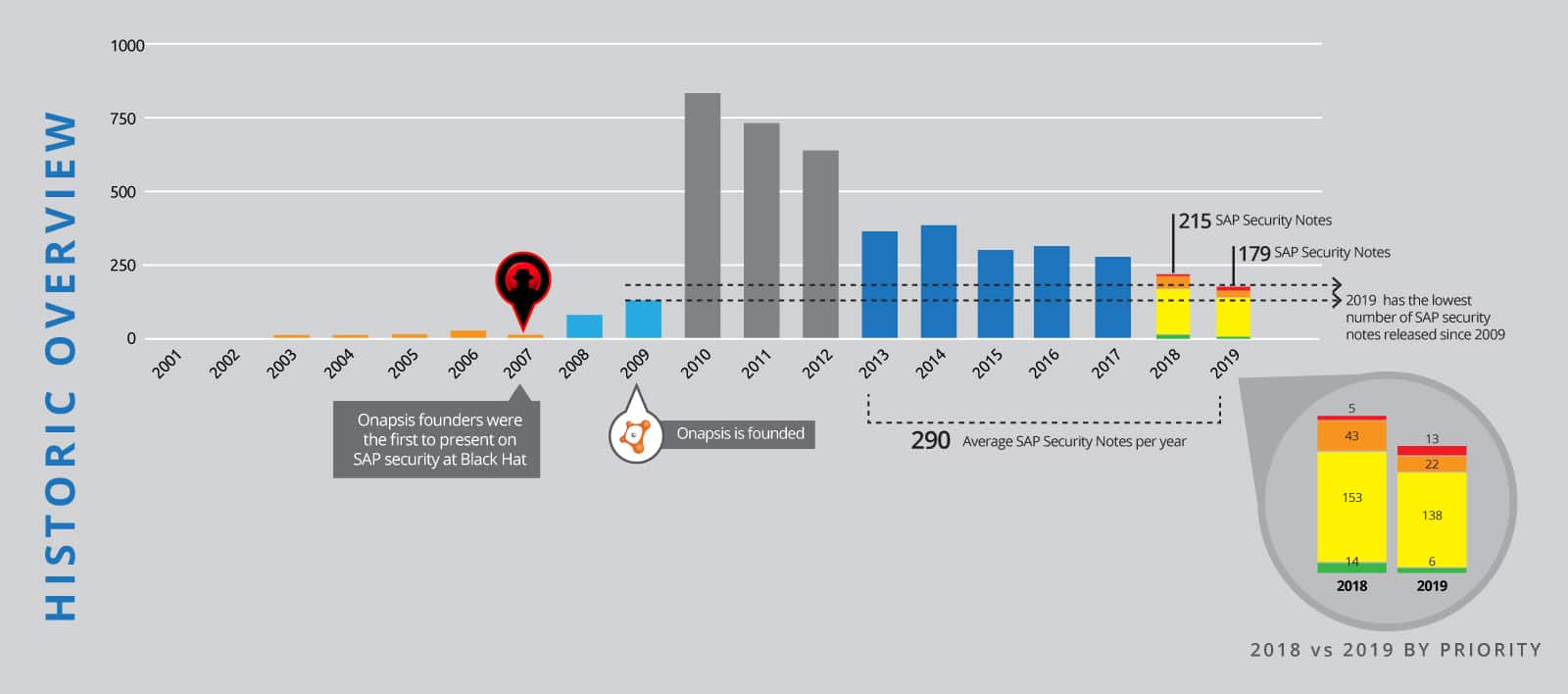
2019 in Numbers
179 SAP Security Notes released in 2019 represents a decrease of 17% compared to the 215 Notes in 2018. This marginally lower rate than last year is mainly a result of the trend to collect multiple vulnerabilities in one security note. The number of critical notes declined significantly by 27% (35 in 2019 and 48 in 2018). Interestingly, 13 of the 35 critical notes in 2019 are HotNews notes, which means an increase of 160% for the most critical note priority, compared to 2018.
4 of these 13 HotNews notes and 5 of the 22 High Priority notes were initiated by vulnerabilities, found by the Onapsis Research Labs. In total, 27 notes were published that fix vulnerabilities detected by Onapsis. This means that 26% of critical notes and 15% of ALL published SAP Security Notes in 2019 are the result of Onapsis’s continuous efforts to secure SAP systems against malicious activities!
The three most common vulnerabilities of the two last years have even expanded their top position. Once again, Missing Authority Check is the most common type, with 27% of the published notes, leaving Cross-Site Scripting (XSS) vulnerabilities in second place with 20%. Information Disclosure is in third place with 16%, followed far behind by Cross-Site Request Forgery bugs at 4%.

Looking at the Next Match
There is no doubt that ERP systems will increasingly become a preferred target of cyberattacks. SAP and Onapsis have taken multiple measures so that customers are best prepared for the challenges of 2020.
In June 2019, SAP started to deliver fixes for critical vulnerabilities (priorities HotNews and High) for support packages shipped within the last 24 months (previously within the last 18 months). This allows more customers who are not always able to upgrade to the most recent support packages to fix critical vulnerabilities.
An even bigger milestone is the strict support of digitally signed SAP Security Notes. Starting with 2020, transaction SNOTE only supports the download of digitally signed SAP Security Notes. This is a crucial improvement as the update process itself was a potential attack target in the past as the integrity of the downloaded configurations could not be guaranteed. For further information, check out our blog post Handling of Digitally Signed Notes.
As in the years before, Onapsis will continue in 2020 with its monthly blog post and webinar after each SAP Patch Day, providing every SAP customer valuable insights and backgrounds about the newly released SAP Security Notes.
With the acquisition of the German SAP security specialist Virtual Forge, Onapsis now offers one single platform for Segregation of Duties, custom code analysis, vulnerability assessments, secure change management, compliance automation and continuous monitoring. Onapsis customer Mario Chiock, Schlumberger Fellow and CISO Emeritus outlines the advantages of the acquisition like this:
“…With this acquisition, we and all SAP customers will now have a one-stop shop for SAP cybersecurity needs, reducing resources, time and cost; consolidating reporting and compliance demands.”
Could there be any better preparation for the upcoming match?
