SAP Security Patches June 2020: Two Critical Fixes Released for SAP Commerce

Highlights of the June SAP Security Notes analysis include:
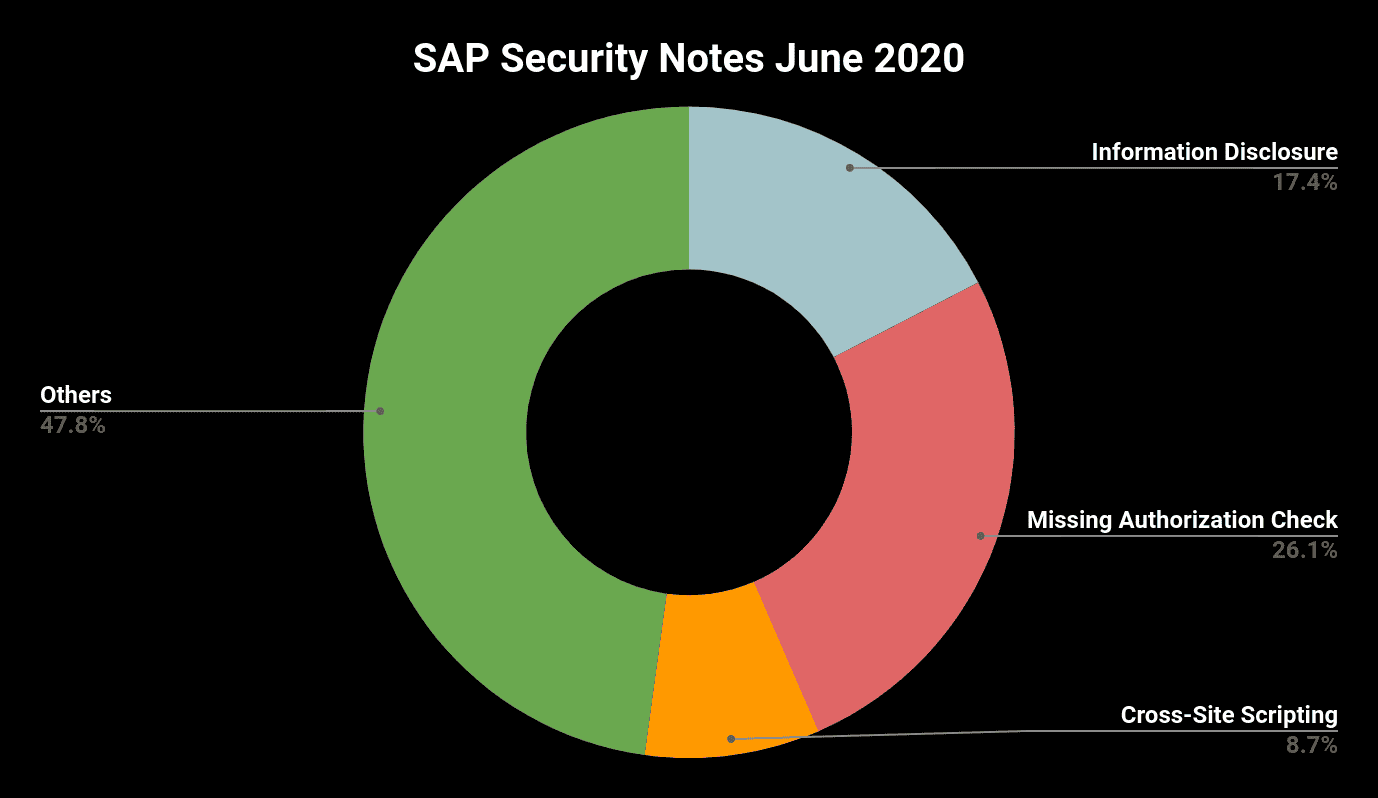
- June Summary—23 new and updated SAP security patches released including two HotNews Notes and five High Priority Notes
- SAP Commerce Affected Most—One HotNews fix and one High Priority fix released
- Onapsis Research Labs Collaboration—Our team was involved in fixing six vulnerabilities covered by four Security Notes, including 3 critical ones
SAP released 23 new or updated Security Notes this month. Of these, seven are critical fixes that fall in line with 2020’s current monthly average and is a significant drop from the 13 critical fixes in May. Additional good news is that five of the critical vulnerabilities can easily be fixed by simply applying the corresponding patches. One application that is suddenly getting a lot of attention is SAP Commerce with a couple of critical fixes added this month.
The Focus of June’s Patch Day: SAP Commerce
It has only been one month since SAP released a critical HotNews fix for SAP Commerce that patched a serious Missing XML validation vulnerability. The new issue was detected beforehand by the Onapsis Research Labs and helped SAP close another two critical vulnerabilities:
SAP Security Note #2918924, with CVSS of 9.8, addresses hard-coded user credentials in SAP Commerce and SAP Commerce Data Hub. This problem can be found in many software products because the products use some built-in accounts with publicly known passwords and do not force the administrators to change these passwords during or after installing the application. For example, every SAP Basis person knows the owners of “6071992” or “admin” passwords. SAP has now solved the problem for SAP Commerce and SAP Commerce Data Hub. After applying the patch, a new installation of SAP Commerce will only activate the built-in “admin” account. The installer is forced to maintain an initial password for that account. Other built-in users are still created during installation, but they are inactive until an individual password is set for these accounts. The later rule also applies to all built-in users of SAP Commerce Data Hub.
An important fact is that the patches only affect new installations of SAP Commerce (Data Hub). They do not remove default passwords from built-in accounts of existing installations. As one option to achieve this, the note proposes to re-initialize the SAP Commerce installation after applying the patch, an option that likely does not apply to most customers. Therefore, the note also provides a Disabling All Default Passwords for Users Guide to remove the default passwords from all built-in accounts.
SAP Security Note #2906366, rated with CVSS of 8.6, fixes an Information Disclosure vulnerability in SAP Commerce. The Onapsis Research Labs detected that under a specific configuration of some property values, a malicious user could exploit insecure features of the login-form to gain information that could be used for further exploits and attacks. Some of the required property values are even set by default.
Further Contributions from the Onapsis Research Labs
SAP Solution Manager (SolMan) is an integral part of every customer’s SAP landscape. As it is normally connected to all SAP systems via RFC and additionally communicates with different agents on these systems, it represents an attractive target for an attacker. For this reason, the Onapsis Research Labs has invested hundreds of hours in the last two years to dissect every technical component of SAP SolMan. This resulted in several critical fixes including a patch for a CVSS 10.0 vulnerability in March 2020 and also in a new High Priority fix on June’s patch day. SAP Security Note #2931391, rated with CVSS of 8.2, describes a Missing XML Validation vulnerability in Problem Context Manager. While an exploit has only a minor impact on the system’s confidentiality, it can have a serious impact on the system’s availability.
Two similar vulnerabilities were reported by our team that affect the Tracing Analysis in SAP SolMan. SAP fixed both of them with the Medium Priority Note #2915126. The note describes the risk of injecting additional content into trace files whose intention is to confuse readers and thus prevent them from identifying any suspicious processes.
Other Important SAP Security Notes in June
There was a second HotNews Note published on today’s patch day that affects SAP Liquidity Management for Banking. Due to a known vulnerability in Apache Tomcat, called “Ghostcat,” SAP strongly recommends disabling all ports using the Apache JServ Protocol (AJP Protocol). The issue is described in SAP Security Note #2928570. While the note points out the risk of a remote code execution, the description of the corresponding CVE-2020-1938 mentions that “AJP connections…can be exploited in ways that may be surprising.” The latter statement, together with the CVSS score of 9.8, should be reason enough to disable all AJP ports. If customers absolutely need the AJP protocol in their scenario, the note recommends to set the required secret attribute in the configuration of the AJP connector.
The set of critical fixes is completed by two High Priority Notes for SAP NetWeaver AS ABAP and one High Priority Note for SAP SuccessFactors:
SAP Security Note #2912939 fixes a vulnerability in the architecture of the batch input process allowing a malicious user to grab user credentials. Although the impact on the system’s integrity, confidentiality and availability is high, the CVSS score is “only” 7.6 as the attack complexity is high and it also needs admin privileges on MS SQL Server as well as batch input authorizations in SAP in order to successfully exploit the vulnerability.
The second High Priority Note for SAP NetWeaver AS ABAP, note #2734580, only contains some minor updates on the Correction Instruction and Correction Validity information and was originally released in May 2020. It fixes an Information Disclosure vulnerability that is rated with CVSS score of 7.4.
Last, but not least, SAP has released a High Priority fix for SAP SuccessFactors, an SAP component that was not represented at all on SAP Patch Days for years now, since it is a cloud-based solution. SAP Security Note #2933282 fixes a Missing Authorization vulnerability in SAP SuccessFactors Recruiting, leading to an escalation of privileges. Without the fix, users can get admin permissions allowing them to read and modify any application-related data. It is important to mention that customers need to apply manual changes in order to be protected.
Summary & Conclusions
With seven critical SAP Security Notes and 23 notes in total, the numbers of patches issued in June nearly reflect the monthly average of 2020. We eagerly await the further development of the note numbers in the second half of 2020. Extrapolating the current averages would lead to more than 70 critical notes, and more than 240 notes in total. This would mark a turning point for the continuously decreasing numbers of the last 13 years. The good news is that SAP applications become more and more secure with every single fix, and the other good news is that companies like Onapsis are supporting SAP in achieving best possible protection against all kinds of malicious activities. This month, Onapsis helped SAP in fixing three critical vulnerabilities, and four vulnerabilities in total.
As always, the Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.