SAP Security Patch Day July 2020: Critical Update Required for RECON Vulnerability
Highlights of July SAP Security Notes analysis include:
- July Summary—20 new and updated SAP security patches released including two HotNews Notes and two High Priority Notes
- RECON—New CVSS Score of 10.0 vulnerability, detected by Onapsis Research Labs, requires urgent patch of SAP NetWeaver AS Java
- Onapsis Research Labs Collaboration—Our team was involved in fixing five vulnerabilities covered by four Security Notes
SAP has released 20 new or updated Security Notes on its July patch day. While the number of critical notes is very moderate compared to the last patch days with “only” two HotNews notes and two High Priority notes, it is nevertheless a patch day that requires maximum attention from all SAP customers. SAP has published patches for the extremely critical RECON vulnerability (CVSS Score of 10.0) that affects all SAP applications running on SAP NetWeaver AS Java and strongly recommends immediate patching. In addition to the RECON vulnerability that was detected by Onapsis researcher Pablo Artuso, our research team contributed in solving four more threats.
In Focus: Protecting Your Systems From the Critical RECON Vulnerability
In May 2020, the Onapsis Research Labs detected an extremely serious vulnerability that affects all SAP applications running on SAP NetWeaver AS Java. Due to its criticality and thanks to the fast reaction of the SAP Security Response Team after Onapsis reported the flaw, SAP fixed it within only a few weeks. SAP Security Note #2934135, tagged with the highest possible CVSS Score of 10.0, was published in the SAP July Security Notes and provides the corresponding patch.
Due to the seriousness of the RECON vulnerability, the U.S. Department of Homeland Security (DHS) has issued US-CERT Alert, AA20-195A, in coordination with BSI CERT-Bund, followed by other global organizations providing warnings about potential threats associated with this vulnerability.
What Makes the RECON Vulnerability So Dangerous?
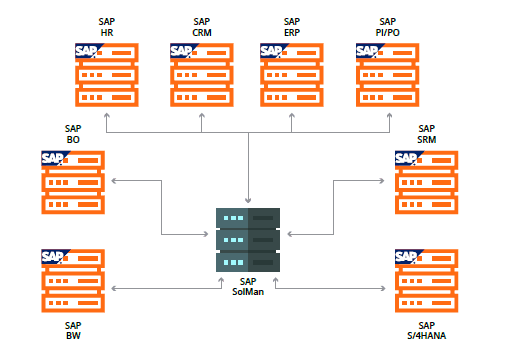
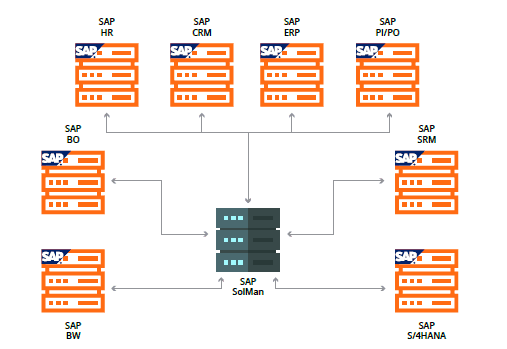
The RECON vulnerability affects a core component that is included in the SAP Java NetWeaver layer. It can be exploited by remote unauthenticated attackers and therefore all systems exposed to untrusted networks such as the Internet represent a potential attack target. The list of directly affected SAP applications is quite large:
- SAP Enterprise Resource Planning (ERP)
- SAP Supply Chain Management (SCM)
- SAP CRM (Java Stack)
- SAP Enterprise Portal
- SAP HR Portal
- SAP Solution Manager (SolMan) 7.2
- SAP Landscape Management (SAP LaMa)
- SAP Process Integration/Orchestration (SAP PI/PO)
- SAP Supplier Relationship Management (SRM)
- SAP NetWeaver Mobile Infrastructure (MI)
- SAP NetWeaver Development Infrastructure (NWDI)
- SAP NetWeaver Composition Environment (CE)
- Others
With SAP NetWeaver Java being a fundamental base layer for several SAP products, the specific impact would vary depending on the affected system. In particular, there are different SAP solutions running on top of NetWeaver Java which share a common particularity: they are hyperconnected through APIs and interfaces. In other words, these applications are attached to other systems, both internal and external, usually leveraging high-privileged trust relationships.
The way SAP applications are opened to the internet in the form of SAP Enterprise Portals, combined with integration technologies such as SAP SolMan or SAP Process Integration, creates an environment in which the exploitation of a vulnerability with a CVSS Score of 10.0 could ultimately lead to business data and PII being compromised.
The following sections will discuss in more detail some examples of widely-used SAP applications that share this pattern of API-based hyperconnectivity and are affected by this vulnerability.
SAP Enterprise Portals
SAP Enterprise Portals provide an integrated entry point to HR processes, financial information and supply chain management processes. Attackers being able to compromise these systems can ultimately cause a significant impact to organizations not only from a pure data breach and risk perspective, but as we are talking about business processes, they are also subject to compliance and regulatory requirements.
SAP Process Integration
The SAP Process Integration (PI) module is a part of the SAP NetWeaver platform that facilitates the communication and integration of business processes, with both SAP and non-SAP systems. It provides a single point of interaction to exchange information between the different components such as Sales & Distribution (SD), Finance & Cost Controlling (FICO), Extended Warehouse Management (EWM) and Customer Relationship Management (CRM), among others.
In spite of applying a secure configuration for the SAP PI module, an attacker could acquire high privileges acquired by exploiting the RECON vulnerability to display, change or delete sensitive data from any of the modules connected to the SAP PI—disrupting critical integrations with strategic business partners and essential processes. Given that the attacker could get administrator privileges in the SAP PI module, it could be strategically used as a pivot to get sensitive information from several modules such as the ones mentioned before.
SAP Solution Manager
SAP SolMan aims to centralize the management of all SAP and non-SAP systems that are within an organization’s landscape. As an administration solution, it performs actions such as implementation, support, monitoring and maintenance of the SAP enterprise applications and systems.
If an attacker is able to compromise SolMan, they will be able to abuse established trust relationships and pivot to any satellite system. Trusted relationships between SolMan and its connected systems are commonly configured to be highly privileged, becoming an interesting vector from the attacker’s point of view to gain further access to business data stored in satellite systems.
Business Impact of Potential Exploit
Once a system is compromised, the possible impact is almost unlimited. Among other things, attackers can create a new user with administrative privileges, allowing them to manage (read/modify/delete) every record/file/report in the system. No need to mention the possible resulting impact on the system’s confidentiality, integrity and availability.
Because of the type of unrestricted access an attacker would obtain by exploiting unpatched systems, this vulnerability also may constitute a deficiency in an enterprise’s IT controls for regulatory mandates—potentially impacting financial (Sarbanes-Oxley) and privacy (GDPR) compliance.
Exploitation of the vulnerability allows an attacker to perform several malicious activities, including:
- Steal personal identifiable information (PII) from employees, customers and suppliers
- Read, modify or delete financial records
- Change banking details (account number, IBAN number, etc.)
- Administer purchasing processes
- Disrupt the operation of the system by corrupting data or shutting it down completely
- Perform unrestricted actions through operating system command execution
- Delete or modify traces, logs and other files
The business impact of a potential exploit targeting RECON could be financial loss, compliance violations and reputation damage for the organization experiencing a cyber attack.
Given the enormous impact on thousands of SAP applications, Onapsis strongly recommends to apply the provided patch. As a workaround, customers can disable the affected Java application if it is not needed. A detailed description of how to disable the vulnerable application can be found in SAP Note #2939665, released by SAP. For more details on the RECON vulnerability and the impact of a potential exploit on SAP systems, read the Onapsis RECON Vulnerability Threat Report.
Additionally, Onapsis has scheduled webinars with live Q&A on the RECON vulnerabilities, register to attend here:
Additional Contribution From the Onapsis Research Labs
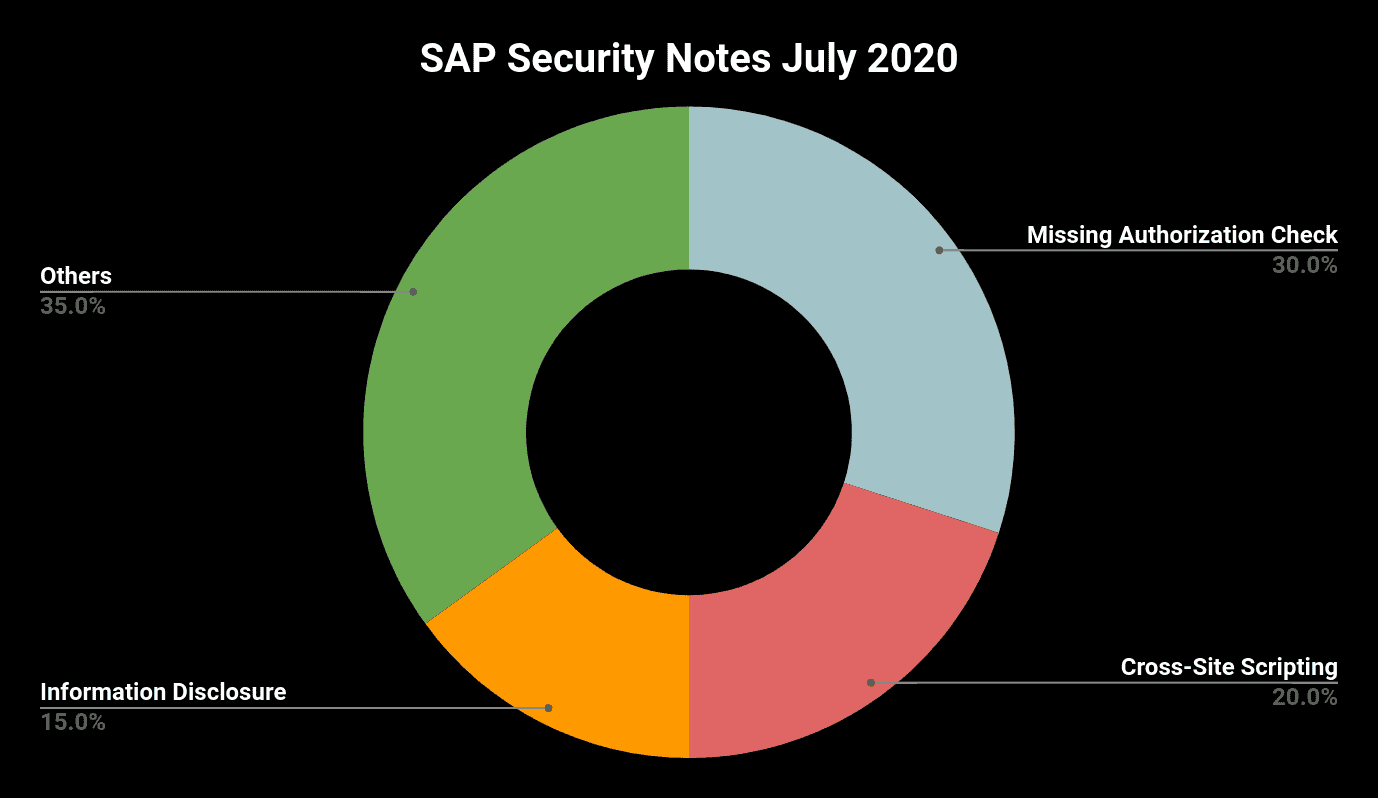
SAP has solved four Cross-Site Scripting vulnerabilities in SAP BusinessObjects on July’s patch day. One of these vulnerabilities was reported by Onapsis Research Labs and patched with SAP Security Note #2849967, tagged with CVSS Score of 6.1. This vulnerability is caused by an insufficient encoding of user controlled inputs.
SAP Security Note #2896025 describes a Server-Site Request Forgery vulnerability in a SAP NetWeaver AS Java service that allows an attacker to target internal systems behind firewalls that are normally inaccessible from the external network by sending special crafted requests. Possible impacts range from information gathering for further attacks to the bypass of firewalls to force the vulnerable server to perform malicious requests. The CVSS Score of 5.8 reflects the fact that an attack is not very complex and can be started remotely while there is no need for privileges or user interaction.
The Onapsis Research Labs also detected an Information Disclosure vulnerability in the search functionality of transaction AL11 on SAP NetWeaver AS ABAP, allowing an administrative user to detect and download files that are actually protected against access. SAP Security Note #2927373, tagged with CVSS Score of 2.7, provides the corresponding patch. As an exploit of this vulnerability requires administrative privileges and because of its low impact, the note is categorized with Low Priority.
Other Important SAP Security Notes in July
The second HotNews Note is the recurring SAP Security Note #2622660, providing the newest patch for SAP Business Client and including the latest supported version of Google Chromium (Chromium 83.0.4103.97). Compared to the last update of SAP Business Client, the new included Chromium version contains 43 fixes in total with a highest CVSS Score of 9.6.
The two High Priority Notes fix Information Disclosure vulnerabilities in SAP NetWeaver AS Java and SAP NetWeaver AS ABAP.
SAP Security Note #2932473, tagged with CVSS Score of 7.7, fixes a bug in the SAP XML Toolkit for Java that allows attackers to access arbitrary files which would otherwise be restricted. Such information can be used afterwards to start further exploits.
SAP Security Note #2734580, tagged with CVSS Score of 7.4, is the second update on a note that was initially released on SAP’s May Patch Day. An additional note was added to the Prerequisite section.
Summary & Conclusions
With only four critical Security Notes of 20 notes in total, SAP’s July patch day seems to be one of the calmer patch days. However, with the publication of the RECON vulnerability, this patch month is one of the most critical of the year. For the second time in 2020, Onapsis helped SAP in patching a CVSS Score of 10.0 vulnerability.
The RECON vulnerability demonstrates once more that it requires the effort of all members of the SAP community in order to defend serious cyberattacks—SAP partners like Onapsis that continuously searches for unknown vulnerabilities, SAP to fix reported threats, and last but not least every SAP customer who should finally implement the provided patch as soon as possible.
As always, the Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
Using the Assess capabilities of The Onapsis Platform, Onapsis customers can automatically run a full assessment of their SAP landscape and analyze whether the RECON vulnerability is present in their SAP systems to streamline remediation and mitigate the risk.
Onapsis customers using the Defend capabilities of The Onapsis Platform have a detection rule in place to continuously monitor for malicious activity and receive alarms to prevent attacks abusing the RECON vulnerability.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.