SAP Security Patch Day January 2021: Two Critical Patches for SAP Business Warehouse Released

Highlights of January SAP Security Notes analysis include:
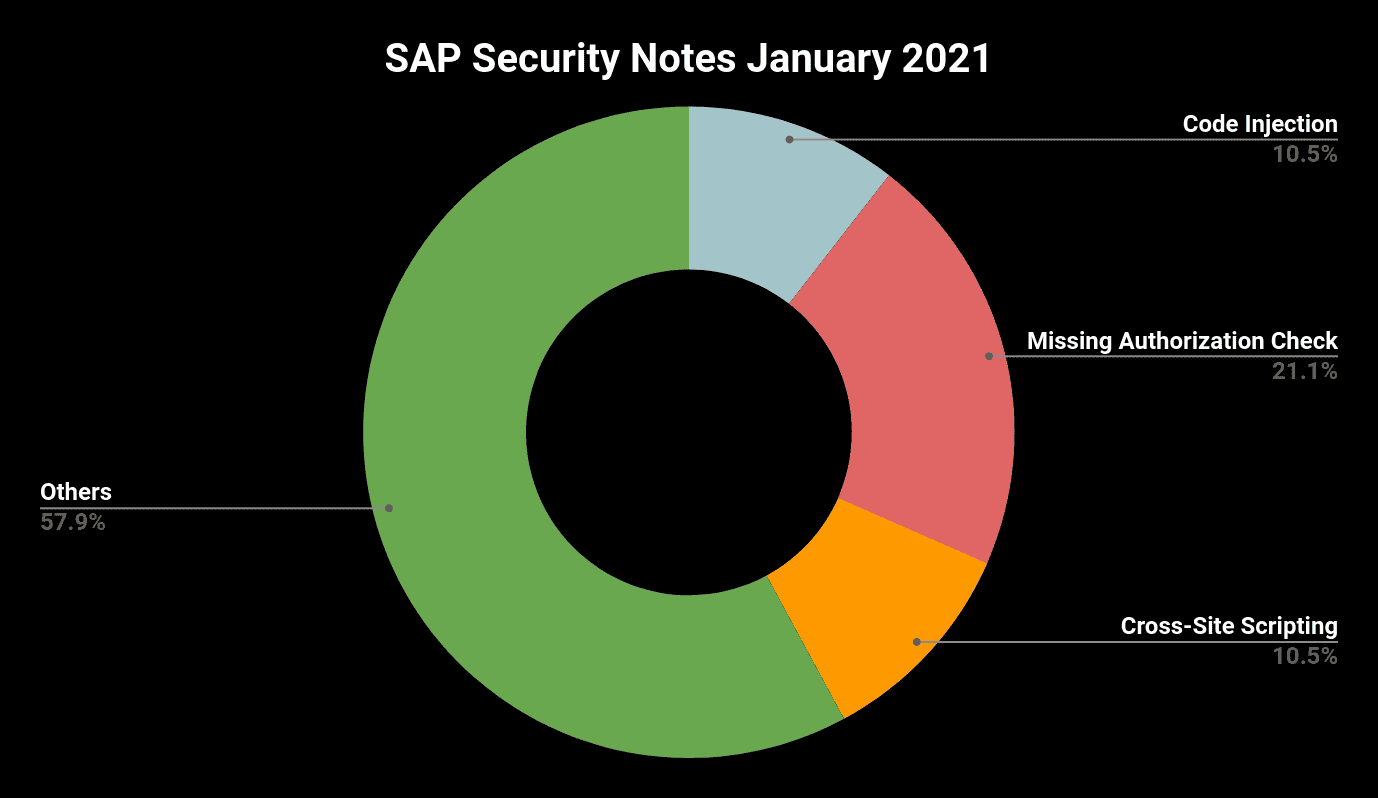
- January Summary—19 new and updated SAP security patches released, including five HotNews Notes and two High Priority notes
- Serious Vulnerabilities in SAP Business Warehouse (BW) and SAP BW/4HANA—Code Injection vulnerability exposes both applications at risk
The new SAP Security year has started with 19 new and updated SAP Security Notes. This number includes five HotNews notes and two High Priority notes.
At first glance, the number of five HotNews notes should cause concern. But a deeper analysis of these notes shows that HotNews note #2622660 is the well-known recurring Chromium Update for SAP Business Client. Looking into the note’s details, one can see that the vulnerabilities fixed with the newest Chromium update have a maximum CVSS score of 7.5. Nevertheless, this means that we have to deal with a defacto High Priority patch here, and thus applying this new update is strongly recommended.
HotNews note #2979062, tagged with CVSS score of 9.1, was initially released on SAP’s November Patch Day. SAP has extended the note and now provides patches for additional support packages. Checking the release dates of the affected support packages, one can recognize that they are out of maintenance with regard to SAP’s 24 months rule. Fortunately, SAP does not always insist on this rule, and thus, more SAP customers can benefit from an automatic patch for the described critical Privilege Escalation vulnerability in SAP NetWeaver Application Server for Java.
The same applies to HotNews Note #2983367, tagged with CVSS score of 9.1 and initially released on SAP’s December Patch Day. Following SAP, they “…enhanced the validity for all covered codelines to the lowest possible SP-level.”
In Focus: SAP Business Warehouse and SAP BW/4HANA
The two new HotNews notes of SAP’s January Patch Day, both tagged with a CVSS score of 9.9, fix critical issues in SAP Business Warehouse (SAP BW) and SAP BW/4HANA.
SAP Security Note #2999854 affects both of the aforementioned applications and fixes a dangerous Code Injection vulnerability. It patches a typical source for this kind of vulnerability. An insufficient input validation could allow a low privileged user to inject malicious code that is stored persistently as a report. This report could be executed afterward, and thus, could potentially lead to scenarios with a high negative impact on the confidentiality, integrity and availability of the affected system (and maybe also of connected systems). Fortunately, the provided patch can be applied automatically via transaction SNOTE and does not require any manual pre or post activities.
The second new HotNews note, SAP Security Note #2986980, only affects SAP BW. It patches a SQL Injection vulnerability, tagged with CVSS score of 9.9, and a Missing Authorization Check vulnerability, tagged with CVSS score of 6.5. Both vulnerabilities were found in the Database Interface of SAP BW. An improper sanitization of provided SQL commands allowed an attacker to execute arbitrary SQL commands on the database which could lead to a full compromise of the affected system.
Only the fact that it needs at least minimum privileges to start the attack prevented this vulnerability, as well as the vulnerability that was fixed with SAP Security Note #2999854, from becoming the first CVSS score of 10 in 2021.
The Missing Authorization Check vulnerability that was fixed with note #2986980 could lead to an escalation of privileges allowing an attacker to read out any database table. SAP has solved the issue by just disabling the function module. Attention: This will cause a dump in any application that calls this function module! So, it is highly recommended to check your custom code before applying the patch. If the function module is still in use, it is also strongly recommended to think about an alternative “as it must not be used anymore” and to implement the patch. Based on that statement, there is a high chance that the dangerous function module will be removed anyway with one of the next updates.
Other Critical SAP Security Notes in January
There were another two High Priority Notes released on SAP’s January Patch Day:
SAP Security Note #3001373, tagged with a CVSS score of 8.9, fixes an issue in the binding process of the Central Order service to a Cloud Foundry application that existed before December 4, 2020. This issue allowed unauthorized SAP employees to access the binding credentials of the service. It can be solved by simply deleting and recreating the service instance. If additional service keys were created for the service instance, they need to be recreated, in order to generate new credentials.
SAP Security Note #3000306, tagged with CVSS score of 7.5, patches a scenario in SAP NetWeaver AS and ABAP Platform that could lead to a Denial-of-Service experience for the users. Starting the demo examples that are embedded in ABAP Server’s and ABAP Platform’s ABAP Keyword Documentation via the web version allows an unauthenticated attacker to prevent legitimate users from accessing a service, either by crashing or flooding the service. The provided fix prevents the demo examples from being started in parallel.
Summary & Conclusions
With only 11 “really” new SAP Security Notes, the new year started with a relatively calm SAP Patch Day.
The most important lessons learned:
- If possible, it is an ideal time to ensure your support package level is still maintained by SAP by keeping in mind the 24 months rule.
- If a note does not provide a fix for your support package level, you should periodically check the security notes for updates. SAP often provides patches for lower package levels some weeks after the initial release of a Security Note.
- Code Injection, SQL Injection and OS Command Injection vulnerabilities are very critical in general as they often allow for the entire system to be compromised. For custom development, be aware of sufficient input validation and/or sanitization of code or commands that can be provided as user input!
As always, the Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about the latest SAP security issues and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Digest Onapsis Newsletter.