SAP Security Notes: February 2026 Patch Day

SAP Security Patch Day February 2026: Critical Code Injection in SAP CRM & S/4HANA
February Patch Day Highlights:
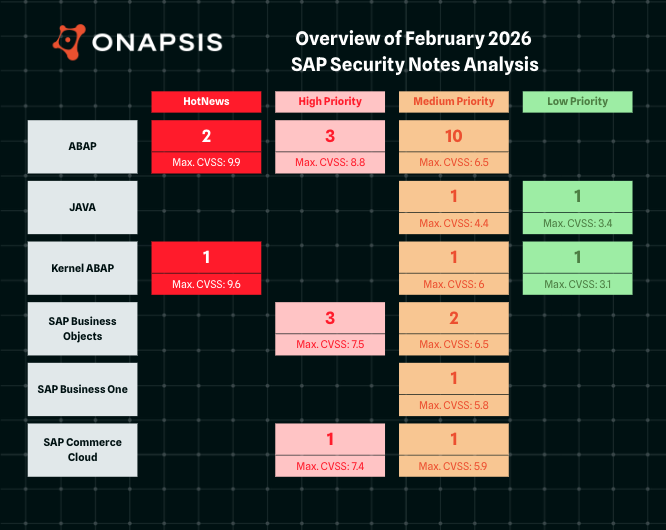
- February Summary – Twenty-nine new and updated SAP security patches released, including three HotNews Notes and seven High Priority Notes
- Critical Code Injection – Vulnerability in SAP CRM and S/4HANA allows execution of arbitrary SQL statements
- Onapsis Research Labs Contribution – Our team supported SAP in patching eight vulnerabilities, covered by seven SAP Security Notes
SAP has published twenty-nine new and updated SAP Security Notes in its February Patch Day, including three HotNews Notes and seven High Priority Notes. Seven of the twenty-seven new Security Notes were published in contribution with the Onapsis Research Labs.
The HotNews Notes in Detail
The Onapsis Research Labs (ORL) supported SAP in patching a critical Code Injection vulnerability in SAP CRM and SAP S/4HANA, tagged with the highest CVSS score in February.
Note #3697099: Code Injection in SAP CRM & S/4HANA (CVSS 9.9)
SAP Security Note #3697099, tagged with a CVSS score of 9.9, patches this vulnerability in the Scripting Editor of the application. It allows an authenticated attacker to execute unauthorized critical functionalities, including the execution of arbitrary SQL statements.
- Risk: A successful exploit can lead to a full compromise of the database with high impact on confidentiality, integrity, and availability of the application.
- Fix: SAP has added additional allowlist checks to the affected generic function module call with the patch. As a temporary workaround, the affected ICF service can be deactivated.
Note #3674774: Missing Authorization Check (CVSS 9.6)
SAP Security Note #3674774, tagged with a CVSS score of 9.6, patches a Missing Authorization Check vulnerability in SAP NetWeaver Application Server ABAP and ABAP Platform. Under certain circumstances, an authenticated, low-privileged user can perform background Remote Function Calls without the required S_RFC authorization.
- Risk: This vulnerability allows attackers to bypass authorization controls for background RFC processing. A successful exploit could allow unauthorized users to execute restricted functions, manipulate business data, or disrupt critical system operations.
- Fix: To patch the vulnerability, customers must implement a kernel update and set a profile parameter. Adjustments in user roles and UCON settings might be required to not interrupt business processes.
Note #3697979: Update to SAP Landscape Transformation (CVSS 9.1)
The third HotNews Note is SAP Security Note #3697979, tagged with a CVSS score of 9.1. The note was updated with the information that the vulnerability was reported externally. The note was initially released on SAP’s January Patch Day and patches the same Code Injection vulnerability in SAP Landscape Transformation that was also patched for SAP S/4HANA (Private Cloud and On-Premise) with HotNews Note #3694242. The vulnerable RFC Function Module was reported to SAP by the Onapsis Research Labs in December 2025.
The High Priority Notes in Detail
XML Signature Wrapping (CVSS 8.8)
SAP Security Note #3697567, tagged with a CVSS score of 8.8, patches an XML Signature Wrapping vulnerability in SAP NetWeaver AS ABAP and ABAP Platform. The vulnerability allows an authenticated attacker with normal privileges to obtain a valid signed message and send modified signed XML documents to the verifier.
- Impact: This may result in acceptance of tampered identity information, unauthorized access to sensitive user data and potential disruption of normal system usage.
- Workaround: There is a workaround available but it can not cover all usage scenarios of signed XML documents.
Information Disclosure in Solution Tools (CVSS 7.7)
SAP Security Note #3705882, tagged with a CVSS score of 7.7, addresses an RFC Module in the SAP Solution Tools Plug-In (ST-PI) that discloses sensitive information to unauthorized users. The information could be used in succeeding system attack attempts and is no longer exposed after implementing the patch.
Onapsis Research Labs Contributions
The Onapsis Research Labs (ORL) supported SAP in fixing two of the seven High Priority Notes:
DoS in Supply Chain Management (CVSS 7.7)
SAP Security Note #3703092, tagged with a CVSS score of 7.7, patches a Denial of Service vulnerability in SAP Supply Chain Management. Our team detected a remote-enabled Function Module that allows an authenticated attacker with regular user privileges and network access to control the number of loop executions. By calling this module repeatedly, it consumes excessive system resources, potentially rendering the system unavailable.
DoS in BusinessObjects BI Platform (CVSS 7.5)
Another Denial of Service vulnerability was detected by our ORL team in SAP BusinessObjects BI Platform. By sending specially crafted requests, unauthenticated attackers are able to crash and automatically restart the Content Management Server (CMS). Submitting these requests repeatedly, the attacker could induce a persistent service disruption, rendering the CMS completely unavailable. The vulnerability is tagged with a CVSS score of 7.5 and patched with SAP Security Note #3678282. As a temporary workaround, CORBA SSL can be implemented.
Other High Priority Notes
DoS in BusinessObjects BI (CVSS 7.5):
SAP Security Note #3654236, tagged with a CVSS score of 7.5, addresses another Denial of Service vulnerability in SAP BusinessObjects BI Platform. It allows an unauthenticated attacker to craft a specific network request to the trusted endpoint that breaks the authentication, which prevents the legitimate users from accessing the platform. The patch allows customers to configure the web application’s trusted endpoint with mutual TLS (mTLS) to only accept queries from trusted backend servers. As a temporary workaround, the landscape can be segregated into different network segments.
Race Condition in SAP Commerce Cloud (CVSS 7.4)
SAP Security Note #3692405, tagged with a CVSS score of 7.4, provides a patch for SAP Commerce Cloud that includes a version of the Eclipse Jersey library that is no longer vulnerable to the race condition tracked under CVE-2025-12383. Staying unpatched, an authenticated user could bypass SSL trust validation for outbound connections, leading to a high impact on confidentiality and integrity of the application.
Open Redirect in BusinessObjects BI (CVSS 7.3):
SAP Security Note #3674246, tagged with a CVSS score of 7.3, patches an Open Redirect vulnerability in SAP BusinessObjects Business Intelligence Platform. The vulnerability allows authenticated attackers to redirect victims to an attacker-controlled domain and subsequently download malicious content. The patch introduces server-side allowlisting to prevent any unvalidated redirects to third-party URLs.
Further Onapsis Contributions
In addition to the HotNews Note and the two High Priority Notes, the ORL team supported SAP in fixing another five vulnerabilities, covered by four SAP Security Notes.
Open Redirect in Business Server Pages (CVSS 6.1)
The ORL team identified an Open Redirect vulnerability in the TAF_APPLAUNCHER Business Server Pages Application that could be exploited to redirect users to attacker‑controlled sites, potentially exposing or altering sensitive information in the victim’s browser. SAP Security Note #3688319, tagged with a CVSS score of 6.1, patches the issue by introducing a security warning to users before any redirection to external URL. If Component Based Test Automation is not used, the affected TAF_APPLAUNCHER application can be deactivated.
Multiple Vulnerabilities in Document Management System (CVSS 6.1)
SAP Security Note #3678417 patches an Open Redirect vulnerability and a Cross-Site Scripting vulnerability in BSP Applications of SAP Document Management System, both tagged with a CVSS score of 6.1. The CVSS vector of the two vulnerabilities is identical and shows a low impact on the confidentiality and integrity of the application. The patch deprecates the vulnerable functions and URL parameters in the affected BSP application pages.
Information Disclosure in Commerce Cloud (CVSS 5.3)
An Information Disclosure vulnerability was detected by our team in SAP Commerce Cloud. The application exposes some API endpoints to unauthenticated users. On submit, these endpoints return sensitive information that is not intended to be publicly accessible via the front-end. The vulnerability is tagged with a CVSS score of 5.3 and patched with SAP Security Note #3687771.
Missing Authorization in Strategic Enterprise Management (CVSS 4.3)
SAP Security Note #3680390, tagged with a CVSS score of 4.3, patches a Missing Authorization Check vulnerability in SAP Strategic Enterprise Management. The vulnerability causes low impact on confidentiality by allowing authenticated attackers to access information that they are otherwise unauthorized to view.
Summary of February 2026 Security Notes
With twenty-nine Security Notes, including three HotNews Note and seven High Priority Notes, SAP’s February’s Patch Day is a very busy one. We are proud that our Onapsis Research Labs could contribute to this Patch Day by supporting SAP in patching eight vulnerabilities, including one tagged as HotNews and two tagged as High Priority Notes.
| SAP Note | Type | Description | Priority | CVSS |
| 3697099 | New | [CVE-2026-0488] Code Injection vulnerability in SAP CRM and SAP S/4HANA (Scripting Editor) CRM-IC-FRW | HotNews | 9.9 |
| 3674774 | New | [CVE-2026-0509] Missing Authorization check in SAP NetWeaver Application Server ABAP and ABAP Platform BC-MID-RFC | HotNews | 9.6 |
| 3697979 | Update | [CVE-2026-0491] Code Injection vulnerability in SAP Landscape Transformation CA-DT-ANA | HotNews | 9.1 |
| 3697567 | New | [CVE-2026-23687] XML Signature Wrapping in SAP NetWeaver AS ABAP and ABAP Platform BC-SEC-WSS | High | 8.8 |
| 3703092 | New | [CVE-2026-23689] Denial of service (DOS) in SAP Supply Chain Management SCM-APO-CA-COP | High | 7.7 |
| 3705882 | New | [CVE-2026-24322] Missing Authorization check in SAP Solution Tools Plug-In (ST-PI) SV-SMG-SDD | High | 7.7 |
| 3678282 | New | [CVE-2026-0485] Denial of service (DOS) vulnerability in SAP BusinessObjects BI Platform BI-BIP-SRV | High | 7.5 |
| 3654236 | New | [CVE-2026-0490] Denial of service (DOS) in SAP BusinessObjects BI Platform BI-BIP-SRV | High | 7.5 |
| 3692405 | New | [CVE-2025-12383] Race Condition in SAP Commerce Cloud CEC-SCC-PLA-PL | High | 7.4 |
| 3674246 | New | [CVE-2026-0508] Open Redirect vulnerability in SAP BusinessObjects Business Intelligence Platform BI-BIP-SEC | High | 7.3 |
| 3695912 | New | [CVE-2026-24324] Denial of service (DOS) vulnerability in SAP BusinessObjects Business Intelligence Platform (AdminTools) BI-BIP-SRV | Medium | 6.5 |
| 3672622 | New | [CVE-2026-0484] Missing Authorization check in SAP NetWeaver Application Server ABAP and SAP S/4HANA BC-DWB-CEX-CF | Medium | 6.5 |
| 3688319 | New | [CVE-2026-24328] Open Redirection vulnerability in Business Server Pages Application (TAF_APPLAUNCHER) SV-SMG-TWB-CBT | Medium | 6.1 |
| 3678417 | New | [CVE-2026-0505] Multiple vulnerabilities in BSP Applications of SAP Document Management System CA-DMS-OP | Medium | 6.1 |
| 3503138 | Update | [CVE-2025-0059] Information Disclosure vulnerability in SAP NetWeaver Application Server ABAP (applications based on SAP GUI for HTML) BC-FES-WGU | Medium | 6 |
| 3689543 | New | [CVE-2026-23684] Race condition vulnerability in SAP Commerce Cloud CEC-SCC-COM-BC-OCC | Medium | 5.9 |
| 3679346 | New | [CVE-2026-24319] Information Disclosure Vulnerability in SAP Business One (B1 Client Memory Dump Files) SBO-CRO-SEC | Medium | 5.8 |
| 3687771 | New | [CVE-2026-24321] Information Disclosure vulnerability in SAP Commerce Cloud CEC-SCC-COM-BC-OCC | Medium | 5.3 |
| 3710111 | New | [CVE-2026-24312] Missing authorization check in SAP Business Workflow BC-BMT-WFM | Medium | 5.2 |
| 3691645 | New | [CVE-2026-0486] Missing Authorization Check in ABAP based SAP systems SV-SMG-SDD | Medium | 5 |
| 3697256 | New | [CVE-2026-24325] Cross Site Scripting (XSS) vulnerability in SAP BusinessObjects Enterprise (Central Management Console) BI-BIP-CMC | Medium | 4.8 |
| 3687285 | New | [CVE-2026-23685] Insecure Deserialization vulnerability in SAP NetWeaver (JMS service) BC-JAS-JMS | Medium | 4.4 |
| 3680390 | New | [CVE-2026-24327] Missing Authorization Check in SAP Strategic Enterprise Management (Balanced Scorecard in BSP Application) FIN-SEM-CPM-BSC | Medium | 4.3 |
| 3678009 | New | [CVE-2026-24326] Missing authorization check in SAP S/4HANA Defense & Security (Disconnected Operations) IS-DFS-BIT | Medium | 4.3 |
| 3215823 | New | [CVE-2026-23688] Missing Authorization check in SAP Fiori App (Manage Service Entry Sheets – Lean Services) MM-PUR-SVC-SES | Medium | 4.3 |
| 3680416 | New | [CVE-2026-23681] Missing Authorization check in a function module in SAP Support Tools Plug-In SV-SMG-SDD | Medium | 4.3 |
| 3122486 | New | [CVE-2026-23683] Missing Authorization check in SAP Fiori App (Intercompany Balance Reconciliation) FI-LOC-FI-RU | Medium | 4.3 |
| 3673213 | New | [CVE-2026-23686] CRLF Injection vulnerability in SAP NetWeaver Application Server Java BC-MID-CON-JCO | Low | 3.4 |
| 3678313 | New | [CVE-2026-24320] Memory Corruption vulnerability in SAP NetWeaver and ABAP Platform (Application Server ABAP) BC-CST-IC | Low | 3.1 |
Next Steps
As always, the Onapsis Research Labs is already updating The Onapsis Platform to incorporate the newly published vulnerabilities into the product so that our customers can protect their businesses.
For more information about the latest SAP security issues, SAP patch day, the latest SAP security notes, and our continuous efforts to share knowledge with the security community, subscribe to our monthly Defender’s Monthly Newsletter, and visit our library of articles and resources.
