SAP Security Notes February 2017: Turning up the Volume
In this month’s SAP Security Notes, it’s noticeable that the priority of the majority of security notes are higher compared to previous month. This can be seen in the below graphic:
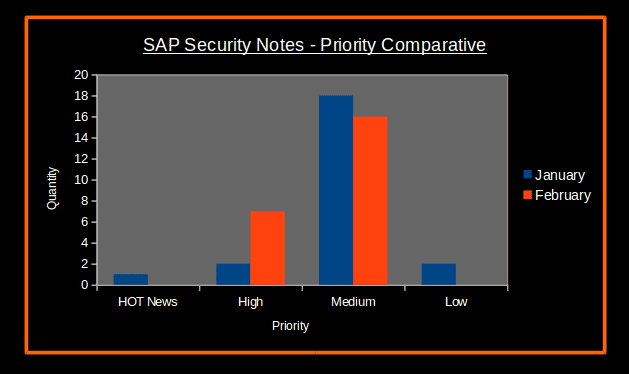
The number of SAP Security Notes each month was the same, but ‘high priority’ security notes were more than doubled this month (1 ‘hot news’ and 2 ‘high priority’ notes in January, versus 7 ‘high priority’ notes in February). There are a total of 23 SAP Security Notes published (15 published today) since the last Security Notes Tuesday in January. Regarding the CVSS scoring, the following Boxplot image shows that this month’s notes are more critical compared to last month’s. Although there is only one note reaching the maximum CVSS scoring of 8.5, the majority of notes had a CVSS score that fell between 6.1 and 8 (while last month the vast majority of notes fell between a 5.4 and 6.5):

High Priority SAP Security Notes
This month had a particularity regarding ‘High Priority’ SAP Security Notes. Almost all of these notes (except for just one) had properly been set with a CVSS version 3 scoring and vector. This is a good starting point when understanding the risk of each note in terms of impact on SAP Products.
- Missing Authorization Checks in SAP Netweaver Data Orchestration Engine (2408892): This note was reported by our Research Labs and it involves the accumulation of several authorization objects for different function groups that affect:
- NWAs 710: SP16 to SP21
- NWAs 711: SP12 to SP16
- NWAs 730: SP12 to SP16
- SUPDOE Add-On 731: SP01 to SP04
CVSS v3 Base Score: 8.5 / 10
- SAP Web IDE for SAP HANA: Unauthorized remote data tampering and DOS attack (2407694): This is a note to definitely take into account if you are using SAP HANA, as it fixes security bugs that would allow an attacker to create a new user to publish new packages, the creation of specially malicious packages, and two different denial of service attacks in Sinopia. CVSS v3 Base Score: 8.3 / 10
- Setup of Trusted RFC in GRC Access Control EAM (2413716): This note explains how to solve a possible problem in the way that access control to the Fire Fighter ID account was being done. CVSS v3 Base Score: 8.2 / 10
- Memory Corruption vulnerability in SAP 3D Visual Enterprise Author, Generator and Viewer (2391018): There was a security bug in SAP 3D Visual Enterprise Author Generator and Viewer through which an attacker was able to corrupt the memory and gain access to the SAP Server. CVSS v3 Base Score: 8.0 / 10
- Leveraging privileges by customer transaction code (2392860): If an incorrect profile authorization was made, the user that was assigned to it would have the ability to develop his/her own transaction and be able to execute it. This notes fixes that behavior. CVSS v3 Base Score: 8.0 / 10
- Denial of service (DOS) in “System Messages” area in DOE Administration Portal (2410061): The Administration Portal was vulnerable to a Denial of service attack when an attacker sends a custom value into the “System Messages” area; this would prevent legitimate users from properly using the component later. CVSS v3 Base Score: 7.7 / 10
- Code injection vulnerability in BC-SRV-KPR-DMS (2278931): The component BC-SRV-KPR-DMS was fixed in this note. If exploited, this vulnerability would allow a malicious user to define and execute code of the user’s choice, thus taking control of the system. CVSS v3 Base Score: not published.
- This month our researchers Pablo Artuso and Emiliano Fausto were acknowledged on the SAP Webpage as both reported high priority vulnerabilities this month. Our team is already in the process of updating the Onapsis Security Platform to incorporate these newly published vulnerabilities. This will allow you to check whether your SAP systems are up to date with the latest SAP Security Notes, and will ensure that those SAP systems are configured with the appropriate level of security to meet your audit and compliance requirements.

