SAP Security Breach Cited as a Major Factor in Company’s Bankruptcy

At the end of 2024 there were news reports of a company filing for bankruptcy due to a cyber security incident and other factors. News articles from sources such as Wall Street Journal, SC Group and SecureWorld all detail that the company attacked was brought down by ransomware that significantly disrupted operations. We learn the company is Stoli Group USA (“Stoli”), a privately held company, and because of the cybersecurity incident and other factors it filed for Chapter 11 bankruptcy in November of 2024.
More Information Surfaces About the Cyber Attack
The Onapsis Research Labs obtained court documents that provide additional details into what happened. The filings reveal that the cybersecurity incident was an “SAP Security Breach.”
“Due to SAP Security Breach”

Source: Case 24-80146-swe11 Doc 117 Filed 12/30/24
Other excerpts from the court filings, where SAP is mentioned as the ERP system being affected, provide further details about the negative impact of the ransomware and data breach attack:
“Cyber Attack Disclosure. As further explained in the Declaration of Chris Caldwell in Support of First Day Motions [Docket No. 11] (the “First Day Declaration”), the Debtors’ IT infrastructure suffered severe disruption in the wake of a data breach and ransomware attack in August 2024 (collectively, the “Cyber Attack”). The Cyber Attack caused substantial operational issues throughout all companies within the Stoli Group (as defined in the First Day Declaration), including the Debtors. Among other things, via the Cyber Attack, the entirety of the Debtors’ accounting and financial systems were hacked and encrypted in a form that the Debtors were unable to read or decipher. The Cyber Attack resulted in the Stoli Group’s enterprise resource planning (“ERP” or “SAP”) system being disabled and most of the Stoli Group’s internal processes (including accounting functions) being forced into a manual entry mode. As of the Petition Date and the filing of the Debtors’ Schedules and Statements, the Debtors’ accounting and financial systems have not been fully recovered and are not up and running as they ordinarily would be in the ordinary course of business.”
The impact of a cyber attack targeting SAP applications goes beyond the disruption of critical business processes such as manufacturing, logistics and sales. The court testimony also includes the following statement, highlighting that the SAP security breach also resulted in challenges for the victim organization to comply with financial reporting. While Stoli was a private company, this would certainly have even broader implications for publicly-traded businesses based on SOX requirements:
(3) the aforementioned severe operational disruption caused by a data breach and ransomware attack in August 2024 (including issues with compliance by the Debtors with the reporting requirements of the Lender)
Per the information in the filings, the company forecasts that the full recovery and restoration will take between 5 and 7 months:
“The Debtors are continuing to execute their plans to recover and restore the encrypted information to the format previously used by the Debtors, and the Debtors anticipate that these systems will be fully restored no earlier than in the first quarter of 2025. Thus, the Debtors provide this disclosure related to the Cyber Attack to note that the information provided herein and in the Debtors’ Statements and Schedules is being provided to the best of the Debtors’ abilities as of the Petition Date and without the Debtors accounting and financial systems having fully been restored following the Cyber Attack.”
The Evolution of SAP Ransomware Threats
SAP and Onapsis have been jointly and proactively alerting organizations of the increasing threat of ransomware attacks to unprotected SAP applications since 2001. Furthermore, last year the Onapsis Research Labs released new SAP threat intelligence in the CH4TTER report, further warning about threat actor behavior in this regard.
The findings pointed to a continued escalation in threats to SAP applications, for instance:
- 400% increase in ransomware incidents involving compromised SAP systems and data
- 490% increase in criminal conversations on SAP vulnerabilities and exploits
- 220% increase in active posts on discovery of SAP cloud-facing and web services
- 400% increase in the price of SAP remote code execution exploits
In an example from the report, a Russian-speaking user in a cyber criminal group was found looking for guidance on how to monetize an SAP compromise of four different companies after exploiting SAP application-level vulnerabilities such as RECON and in SAP Solution Manager.
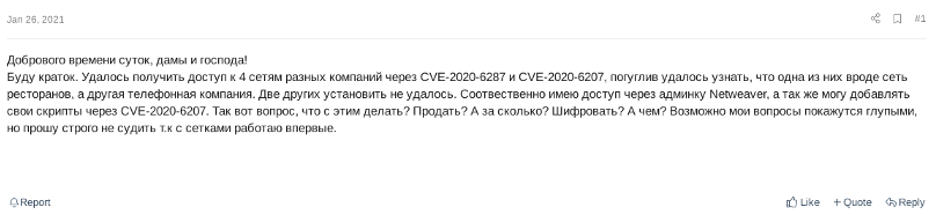
Source: CH4TTER Report
This translates (roughly) to:
| Good day, ladies and gentlemen!I’ll be brief. We managed to gain access to 4 networks of different companies through CVE-2020-6287 [RECON] and CVE-2020-6207 [SAP Solution Manager missing authentication], after googling I found out that one of them was like a restaurant chain, and the other was a telephone company[…] what to do about it? Sell? How much? Encrypt? […] |
How to Ensure Your SAP Applications Are Protected
The conclusion is clear: threat actors have the capabilities, knowledge and intent to compromise unsecured SAP applications. Furthermore, they have now realized that, given the mission-critical nature of SAP to most organizations and the significant financial impact of a sustained disruption in their SAP systems, ransomware attacks on SAP will yield high leverage in ransom negotiations with their victims.
The Onapsis Research Labs is continuing to investigate this incident. While there is still no additional technical information about the specific techniques, tools and procedures used by threat actors in this case, based on our SAP incident response experience and threat intelligence insights, we would like to provide guidance on actions all SAP customers can take to minimize the risk of successful SAP ransomware attacks.
Some of the most important recommendations:
- Scan SAP systems for all known SAP application-level vulnerabilities, such as missing SAP security patches/notes and insecure instance configurations.
- Analyze SAP systems for malicious or excessive SAP user authorizations.
- Assess SAP custom code created by developers or third parties, to identify potential vulnerabilities and backdoors.
- Monitor SAP systems for indicators of compromise resulting from the exploitation of vulnerabilities.
- Monitor SAP systems for suspicious user behavior, including both privileged and non-privileged users.
- Apply threat intelligence on new vulnerabilities to improve the security posture against advanced targeted attacks.
- Define comprehensive security baselines for systems and continuously monitor for compliance violations and remediate detected deviations.
- Ensure SAP applications are backed up periodically, and back ups are tested
- Review incident response processes and playbooks, ensuring SAP systems are included in the scope.
For more information, follow our posts, blogs, our advisories on SAP vulnerabilities, or contact us.

